Update (05/21/2014): As previously suspected, other reports also support that CVE-2013-2729 is being used in malicious PDFs).
Email remains a widely used infection vector that mostly relies on social engineering a victim to click on a link or execute an attachment.
As far as malicious attachments go, the majority are zipped executables that often use the double extension trick (i.e. Invoice.doc.exe) and will directly infect a user’s PC as soon as they are ran.
But there’s another type of malicious attachments, one that we seldom hear about, that may deceive a lot of people and sneak by your antivirus: regular documents that have been exploited.
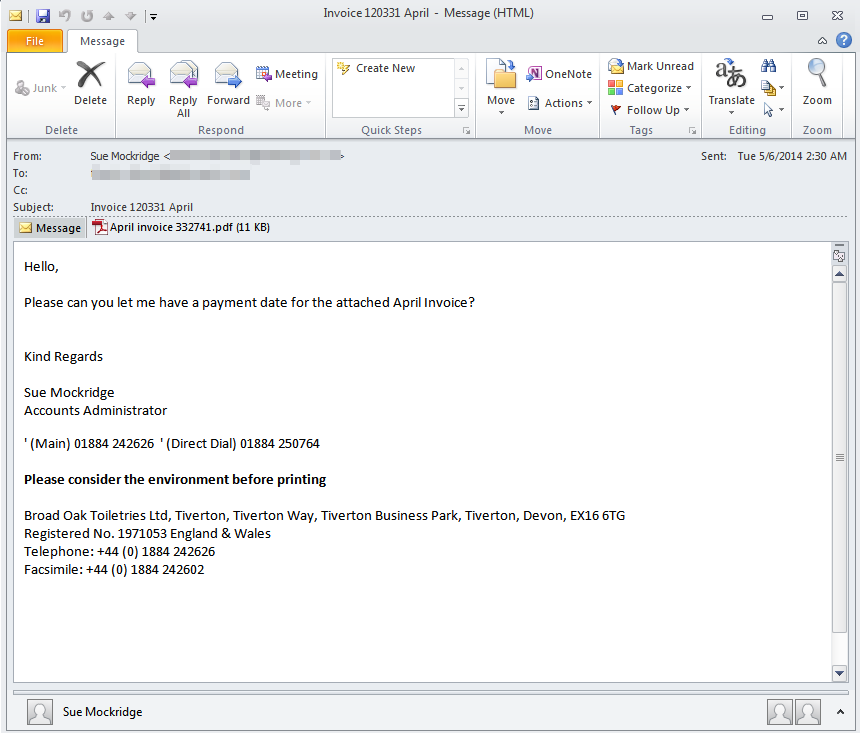
Just a couple of days ago, we spotted a new wave of spam emails spewing malicious PDF files. The decoy, which purports to be an invoice, is directly attached to an email targeting small businesses:
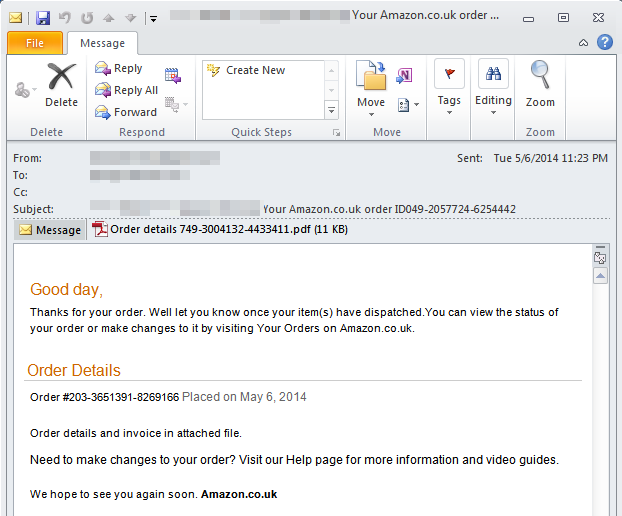
or a more generic fake Amazon invoice:
All it takes for the infection to propagate is a double-click on the PDF (April invoice 332741.pdf – Order details 749-3004132-4433411.pdf) and a vulnerable version of Adobe Reader (version 11.0 was used in this test).
