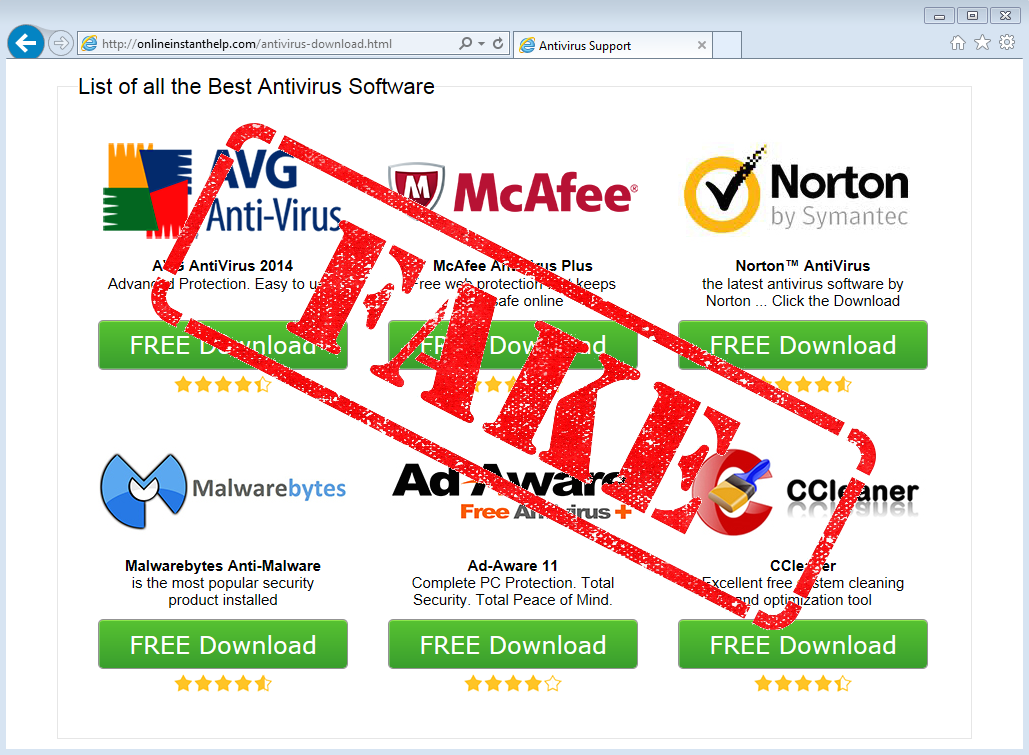
Just when we thought we had seen it all, scammers come out with an elaborate and clever scheme to trick users into calling for bogus tech support. If you are looking to download one of the popular antivirus or anti-malware product on the market, watch out before you click.
Lookalike pages
Fraudsters have set up fake download pages that look incredibly like the authentic ones. Judge for yourself:
There is even a fake page for our own Malwarebytes: 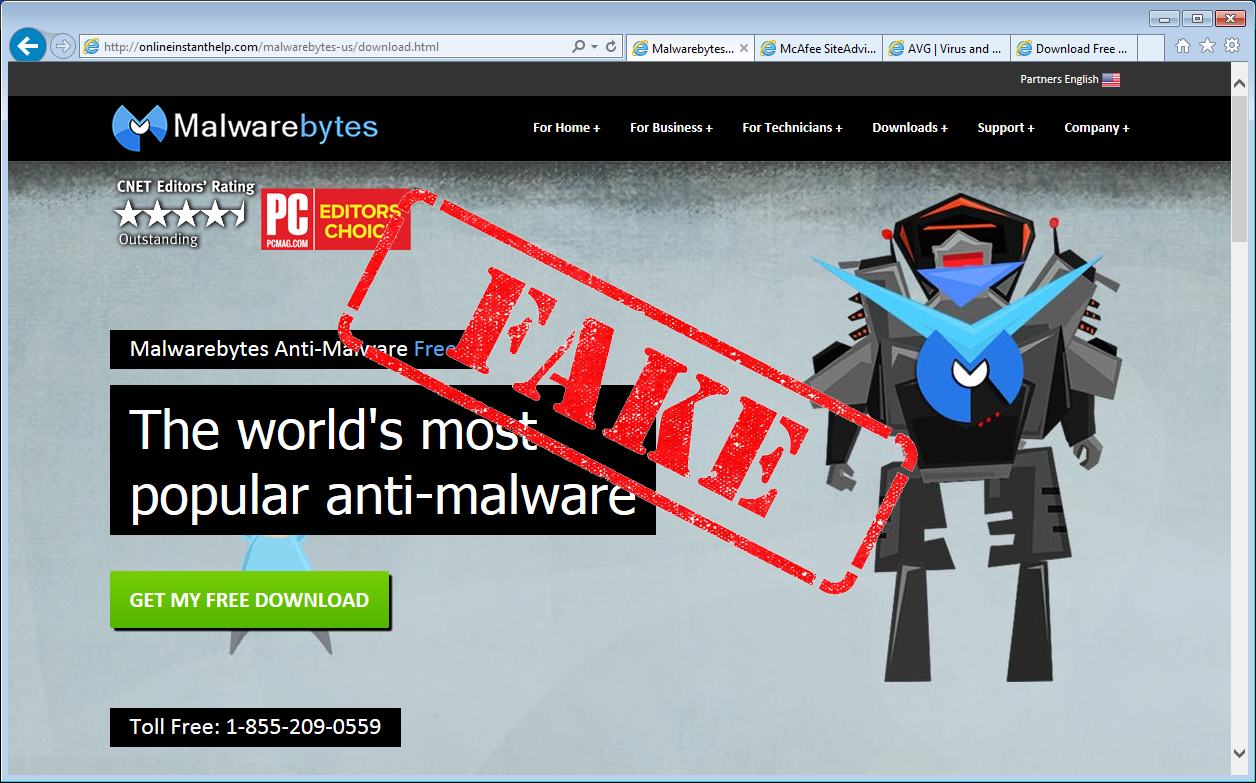
Hijacked software
Each page links to a download, which of course is not the actual software but certainly looks like it:

The guys behind this went to such lengths that they actually piggy-backed on the real programs and inserted their own piece of code half way through the installation procedure:
Have a look at how well done it is with this fake Malwarebytes Anti-Malware installer:
Call to action
The purpose of these fake programs is to trick people into thinking something is wrong with their computers:
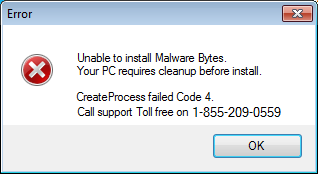
Rather clever, isn’t it? You probably know where this is going. The phone number directs you to a tech support company located in India ready to take your money once they have run their ‘diagnostic’.
Here is the video recording of the interaction with the technician:
[youtube=http://youtu.be/_gxx0actkg8&rel=0]
