Opera Software, the Norwegian company that makes the Opera browser was hacked on June 19th and released a statement a week later:


The hackers breached the company’s network and used one of its code-signing certificate (an older and expired one mind you) to digitally sign a piece of malware and package it as an update for the Opera browser.
While it is not entirely clear what happened, it would appear as though the bad guys went as far as pushing the update for a 36-minute period, meaning they had access to Opera’s infrastructure during that time.
The malicious file followed the same naming convention as the legitimate Opera auto update files but was much smaller:
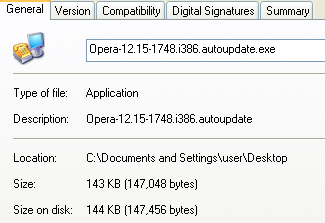
A number of Opera’s estimated 300 million users may have been infected with a nasty Trojan downloader.
Upon successful infection, the malicious file searches the hard drive for passwords stored in Internet Browsers as well as FTP clients.
In addition, after several minutes, the user’s computer may become locked up with Ransomware demanding $300:
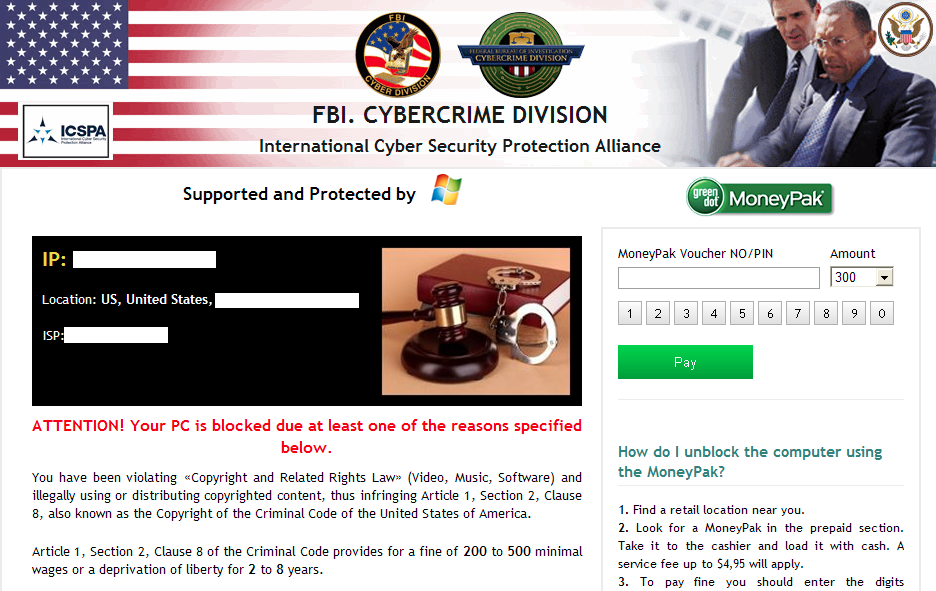
This attack and payload are possibly the most effective method to serve malware onto unsuspecting users who are naturally urged to update their software when an update is available. The fact that it came from a trusted authority (Opera itself) and was using a digital certificate makes it even trickier.
This incident should not discourage end-users to follow best practices by keeping their PCs up-to-date, but it does raise some questions. After all, it shows that we cannot completely trust files, even when they are coming from reputable vendors.
This is perhaps when defense in-depth shows its merits. The bad guys can fool one product but not all (or at least it is much more difficult). Having multiple layers of defense (antivirus, anti-malware, browser protection) can stop an attack at different stages before it succeeds.
While Opera Software coming forward with this information is a good thing, their statement’s title “Security breach stopped” does not quite add up since a breach did appear to happen and lead to at least one malicious file being pushed onto users. The other troubling thing is the lapse of time between the incident itself and the announcement (one week), which is long enough for malware to do its thing.
The only bright light to this story is that the file was detected by several antivirus vendors and also by our very own Malwarebytes Anti-Malware as Trojan.Downloader.szb the same day that it came out, keeping our users safe from this threat.









