Our researchers recently noticed a trend in phishing scams over the last week, namely that a specific style of PayPal phish e-mail has been flooding potential victims.
The text of the phishing e-mail includes:
Dear Member,Recently, there's been activity in your PayPal account that seems unusual compared to your normal account activities. Pleaselog in to PayPal to confirm your identity and update your password and security questions.
To help protect your account, no one can send money or withdraw money. In addition, no one can close your account, send refunds,remove any bank accounts, or remove credit cards. Click here to login <- Phishing Page What's going on? We're concerned that someone is using your PayPal account without your knowledge. Recent activity on your account seems tohave occurred from a suspicious location or under circumstances that may be different than usual.
What to do
Log in to your PayPal account as soon as possible. We may ask you to confirm information you provided when you created your account to make sure you're the account holder. We'll then ask you to change your password and security questions.
You should also do the following for your own protection:
-
Check your account details (address, email, phone, etc.) to make sure they're accurate. -
Review your account activity to make sure you recognise the transactions made recently. -
Report any unknown or unauthorised activity. Go to the Resolution Centre and click Dispute a Transaction
We have seen a massive amount of domains being employed to host the actual phishing page, which looks like this:
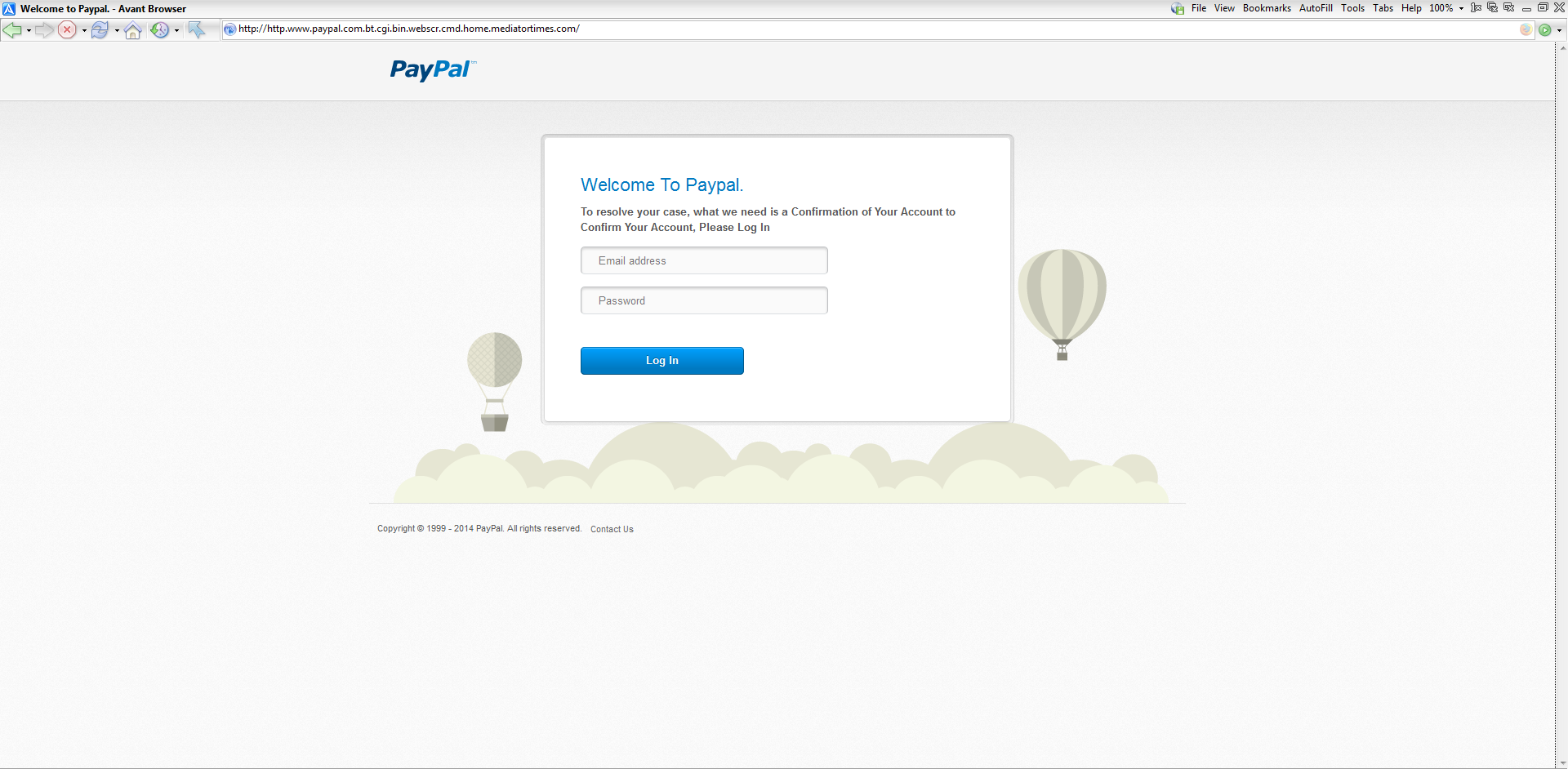
In addition to the many locations this scam is being hosted, the amount of observed IP addresses sending the phishing attack is so far over 500.