This is a two-step exploitation, with first a fake error message (JavaScript):
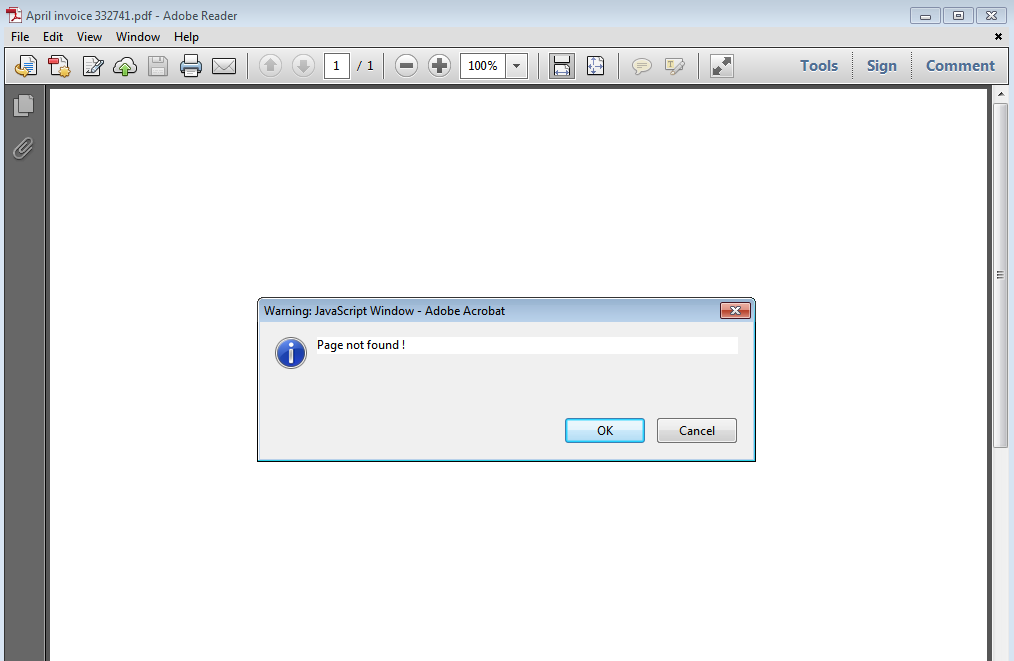
which leads to the actual exploit (CVE-2013-2729). If you have information, please share):
Let’s have a (quick) look at the underlying structure for this exploit: shellcode, heap spray
(Update 05/12/14)
The shellcode contains the URL that the exploit will contact to download the malicious payload. We can extract it using pdf-parser from Didier Stevens:
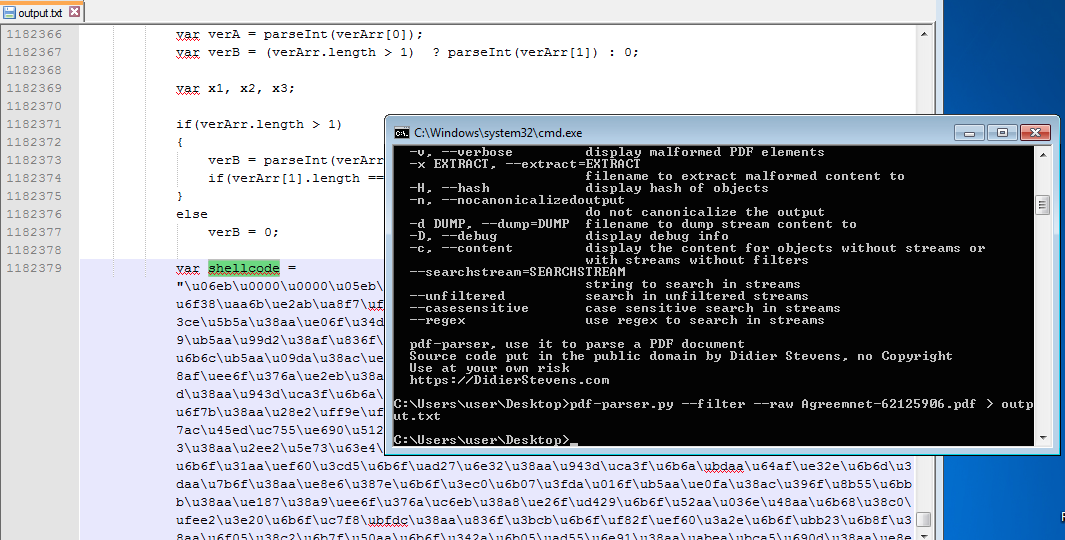
Then use a tool (Converter from Kahu Security) to convert Unicode to EXE:
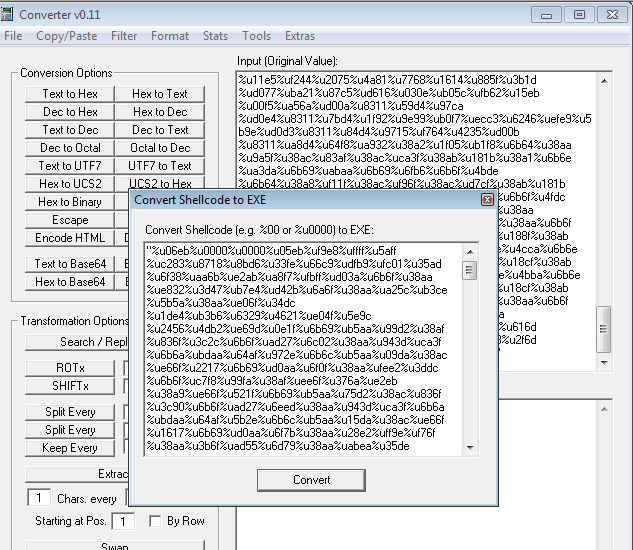
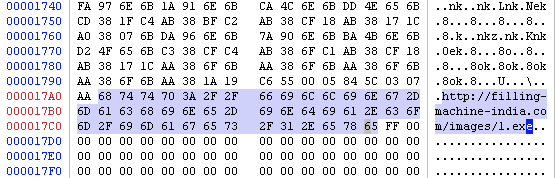
And finally view the URL with PE Insider:
This is what happens if you open the PDF with a vulnerable version (click to enlarge):
