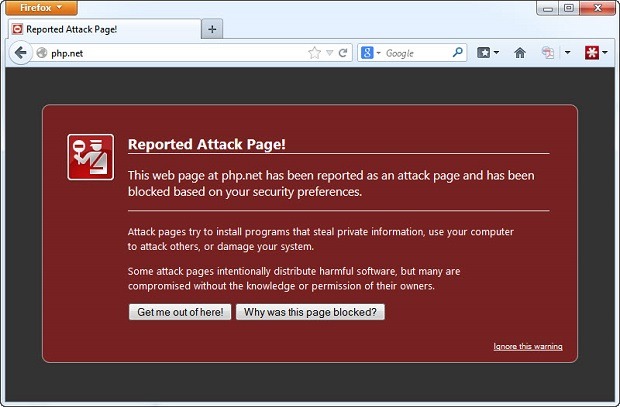
Google’s Safe Browsing System determines php.net is malicious”>
Google’s Safe Browsing system deemed the official PHP website, PHP.net, malicious last week. Though, the initial reaction from PHP creator Rasmus Lerdorf was a false positive from Google; this was not the case.
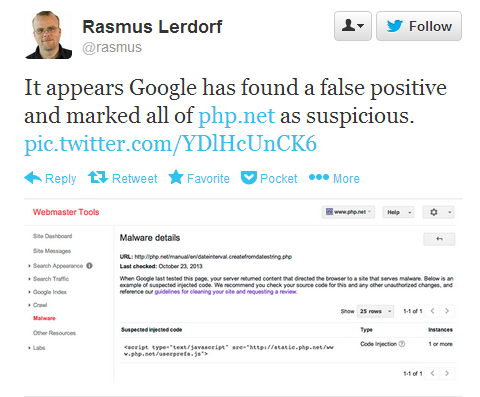
Following Lerdorf’s tweet on October 24, it was determined that the site contained a modified JavaScript page called “userprefs.js” that eventually led users to the landing page for the Magnitude exploit kit.

Obfuscated JavaScript for an IFRAME. Image: stopmalvertising.com
“Magnitude is a community name chosen for an Exploit Kit previously referred to as Popads,” said French security researcher Kafeine in a recent blog post about the kit.
In response to the attack, PHP.net was moved to a new set of servers and new SSL certificates were issued; as it’s possible the SSL private key of the site recovered by the attackers.
In addition, the PHP group has confirmed that the source code for PHP was not modified in any way from the attack.
“The highest priority is obviously the source code integrity,” as stated in the PHP.net news for Oct 24. “We see no evidence that the PHP code has been compromised.”
However, while the site is now clean, what’s most scary about all of this is the source of the breach has yet to be determined. According to an article from Ars, PHP maintainer Adam Harvey states “the investigation is ongoing. Right now we have nothing specific to share, but a full post mortem will be posted on PHP.net once the dust has settled.”
It’s true that websites suffer hacks all the time. Unfortunately, for this reason it is important to be on your guard against things like exploit kits even when practicing safe browsing habits.
Fans of Malwarebytes products can download Malwarebytes Anti-Exploit BETA for free to start protecting themselves from these sort of attacks.
For more technical details surrounding the attack, check out this analysis report from stopmalvertising.
_________________________________________________________________
Joshua Cannell is a Malware Intelligence Analyst at Malwarebytes where he performs research and in-depth analysis on current malware threats. He has over 5 years of experience working with US defense intelligence agencies where he analyzed malware and developed defense strategies through reverse engineering techniques. His articles on the Unpacked blog feature the latest news in malware as well as full-length technical analysis. Follow him on Twitter @joshcannell









