Over the last few days, I’ve seen a number of Twitter accounts belonging to both people in the security community and elsewhere sending a certain type of DM (direct message) spam, which is trying to get around whatever rogue link spam filters Twitter has in place.
I’m not 100 percent sure if Twitter is still block URLs in DMs, because my account never had that restriction placed on it, but the technique at play over the last couple of days has been seen before.
Instead of sending links to URLs, they’re compromising legitimate accounts then sending links to Tweets posted by spam profiles / other compromised accounts.
The linked Tweet will then send the end-user to the desired spam page — in this case, it’s diet spam.
Here’s the rogue DM from a compromised account sending the link to the Tweet:
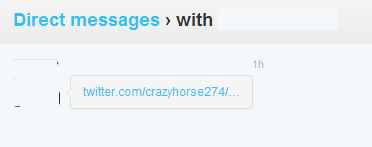
Here’s the public facing spam Tweet posted to a timeline:
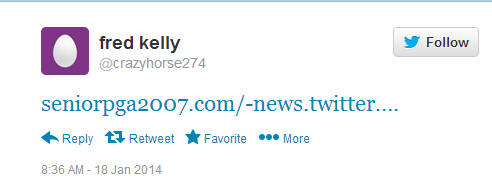
Here’s the site the end-users are redirected to after clicking the above link:
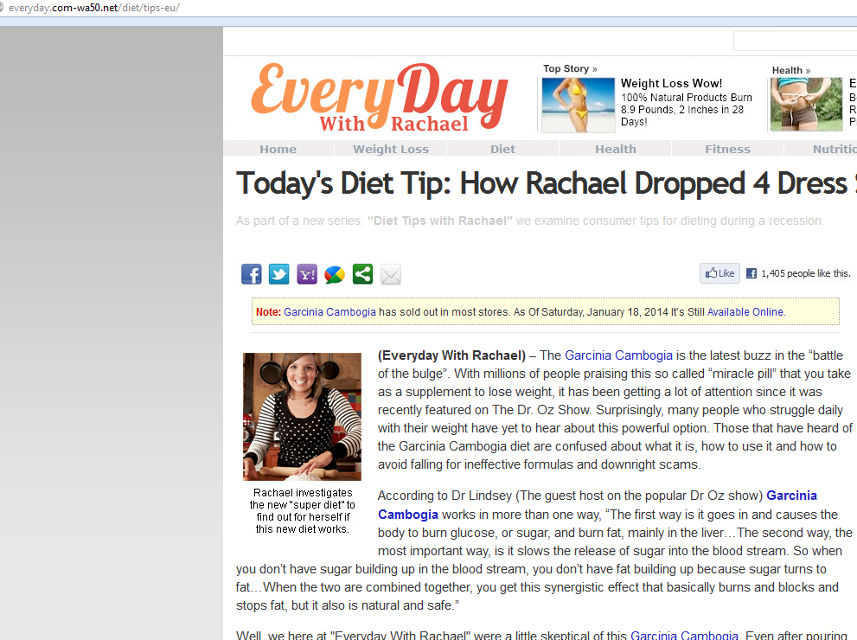
It’s surprising to see certain accounts in Infosecurity land being compromised, and there’s plenty more accounts being compromised besides those.
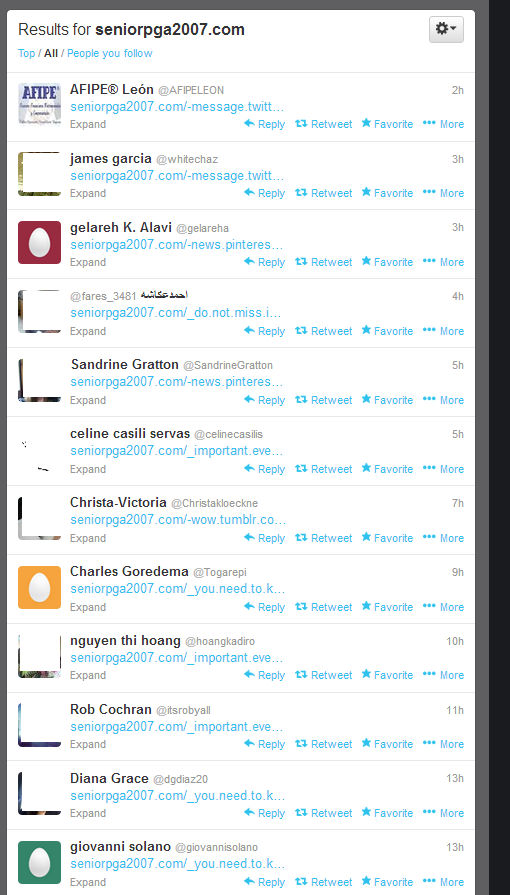
Below, you can see the latest batch related to the links being sent out. It’s possible there are other URLs being used in this particular campaign.
You should perhaps take a few moments and follow the below steps to keep your account safe(r):
1) Associate a mobile device with your account for two-step authentication.
2) How long is your Twitter password? You can set it to at least 100 characters. You may wish to consider making use of a password manager (and some of those with online functionality also make use of features such as two-step authentication, logins restricted to certain countries and more besides).
3) The email address tied to your Twitter account? Yep, you should be two-stepping all over your email account too. You’re trying to make yourself as hard a target as possible with endless, hoop-jumping layers of security for the would-be thief to throw up their hands and go “eh whatever, next target please”.
And we’re only on Step 3!
4) “Require personal information to reset my password” Enable this in your Security & Privacy settings, and anyone trying to reset your password will have to enter your email address or phone number before they can begin (which, one would hope, they don’t know).
5) You can fine tune the login experience via this Twitter help center page. A word of advice: some prefer to use authentication devices that don’t send an SMS to your phone. The reason for this is that in theory, if the attacker knew your mobile number / network provider they could call your network, pretend you’d lost your phone and ask them to redirect all SMS to “your” new number.
This would not be a good thing. Google Authenticator works offline and doesn’t use SMS, so not only are you protected from SMS redirections but you won’t have to disable two-step because you’ve travelled to an area with no phone signal / usable network – especially useful if overseas.
6) Have you checked for peculiar applications in your Apps settings? If there’s anything in there you don’t recognise or are unsure about after having tried out, feel free to revoke access.
After all of the above, visit the Twitter “Keeping your account secure” page and pay attention to the tips related to phishing links, ensuring you’re on the correct Twitter.com URL, ignoring emails send asking for your password and so on.
And take heed of Twitter’s advice to let your friends know if they’ve been compromised – no account is ever going to be 100 percent secure. By letting your friends and followers know, you may prevent many others from ending up on everything from spam and diets to Malware and phishing.
Christopher Boyd










