A new and currently unpatched flaw affecting Internet Explorer 10 (CVE-2014-0322) has been discovered on some highly targeted websites, indicating a watering-hole type of attack.
I immediately tested this new exploit and was able to reproduce a successful infection on Windows 7, Internet Explorer 10 with the latest version of the Flash Player.
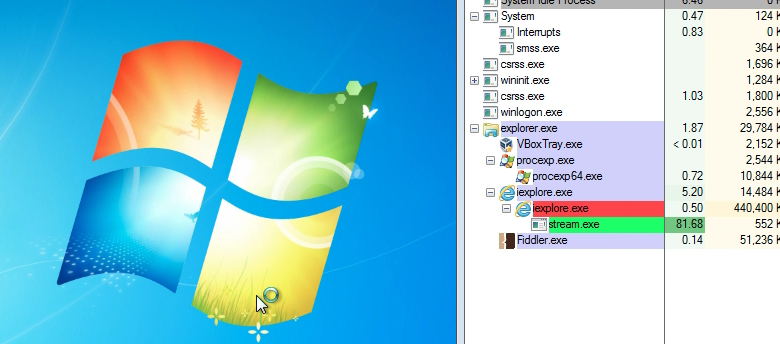
The vulnerability is a use-after-free bug that gives the attacker direct memory access at an arbitrary address using a corrupted Adobe Flash file. It then bypasses both Address Space Layout Randomization (ASLR) and Data Execution Prevention (DEP).
Here is a procmon screenshot showing Internet Explorer loading a dropped file:
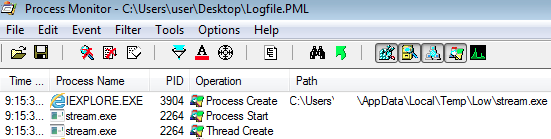
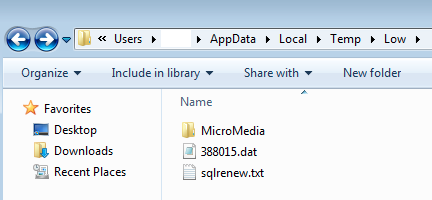
Malware binaries disguised as data or text files are dropped in %temp%low:
Malwarebytes Anti-Malware already detects and blocks those threats:
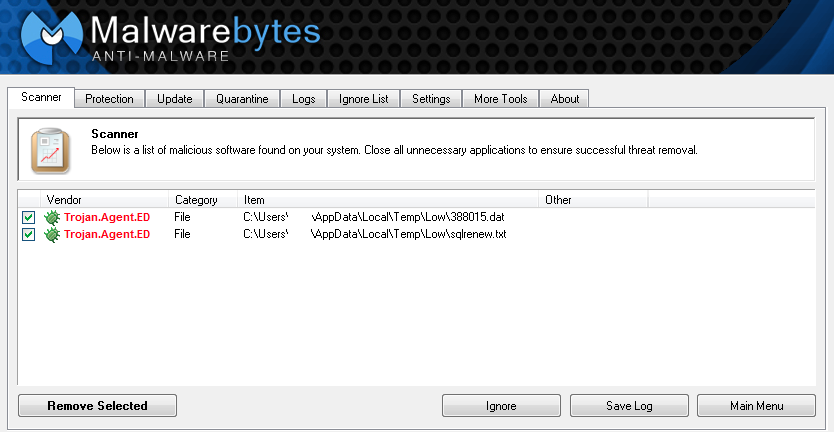
One of the files being dropped is digitally signed making it look like a legitimate application. Malware authors have abused digital certificates before and it’s still a reminder to approach all files with caution, signed or not.
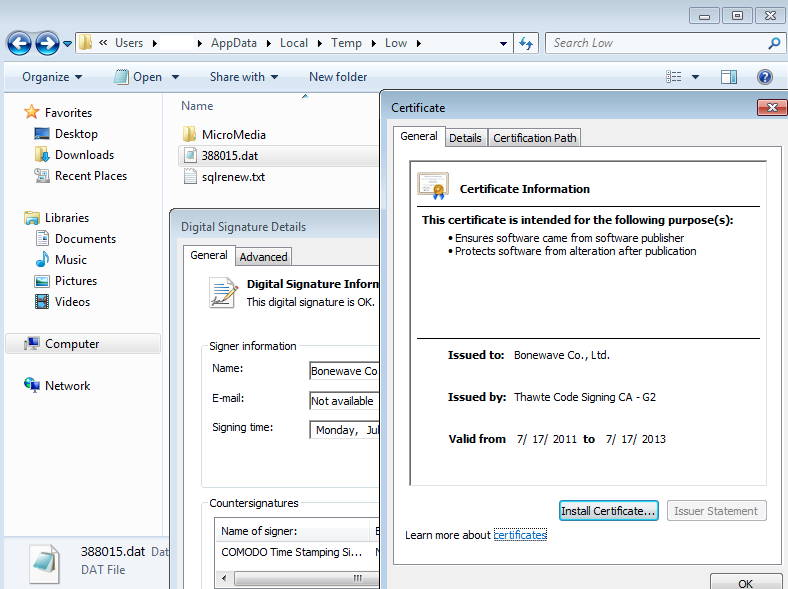
Once again, this attack was very targeted and is not currently in any of the popular exploit kits we monitor. However, now that the information has been made public, it is a race between the bad guys and Microsoft, the latter working on a fix and release for its massive user base.
Malwarebytes Anti-Exploit BETA proactively blocked this exploit, requiring no signature or update to its engine. A short video clip of the exploit being stopped can be viewed here.
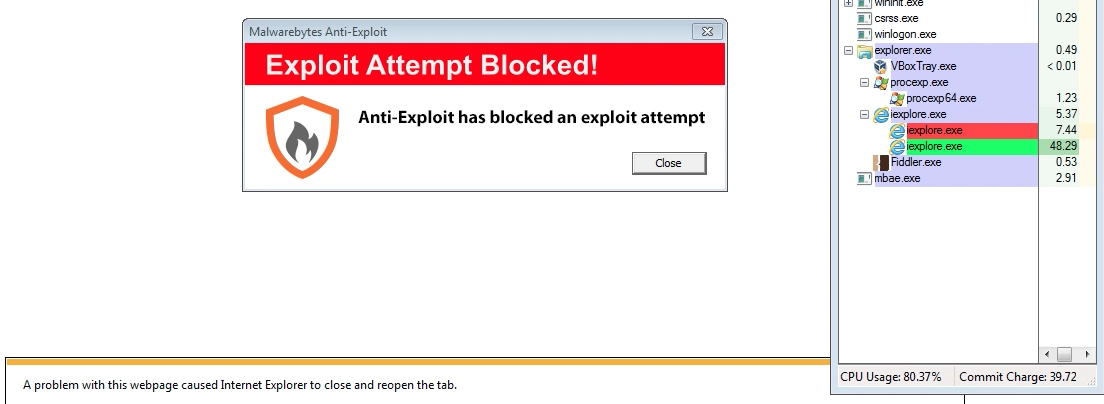
Users can also mitigate risk by avoiding Internet Explorer 10, upgrading to Internet Explorer 11 or choosing another browser.
We will continue to monitor the threat landscape as this exploit is already available for download and will be used on a wide scale soon.
Update: According to this news article from the TheNextWeb, Microsoft acknowledged the exploit and said that Internet Explorer 9 was also affected.










