Too often I see people waving their smart phones around trying connecting to any wireless access point.
The high cost of cellular data plans and a desire for free internet access will do that to people.
This may sound obvious to those who work in the security field, but many people do not always know where their mobile device is connecting to.
There is a convenience setting on both iOS and Android allowing your smartphone to automatically connect to known networks.
On iOS it is: Ask to Join Networks. On Android it is: Auto-Connect Wi-Fi. Both mobile operating systems are set this way by default.
This is a nice feature, if you approach it from the perspective of convenience.
From a security standpoint, this feature can be abused — you could be connected to a rogue access point where all your info can be accessed by a third party.
When you are home your phone will discreetly switch from the cellular network, to your access point, provided you setup your personal Wi-Fi in the past. It does this without any interaction on your part. This is great for saving on your cellular data plan, but are you sure your device is connecting to your access point?
Here, we presume that everyone has secured their wireless access points with some kind of encryption, such as a password. When you originally set up your phone onto your network, you entered your password and do not have to enter it again.
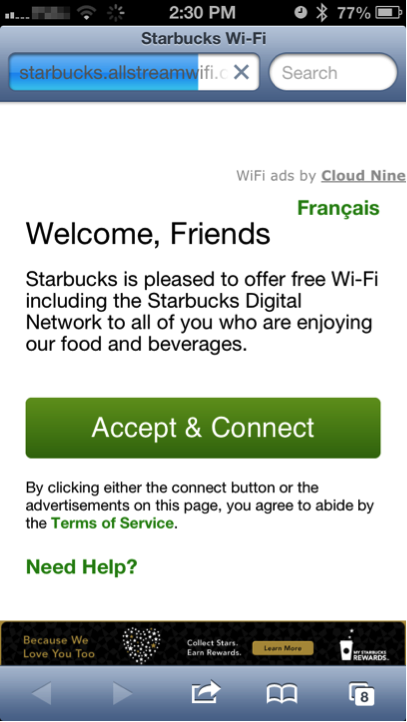
However, there are wireless access points that do not require passwords, or use encryption of any kind. This is by design. If you have ever used the free Wi-Fi at Starbucks, or at an airport, you will be familiar with these types of access points.
In brief, you connect to the unsecured access point and any web page you request is redirected to a terms of service page. You must agree to their terms before they allow you to use their free internet.
Once you have done this, and if your phone has the aforementioned convenience setting enabled, it will connect subsequently without requiring any interaction on your part.
Enter the “Wi-Fi Pineapple.”
This nifty device is derived from a small wireless access point, that has had its firmware replaced with a custom one called “Jasager” (this means the yes-man in German).

The Wi-Fi Pineapple started out as a “man-in-the-middle” tool, using a fake access point to lure unsuspecting victims to connect to your network.
This device has gone through several revisions and is now capable of much, much more.
It is typically deployed as part of a sanctioned penetration test but could also be used maliciously. (I typically use mine as an “educational” tool…)
I recently attended a security conference where I witnessed the Wi-Fi Pineapple, deployed in the field. Here are some pictures of the setup.
Here you can see the Runnur (because a fanny pack simply will not do), a kind of utility belt with convenient pockets, where we can discreetly stash all the components, such as a malicious access point including:
- A Wi-Fi Pineapple
- a 7dbi panel antennae
- An RP SMA extension cable
- A 4gb USB thumb drive (I had a horrible time finding a drive that would reliably hold the extra storage I required, 4gb was the biggest that would work)
- A USB power cable
- A pineapple Juice battery pack, to run this lovely apparatus.

The back of the “Runnur” utility belt has convenient pockets, where we can discreetly stash all the components.
And finally, a glamour shot of what the “portable hostile access point” looks like. As you can see, it’s pretty compact. You could stuff it in a backpack and make it more stealth to deploy, but the Runnur setup was so much cooler.

Here is a video of it in action along with the pre-requisites:
- My Android handset has previously connected to the free Wi-Fi of a really popular coffee shop chain (Fairly common)
- The connect automatically option is selected. (Default Setting.)
- The Pineapple has the strongest Wi-Fi signal. (Easy, with a big antenna.)
- The Wi-Fi Pineapple has been configured to broadcast the same SSID as the really popular coffee shop.
All kidding aside, the Pineapple directing me to to a “rick-roll” joke website, instead of the Google homepage helps in demonstrating how a rogue access point can be devastating. It could just as easily have been configured to serve up a truly malicious website, hosting exploits, or pushing a phishing page. With this in mind, I have put together a second video, showing credential harvesting, using the SSL Strip infusion, available to all Wi-Fi Pineapple owners.
Here are screen shots of the web interface of the Wi-Fi Pineapple. As you can see, with all the infusions installed, this device has a wealth of functionality.
So how do we defend against this type of attack? That is a difficult question. The convenience of free Wi-Fi access at public places, combined with the high cost of cellular data access makes this a very real problem.
The immediate solution is to turn “Ask to Join Networks” on in iOS, and / or “Auto-Connect Wi-Fi” to off on Android.
The Immediate result is that your phone will prompt you before connecting to Wi-Fi networks. This can get quite annoying, as you phone will now inquire about all the available wireless networks.
Perhaps a more realistic solution is to avoid connecting to web based services that require authentication when using an unknown wireless access point, something that has always been a wise thing to do.









