Online ads can be very aggressive and disruptive, not to mention they often carry malicious payloads aka malvertising.
You may have come across some strange situation on your smart phone or tablet where as you were browsing the web, the App Store or Play Store automatically popped up or even initiated a download for some random app.
It turns out this technique is not actually new per se (early reports from 2012 mention a similar behaviour which essentially hijacked your web session to trick you into installing unwanted apps).
More recently, Sarah Perez from TechCrunch wrote a nice article showing that many users were frustrated with such annoying ads and yet Apple or Google had yet to respond or comment on this subject.
What is most troubling about this is the fact that a specially crafted online advert is responsible for automatically switching the browser to a different program (the App/Play Store) with absolutely no user interaction required.
Case in point, when we visited Reddit and clicked on a thread. It opened up imgur, the picture hosting website where an ad loaded and then launched the App Store on its own, literally shoving the “Clash of Clans” app in our face.
[youtube=http://youtu.be/Zv27KsUFIOk&rel=0] (Video best viewed in HD, full screen)
You are more likely to encounter such disruptive ads if you browse dodgy sites. But due to the nature of online advertising it may also happen on high-profile sites and blogs such as the ones mentioned in the TechCrunch article.
On iOS, this issue exists both in its native browser (Safari) as well as third-party browsers such as Google Chrome.
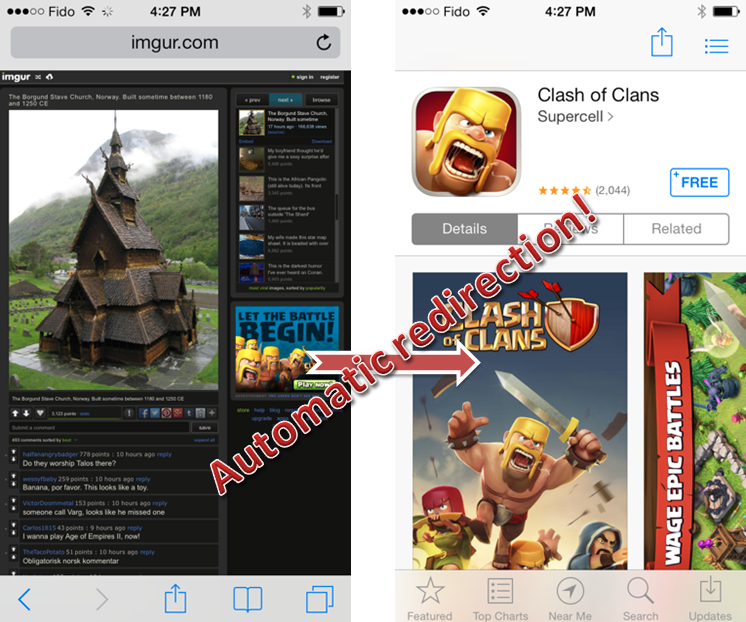
Figure 1: From browser to App Store: advert pushes install for an App.
For information, I am using the default security settings with Pop-up blocker enabled.
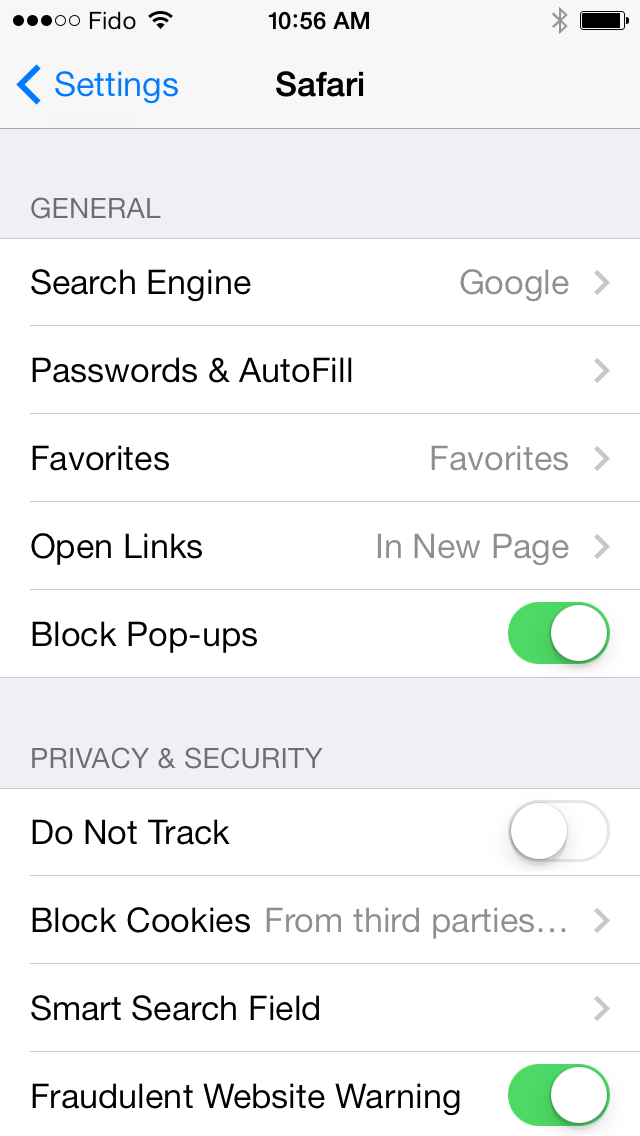
Figure 2: iOS settings for Safari.
