A security breach involving the makers of the popular forum software vBulletin was announced late last week.
According to their statement, hackers were able to access customers data including passwords, prompting vBulletin’s security team to force a password reset on all their customers’ accounts.
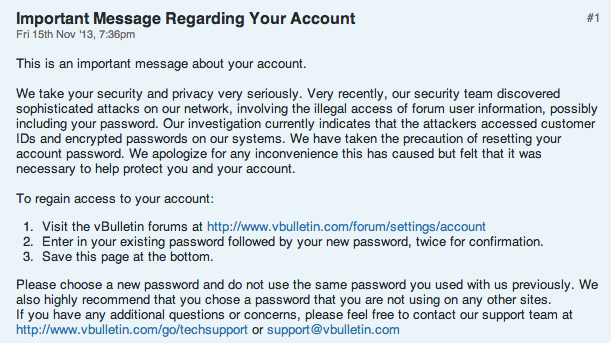
Notice posted on http://www.vbulletin.com/forum/forum/vbulletin-announcements/vbulletin-announcements_aa/4007195-important-message-regarding-your-account
Details revealed by Ars Technica show that this announcement was published three days after another high-profile breach on the MacRumors forums, which also use vBulletin.
But there was more to the story than just a security breach. Back in July, the compromise of Ubuntu forums (also powered by vBulletin) lead to speculations that a zero day vulnerability exists in the vBulletin forum software itself.
Those speculations were fueled by a Facebook post from a hacker group known as the “Inject0r Team”, and whose post preceded the vBulletin announcement.
The hackers take responsibility for both the MacRumors and vBulletin’s site hacks as well as announcing they found a critical vulnerability in versions 4 and 5 of the forum software.
These claims have not been confirmed yet, although many people are not taking any chances and are disabling vBulletin forums from their website.
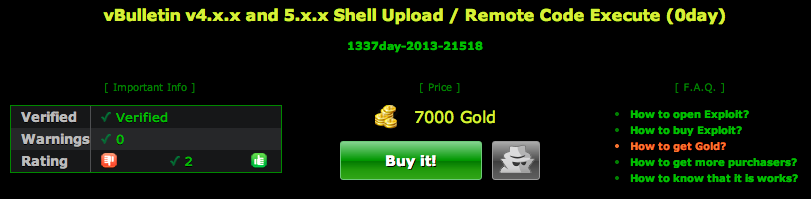
Interestingly, the Inject0r Team is selling a patch for this alleged zero day, pricing it at 7000 Gold (an equivalent of USD$7,000):
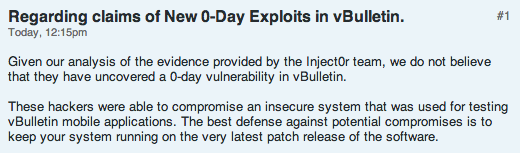
Today, vBulletin addressed concerns about a possible zero day by denying the Inject0r Team’s claims:
In all this uncertainty, there are some things to do for sure:
- If you had an account on vbulletin.com, change your password immediately. Hopefully, you did not reuse that same password on any other site.
- If you own a website with a forum powered by vBulletin, you can either shut it down until further information is released or at least put it behind a Web Application Firewall, as recommended by the folks at web security company Sucuri.
We will update this post when new information comes up.
Jerome Segura (@jeromesegura) is a senior security researcher at Malwarebytes.










