After supplying you with examples on how to encrypt your mail and how to encrypt files and folders I would like to give you some more information about encryption in general and other examples of encryption use.
Security is, or should be, a major concern on the internet, because we use it to send a lot of sensitive information to others. For example:
- Personal information
- Information about your company
- Bank and credit card information
- Private correspondence
Since human based code is far too easy to crack by modern computers, we rely on computers to encrypt and decrypt our sensitive data. Computer encryption systems generally belong in one of two categories:
- Symmetric key encryption
- Public key encryption
Symmetric key encryption
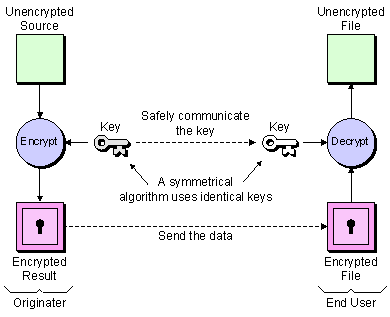
Symmetric key encryption requires that you know which computers will be talking to each other so you can install the key on each one, so each computer has the secret key that it can use to encrypt a packet of information before being sent over the network to the other computer. In principle it is a secret code that each of the two computers must know in order to decode the information.
The best example is probably AES, which the US government has adopted, and is the worldwide standard. The key size used for an AES cipher specifies the number of repetitions of transformation rounds that convert the input, called the plaintext, into the final output, called the ciphertext. Malwarebytes Secure Backup uses AES encryption for the transfer and backup of your online files.
But this design necessitates sharing of the secret key, considered to be its main weakness when there is a chance of the key being intercepted.
Public key encryption
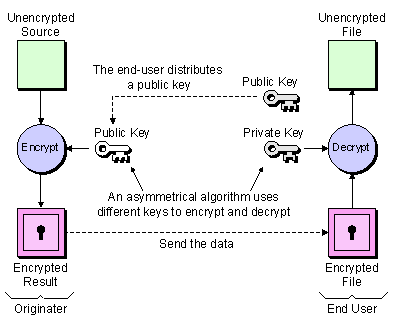
To address this weakness, public key encryption was invented.
Public key encryption uses two different keys at once. A combination of a private key and a public key. The private key is known only to your computer, while the public key is given by your computer to any computer that wants to communicate securely with it.
To decode an encrypted message, a computer must use the public key, provided by the originating computer, and its own private key. The key pair is based on prime numbers of a long length. This makes the system extremely secure, because there is essentially an infinite number of prime numbers available, meaning there are nearly infinite possibilities for keys.
One very popular public-key encryption program is Pretty Good Privacy (PGP), which allows you to encrypt almost anything. We have shown you how to encrypt files and email using PGP.
To use public key encryption on a large scale, for example on a secure Web server, requires a different approach. Here we use digital certificates. Digital certificates are issued by certificate authorities and we trust them to reveal the holder of the certificate is who he claims to be. In other words, it confirms that each computer is in fact who it says it is, and then provides the public keys of each computer to the other.
SSL is an Internet security protocol used by Internet browsers and Web servers to transmit sensitive information. SSL has become part of an overall security protocol known as Transport Layer Security (TLS). TLS and its predecessor SSL make significant use of certificate authorities. Once your browser requests a secure page (https), it sends out the public key and the certificate, checking three things:
- the certificate comes from a trusted party
- the certificate is currently valid (before the expiry date)
- the certificate has a relationship with the site from which it’s coming
When two computers initiate a secure session, one computer creates a symmetric key and sends it to the other computer using public-key encryption. The two computers can then communicate using symmetric-key encryption. Once the session is finished, each computer discards the symmetric key used for that session. Any additional sessions require that a new symmetric key be created, and the process is repeated.
Summary: the strength of encryption depends strongly on the difficulty of discovering the key, so very ingenious systems have been thought up to create keys that can withstand brute force attacks. These methods are so secure, that the human factor must be considered as the weakest link. Meaning that carelessness or manipulating the user into giving out his key are the easiest ways to break the encryption.
Illustrations courtesy of Chip Design










