The SEA was at it again on Monday when they attempted to gain sympathy from members of the U.S. Marine Corps. How did they do it? By hacking of course!
An article posted on CSO this morning, by Steve Ragan, explains how the SEA were able to redirect traffic going to Marines.com to a propaganda site, asking Marines to not fight against their “Syrian Brothers.”
The redirection was not a result of any compromise to Marines.com servers and was fixed within a few hours. A running theory however, based on previously observed SEA attacks, was that records belonging to DNS servers and/or domain registrars responsible for Marines.com were to modified to send false location information to users attempting to access Marines.com.
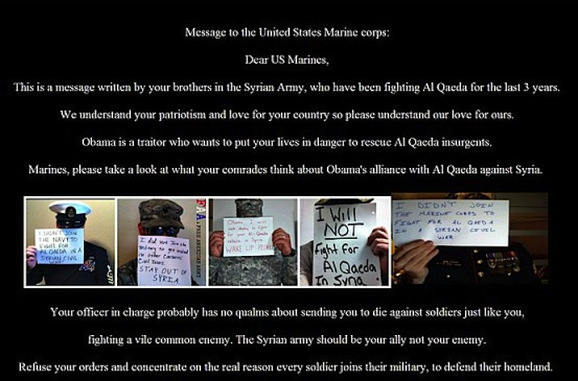
The guy on the left isn’t even dressed as a Marine, that’s a Navy uniform!
The result being that anyone attempting to visit Marines.com via the domain name would be redirected to the propaganda server.
Now, I am sure that many of our readers have been hearing a lot about DNS, redirection, domain registries and the like for some time and are probably uncertain what those things are, how they are used for the SEA’s purposes and whether or not it was the lack of security for individual web servers that caused these problems?
I want to take this opportunity to explain how this all works, I will do my best to keep it simple and understandable.
DNS and Redirection
First things first, when you consider URLs like “google.com” or “malwarebytes.org” in terms of the internal working of the internet, those terms mean little to nothing, they are just names, like John or Steve. The true identifiers for web servers are known as IP addresses. A unique number with four separate sections that help your system know how to contact a web server. Here is what an IP address looks like: 10.20.185.243. So when you type a URL into your web browser, how do you end up where you want to go, considering that URLs mean nothing on the large scale and you don’t know the IP address of the server?
Well that is where Domain Name System, or DNS, comes into play. It helps systems by taking the input of a domain name, like Malwarebytes.org, and translating that into an IP address, sending that information back to your system, allowing you to visit the requested web server. Think of it as a phone book for the internet.

Ah the old days.
When you would need to contact a certain person, you look up their name and find out what their number “or numbers” were so you could call them. DNS works the same in that you need to find out the number of a website so you reference the DNS server and find out the IP.
Unlike phone books however, every person does not have their own personal DNS server, usually there are a couple for a geographical area that multiple Internet Service providers (ISP) share to help their customers reach the websites they want to go to. DNS servers are populated with domain names and IP addresses obtained from what we call Domain Registrars.
A registry holds information about tons of domain names, based on the geographical location, usually, of the web servers using that domain. The registry keeps listings of each Domain, the IP addresses assigned to those domains, personal information about the domain name holder, etc. It then takes the relevant information, like what the IP addresses are for a certain domain name, and hands them out to DNS servers all over the world.
Here is an analogy:
A new business opens up in your town and the business registers their phone number with the proper authorities. Those authorities update the phone book that every person in town gets on occasion.When you decided you want to call that business, you use the phone book to look up the phone number of the business by referencing its name.
You as the caller are your system, the phone book is the DNS server your system uses, the phone book authority are domain registrars and the business represents a web server.
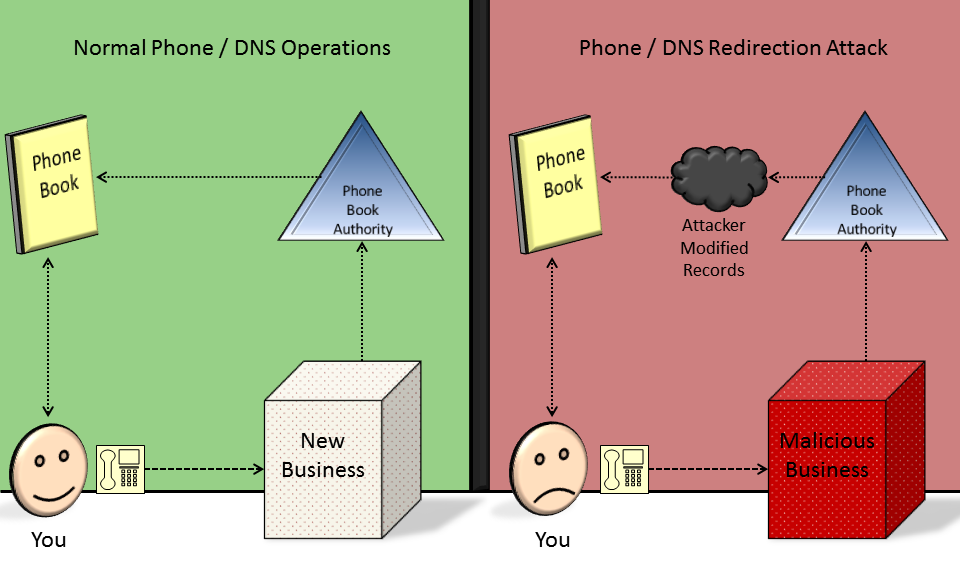
- An attacker can tell you, personally, what the phone number is of the business, though the number is wrong and it directs you to a survey call line or something, this method is not widespread and very limited.
- The attacker can break into where they print the phone books and modify the number of the business manually before they are printed, maybe for a certain city, this method is a bit more widespread but only to a certain geographical area.
- The attacker can infiltrate the phone book authorities and modify the phone number through them, so that every phone book is printed with the wrong number, everywhere. This is the most widespread method and can be on a global scale.
So in conclusion, what might appear as a compromise of a web server from the outside looking in, might in reality not have anything to do with the web server itself other than someone modified how people contact said server. Making it a very effective method to redirect users to page that spread propaganda, steal user credentials or even exploit the users browser and install malware.
The SEA have been able to compromise DNS servers and Domain Registrars by using long-term and targeted Spear Phishing attacks to obtain user accounts and modify the records of sites like Twitter.com or The New York Times.
Unfortunately, many of these DNS problems cannot be solved by individual users, save changing which DNS servers you are pointing to, and have to be left in the hands of those in charge of these systems.
Thanks for reading and safe surfing!










