Update (02/24/14): This exploit has been found in the wild already. It is blocked by Malwarebytes Anti-Exploit.
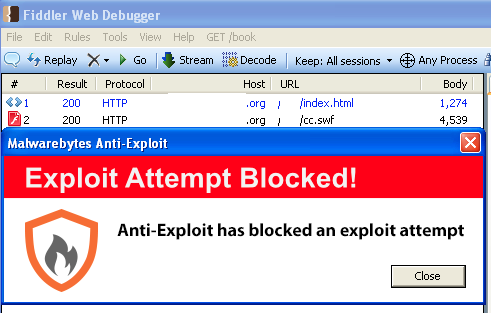
In a very busy month for vulnerabilities and only days after the Internet Explorer zero-day went public, a new vulnerability in Adobe’s Flash Player has been identified.
Security firm FireEye revealed all the details in a blog post today, saying this had been a targeted attack affecting a number of non-profit and research organisations.
Thankfully, the vulnerability which has been assigned CVE-2014-0502, has already been addressed by Adobe in a security advisory posted today.
The following versions and operating systems are affected:
- Adobe Flash Player 12.0.0.44 and earlier versions for Windows and Macintosh
- Adobe Flash Player 11.2.202.336 and earlier versions for Linux
- Adobe AIR 4.0.0.1390 and earlier versions for Android
In order to bypass Address Space Layout Randomization (ASLR) protection in Windows, this attack relied on either one of the following configurations:
- Windows XP
- Windows 7 and Java 1.6
- Windows 7 and outdated Microsoft Office 2007/2010
Users who did not fall into any of these categories would have been safe (although the vulnerability still existed in the Flash Player) showing the importance of keeping a system up-to-date.
In case you are not sure which version of the Flash Player your system is running, you can download the latest version (Version 12.0.0.70) from Adobe’s own site here.
While all these zero-days have mainly been aimed at a small number of people in very targeted attacks, it is not good news for mainstream users. With an abundance of exploit code available, malware authors now have even more weapons to use in their toolkit.
Basic security measures such as keeping your computer up-to-date, running antivirus and anti-malware solutions go a long way but still leave a small window open for zero-day attacks. Exploit mitigation software such as Microsoft’s EMET or our own Malwarebytes Anti-Exploit aim at closing that gap.










