Over the years, online privacy has not been spared very much with from Adware and Spyware that monitor your browsing habits to serve customized pop-ups or hijack your search results.
It got so bad that the Federal Trade Commission had to intervene due to the number of complaints.
Things have changed, but many of those same companies have regrouped under different names and operate a slightly different business model, still making money hand over fist.
Large corporations, like Google, have come under heavy fire with regard to data collection and privacy.
Recently, the European Union has come after Google with sanctions for breaching data protection laws. The search engine giant is known for having amassed one of the largest customer databases ever known with data such as full names, phone numbers, addresses, credit card numbers, search query logs, phone calls made, contact lists, etc.
It wouldn’t be fair to forget to mention Facebook, which has had its fair share of privacy blunders, something that cannot go unnoticed when you are the world’s largest social networking platform.
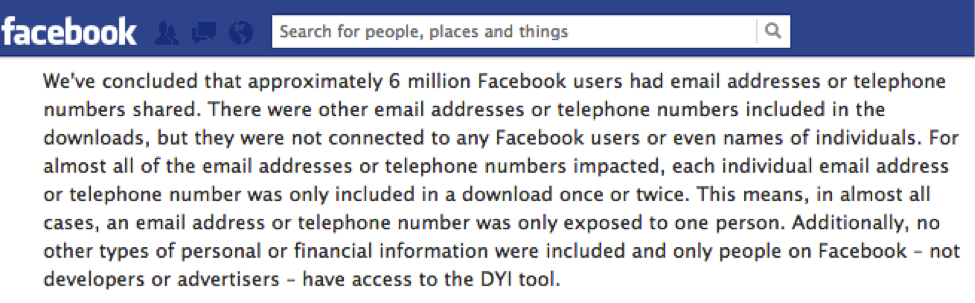
In fact, just last Friday, Facebook apologized to its users for a flaw in its system that allowed people to view private phone numbers and email addresses.
This technical glitch had been in existence for a year, and according to Facebook, six million users have been affected.
While some attempts have been made by software companies to come up with new privacy features in their products (e.g., Internet Explorer’s InPrivate browsing, Google Chrome’s Incognito mode), whatever hope was left may very well have been shattered with the recent NSA leaks about the PRISM surveillance program that revealed how the U.S.’s top Internet companies were turning over private user data to the government.
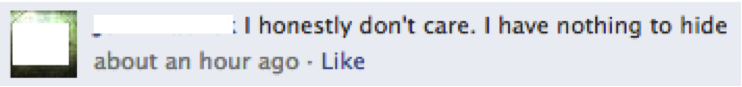
Whether data is being sent automatically (think apps that sync to the cloud) or driven by users (placing a phone call, uploading photos), the end result is that it’s all there somewhere being logged and stored. Some people argue that they have “nothing to hide,” that they’re not doing anything wrong and could not care less if their private information was accessed, especially if it helped the effort to track down terrorists.
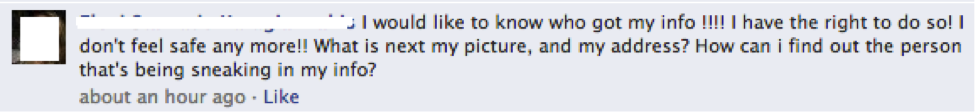
While there is no doubt that ready access to data is an invaluable asset for intelligence agencies, it is really important to remember that each individual has a fundamental right to privacy.
There is a paradox in that more and more people are openly sharing very private data, and yet people are also very concerned when their privacy has been affected:
As humans, we thrive on communicating with each other, and the social tools we have available today make this so easy.
You snap a picture with your phone, and seconds later it is available to someone all the way across the country.
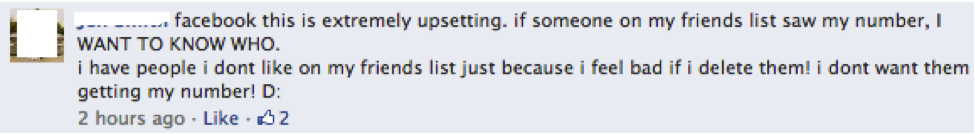
And, of course, relationships are often complicated, and some of our friends aren’t really “friends”:
If you do care about your privacy, or if you think that one day you might, you are not alone.
Just because technology allows us to share so much stuff doesn’t mean we should.
And keep in mind that those apps and social networks weren’t necessarily created with your best interest in mind.
Your private information is extremely valuable; in fact, it is a treasure trove for advertisers and is worth billions of dollars to those who sell it – and you’re not going to get one single penny for it.
Aside from advertisers, there are many other parties interested in certain things about you for their own benefit – perhaps to even use that personal information against you.
Here are some tips to safeguard your privacy. Feel free to suggest more ideas, or if you disagree, you are welcome to leave a comment.
- Think twice before posting. There’s an old adage that once something is on the Internet, it will be there forever. You may be dying to share that picture of you having a good time drinking at a party or striking a very suggestive pose, but you might really regret it one day.
- Sanitize the data you post. Make sure your car’s license plate or driveway with street sign is not visible, or else you open yourself up for some nasty surprises. We all know too well the story of people who posted a picture of themselves in front of their luxurious house with the tagline “going to Mexico for two weeks.” They might as well have added “feel free to rob my house while I’m gone.”
- Choose your online “friends” carefully. It’s typical to see some users having hundreds if not thousands of contacts on their friend list. When the list gets so big, you might not even remember who can view your updates. A little spring cleaning never hurts.
- Review your Facebook privacy settings regularly. Over the years, Facebook has reviewed its settings many times, and will most likely continue to do so. It’s important to make sure whatever new settings are in place are all right with you.
- If at all possible, encrypt your data. Storing data in the cloud is really handy because it can be accessed from multiple devices and is in theory safer than if it was just sitting on your hard drive. The big difference, though, is that what is online could be accessed by basically anybody – whether legally or not. Tip: Malwarebytes Secure Backup stores all your files in the cloud with military-grade encryption.
- Keep your data safe with good passwords. It goes without saying that your data is only as safe as the key to it. Password managers are no longer geeky tools, but have become a necessity if you use a different password for every online service you use (and you should).
- Minimize your online footprint. When browsing from a public Wi-Fi, use a VPN to encrypt all your traffic. Clear your Internet browser’s cache of cookies and temporary files. Even better, use the private or incognito features available in almost all modern browsers.
- Lastly, although not cloud related: Dispose of your devices safely. Before giving away an old computer or phone, make sure the data on it isn’t simply deleted (as in: moved to the trash), but rather erased multiple times with software such as DBAN. Some people prefer to use a good old hammer, but while it does the job, it also ruins the drive for future usage.