Behind the scenes
The fake pages are hosted here:
hzzzp://onlineinstanthelp.com/antivirus-download.html hzzzp://onlineinstanthelp.com/norton-us/download.html hzzzp://onlineinstanthelp.com/mcafee-us/download.html hzzzp://onlineinstanthelp.com/avg-us/download.html hzzzp://onlineinstanthelp.com/malwarebytes-us/download.html hzzzp://onlineinstanthelp.com/winzip-us/download.html hzzzp://onlineinstanthelp.com/lavasoft-us/download.html
The company providing ‘support’ is: wefixbrowsers.com By reverse engineering the executables we can even identify their author:
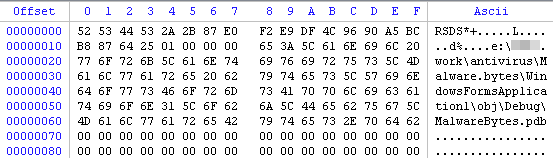
This shows the path from where the application was compiled and the user’s name:
e:{redacted} workantivirusMalware bytesWindowsFormsApplication1objDebugMalwareBytes.pdbWe are reporting the sites to the registrar and passing on the LogMeIn codes so that interested parties can take appropriate actions.
Cump Tech Media Pvt Ltd | xevoke.com,onlineinstanthelp.com | 1-855-209-0559 | LogMeIn: 186024
This company has been added to our blacklist.
To avoid these fake installers, users should always go to the company’s official website.
Another thing you can watch for is whether the file has been digitally signed by the vendor or not. This wasn’t the case here and would be a (subtle) giveaway that it is not trustworthy.
Many thanks to Stefan Dašić for relaying this information!