Smartphones no doubt make our lives easier and it’s great having so many resources available at our fingertips.
Mobile banking is one of those resources, with banks have made very feature rich apps that allow us to access our account, deposit checks, and money transfers.
Malware writers know this and have been trying to make an impact on Android’s banking app for some time now. There have been a several families with some of the same gangs targeting PC’s also targeting mobile such like Zeus and SpyEye.
Banking Trojans on mobile were largely successful targeting older generation operating systems like J2ME and Blackberry, but haven’t made the headway they’d probably like to on Android and iOS.
On Android and iOS, there are several features (apps running within a sandbox,etc) that increase overall security.
There haven’t been any bank Trojans discovered for iOS to my knowledge, and especially not any getting in the App Store (with their walled garden approach, it’s difficult to share malware).
Android on the other hand has had their share of bad luck in this.
Mobile bankers usually monitor incoming SMS messages, as they are easily attainable without any advanced code or root permissions.
The malware will then forward them to a remote server, hijacking banking sessions, stealing mTAN codes and banking credentials. Along with sniffing SMS messages they will usually work with a PC component to help steal info.
ZitMo, SpitMo and CitMo are the mobile cousins of Zeus, SpyEye, and Citadel, three infamous banking Trojans affecting Windows. They’ve all made a splash on Android and have had some success.
Along with the big names, there have are also lesser known ones, but they are all pretty basic in their functionality.
We’ll take a glance at a few that were discovered in the wild.
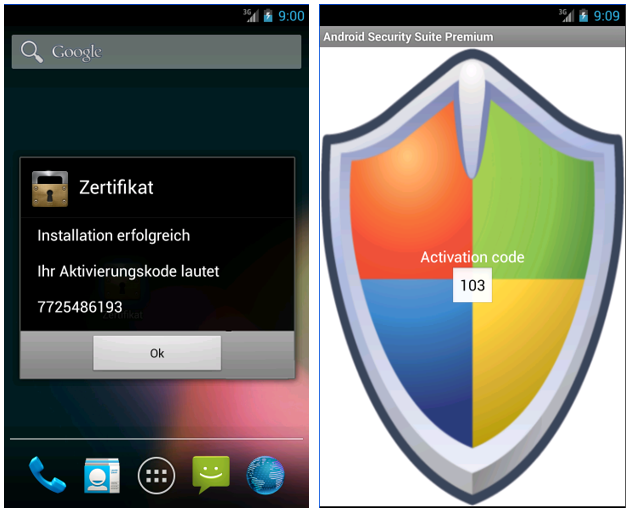
ZitMo has been around for a while with the first one being discovered mid-2011 and has disguised itself as a fake security and banking apps.
Over time, the variants contained more features, but the overall functionality is as a SMS forwarder, all incoming SMS are forwarded to a remote server, to capture mTAN codes and other banking information.
Perkel
Perkel came about earlier this year and was sophisticated in that it worked in conjunction with PC malware.
The PC malware injects into your web browser waiting for the bank transaction.
When this occurs, they prompt the user to install a security certificate and request their phone number. An SMS would be delivered containing the Android Trojan.

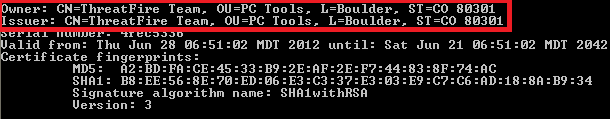
An interesting tidbit with one particular copy of Perkel was how they chose to sign the digital certificate. They choose the ThreatFire team as the company who created the app, ThreatFire was based in Boulder, Colo. and the ThreatFire product has since disappeared during multiple corporate acquisitions. It was a great security product, very innovative for its time.
This also points out how open the Android playground is, anyone can sign their app any way and there is no verification.
Hesperbot
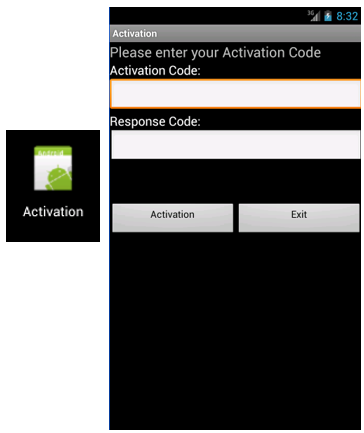
Hesperbot is the latest banker to emerge, but overall has the same functionality as the others. It also uses a PC as an infection starting point, with the PC binary being delivered through phishing campaigns. Like Perkel, it uses browser injections to display rogue banking web pages to capture your phone number—using that to deliver the Android Trojan component. Which, you guessed it, is a SMS forwarder, looking to capture authentication codes.
Although, these Android Trojans appear to have basic functionality in attempting to beat two-factor authentication they have been successful. Bank firms have taken notice, now more aware of bank Trojans after being victimized on other platforms and they are looking at ways to better protect their customers, “cough” money.
This is just a brief look at Android bank Trojans. Remember to exercise caution when using mobile banking apps and try to avoid accessing your bank accounts over unsecure and/or public networks. If you are unsure that an app is from your bank, it never hurts to check with them before installing it. Stay safe!