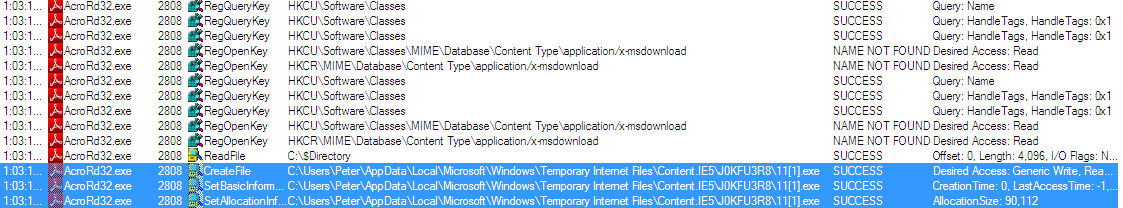
Adobe Reader downloads dr-gottlob-institut . de/11.exe (91aa1168489a732ef7a70ceedc0c3bc9), which in turn downloads pgalvaoteles . pt/111(91d33fc439c64bd517f4f10a0a4574f1):
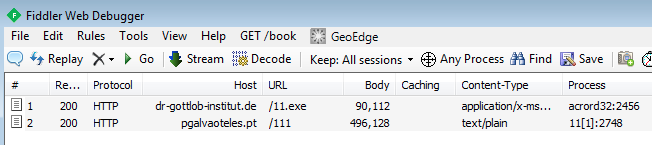
It is worth noting that both files have ‘Adobe Reader themed’ icons:
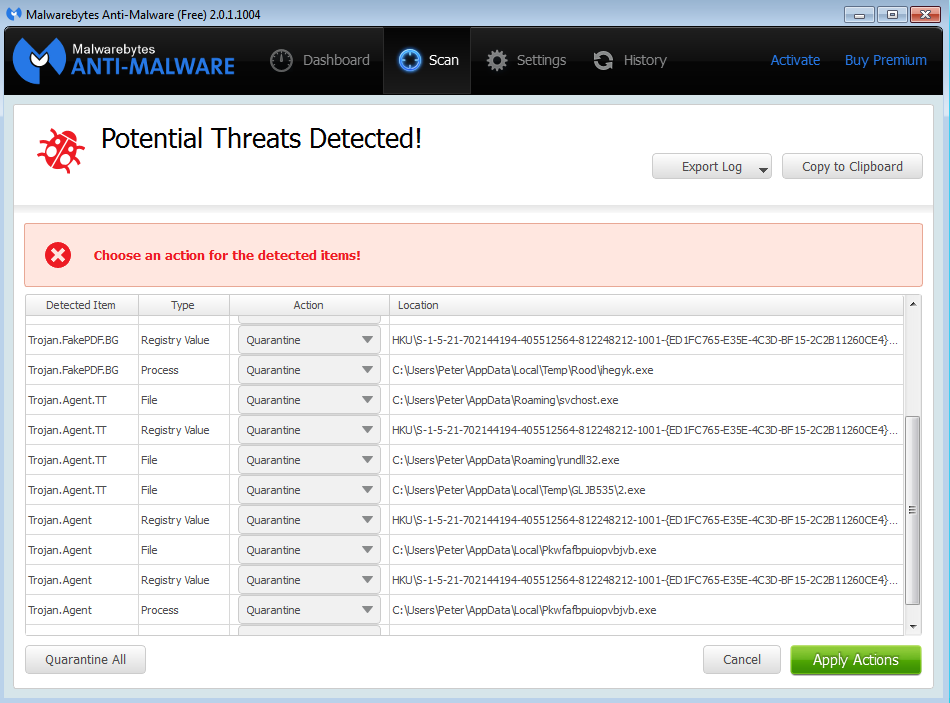
The dropped files download many additional pieces of malware: the infamous ZeuS banking Trojan, CryptoLocker as well as other threats as seen in this Malwarebytes Anti-Malware scan report:
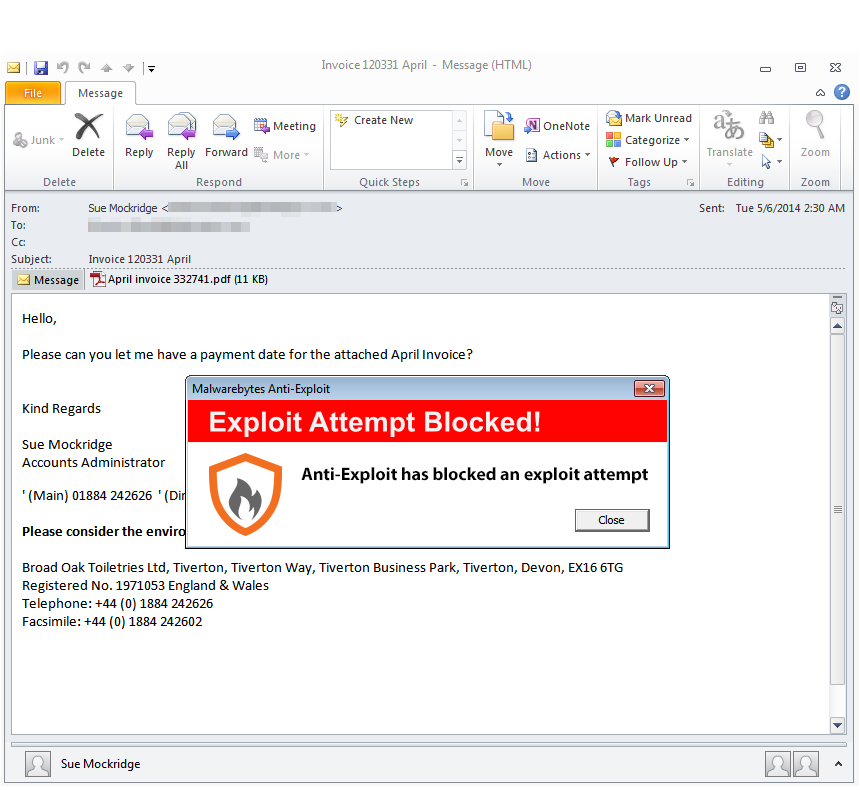
But, as with all malware, prevention is better than cure. Our Malwarebytes Anti-Exploit product is able to stop this threat before it can do damage:
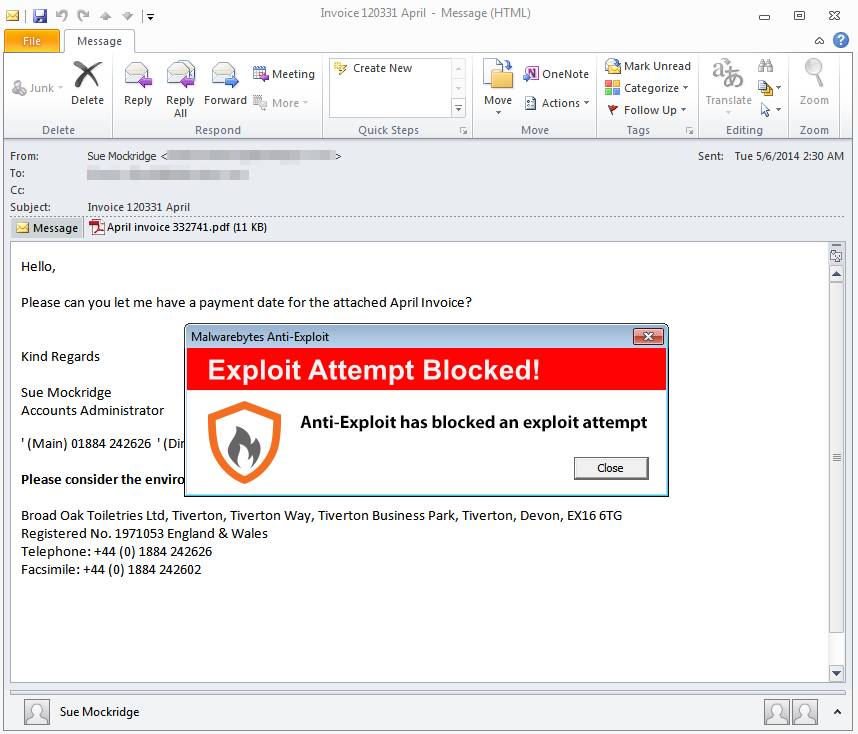
The threat is blocked as soon as the user opens up the malicious document, preventing malicious code from ever entering their PC.
Perhaps this type of threat became a little more well-known with the recent Microsoft Word Zero-Day (CVE-2014-1761) embedded in RTF documents that could exploit a system and download remote code, showing that not all exploits stem from browsing booby-trapped websites.
Here’s why exploit protection is also a better solution in this case: malicious documents typically have much lower detection rates than traditional malware binaries (notice how the bad guys didn’t even bother zipping the attachment).
There are more chances for a malicious PDF to make its way past the spam filters and more chances for the user to open it (don’t we all open PDFs from our inbox without thinking twice?).
Also, while you may want to send attachments to online scanning services such as VirusTotal, would you really want to upload and share with the world private contracts, invoices, etc?
It would be very interesting to know the infection rates between malicious documents and malware binaries. While the former do rely on the user’s machine being outdated, that factor is counter-balanced by the inherent trust in documents (Word, Excel, PDF, etc).
To mitigate these attacks, always make sure that your operating system is up-to-date as well as all the browsers and their respective plugins.
Of course, there will always be Zero-Days that make this recommendation useless, which is why exploit protection is more and more crucial.