In order to understand how this happened, I routed my smartphone through a proxy (Fiddler) and recorded the traffic:
hastrk2[dot]com sends a 302 HTTP response with a specially crafted URL (itms-appss://itunes.apple.com/app/clash-of-clans/id529479190?mt=8) that results in the App Store popping up.
On Android, the process is quite similar, albeit with a different URL format:
market://details?id=com.zoosk.zoosk&hl=en&referrer=utm_campaign%3DO1_3I_AN_XX_CA%252A007119_020868_000000_2514_1271%26mat_click_id%3Dd53619e84e977c58a8-20140203-3188
Here is a general overview of what takes place (all other non related URLs were removed for clarity) showing the many bounces involved in this campaign:
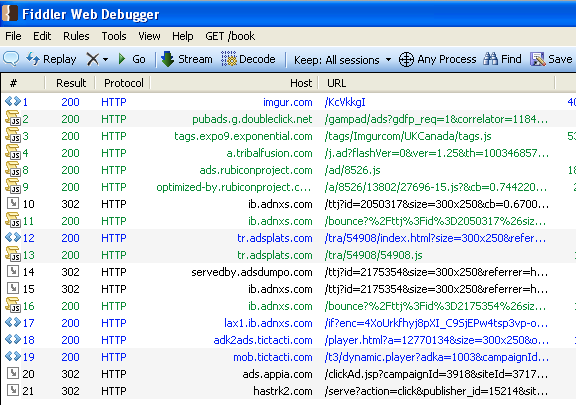
Figure 4: Each URL is linked to the abusive Ad in a very long chain.
The slideshow below reveals how each web session from Figure 4 is tied to the next one:
The domain hastrk2[dot].com has been flagged by several people (spam leading to App Store) and is hosted by Amazon Web Services (IP: 107.23.171.42) and could certainly be blocked if you wanted to prevent these unwanted redirections.
However, it would make more sense for Apple (in the name of ‘user experience’) to block all non user initiated requests to launch the App Store (or at least prompt the user before) and the same goes for Google with its Play Store.
Many layers of redirections make it harder to pinpoint which Ad network is directly responsible. But at the same time, aren’t all ad networks involved by not policing their third-party resellers well enough?
Greedy advertisers are pushing the envelope while there is no solution to stop this problem.
The app developers themselves may also turn a blind eye. They ought to know about those practices since they would be paying commissions for these affiliates. Or are they OK with that business model? For the record, our emails went unanswered.
It doesn’t appear anybody has found a name for this type of advertising/redirection, so I decided to come up with my own: Ad2Store.
As I was writing this article I came across another popular news site popping up the App Store on me again, showing that if we don’t put a stop on this soon it will quickly become widespread.
I’d like to thank my friend JP Taggart for helping me out with this project/video.
Update (Feb 18): I have contacted Amazon for them to review hastrk2[dot]com, the one site known for these unwanted redirections. Since they are hosting it, I believe they ought to check whether it violates any of their guidelines. I am still waiting for their reponse and will update this post when I hear back from them.
In the meantime, I came across one of the apps being pushed and reading the reviews made it quite clear why this practice is a major problem for end users:
I had to download this app to stop the constant hijacking from websites to its page on the App Store.
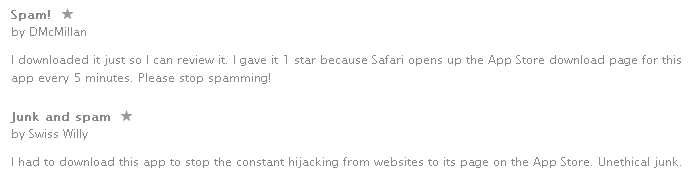
People are so desperate they are actually installing the apps in the hope that the relentless redirections stop.
Update 2 (Feb 20): Amazon has replied to our request but is not going to take any action:
After looking into this and consulting with our legal department we do not consider this a violation of our Acceptable Use Policy.
This is somewhat disappointing but we do appreciate Amazon taking the time to review this and getting back to us with a response.
Our inquiry with the domain registrar for hastrk2.com (GoDaddy) has been unanswered thus far.
—
Jérôme Segura @jeromesegura