UPDATE:
To add even more urgency to this particular scam, similar e-mails have been going out that advise the user of a recent deposit to their PayPal accounts. The email includes a PDF receipt with all the details, however the attachment is a poorly masked EXE, made to look like a PDF. In reality, the executable launches a well known Zeus variant on the system.
For those that don’t remember, Zeus is a family of Banker Trojans that steal users credit card and bank login information. The family has been around for many years, always modifying it’s tactics with each new variant to avoid security protections. The current sample being sent with the malicious e-mail is well known and detected by many popular antivirus applications, including Malwarebytes Anti-Malware, which detect it as Spyware.Zbot.ED.
This particular scheme has been discovered by multiple sources including My Online Security and Webroot. Here is what the e-mail might look like:
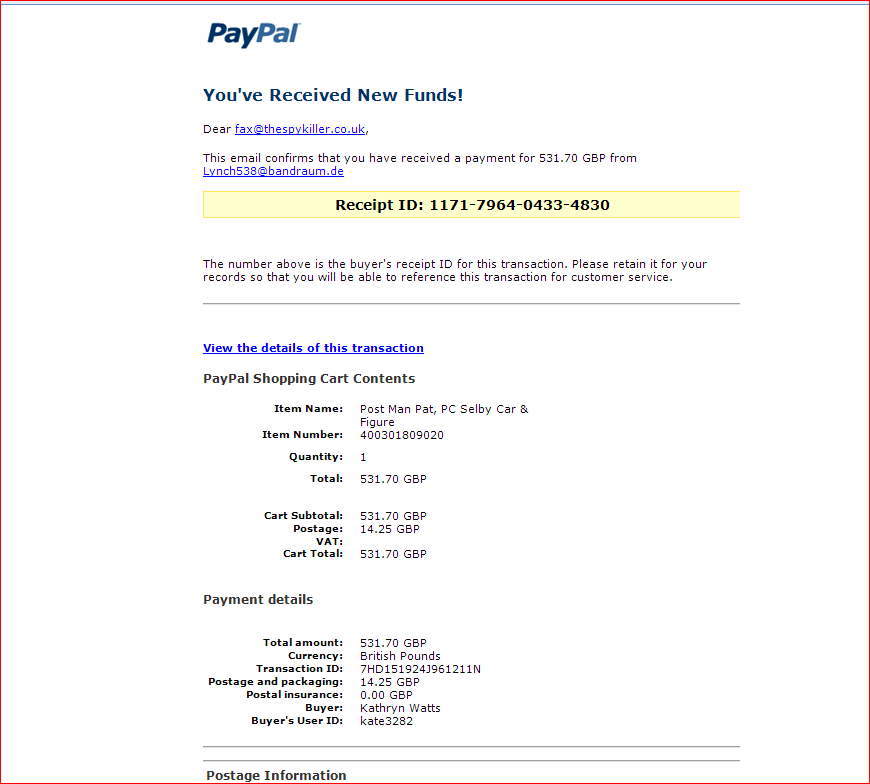
Courtesy of My Online Security
Please check out the My Online Security link for protection suggestions and the more technical analysis done by Dancho Danchev via the Webroot link.
So keep an eye out for any such scam. In addition, there seems something oddly ‘phishy’ about the pattern of these attacks and as we uncover more we will update this post.
Thanks for reading and safe surfing!











