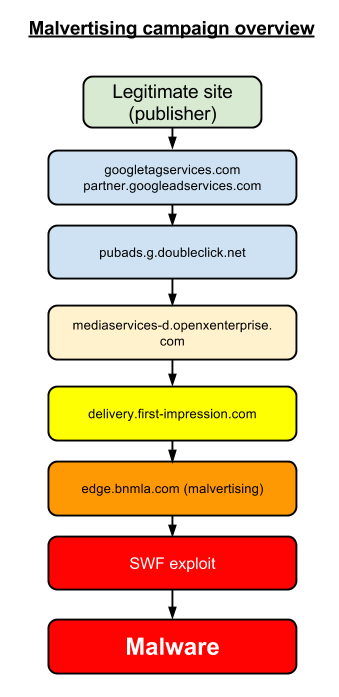
Last week we uncovered a large-scale malvertising attack involving Google’s DoubleClick and Zedo that affected many high-profile sites.
Unfortunately, another incident where DoubleClick is part of the advertising chain has happened again.
Upon our discovery we immediately notified Google so they could shut this down.
Although DoubleClick is not directly responsible, the publisher is trusting them to only allow ‘clean’ ads.
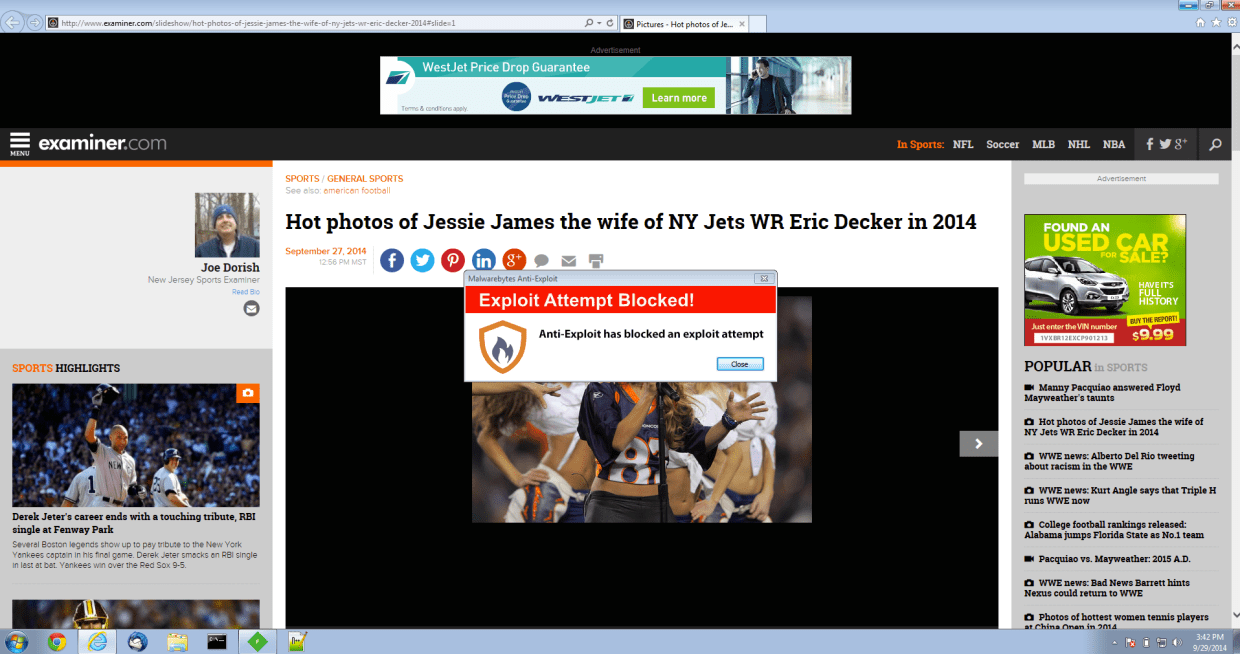
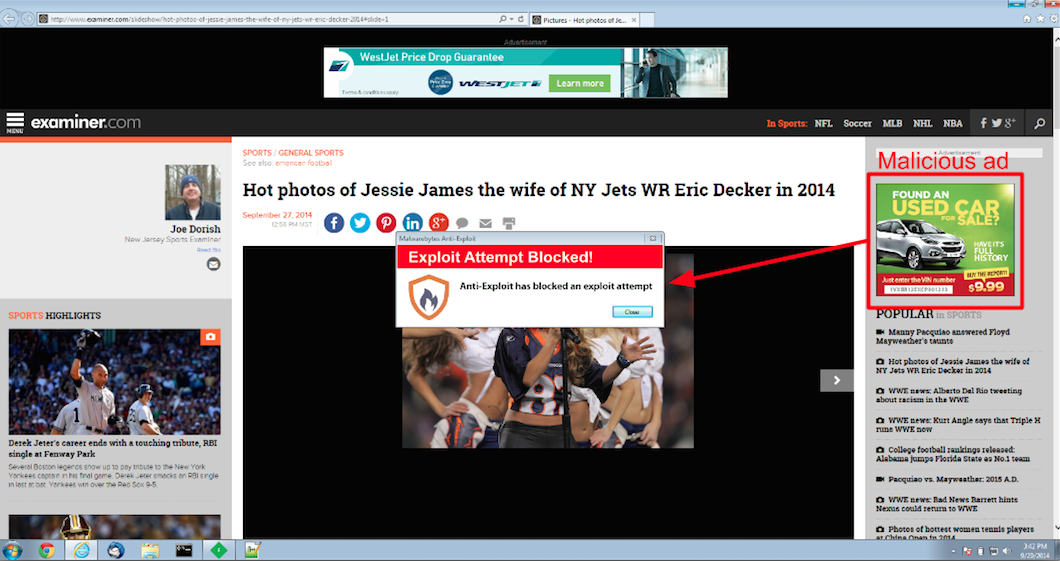
Many popular sites were caught in the cross-fire including examiner . com. The power of malvertising attacks is that they can be widespread in an instant by leveraging the advertising networks’ infrastructure.
Malicious ads are displayed to millions of visitors who do not actually need to click them to get infected.
Attack overview:
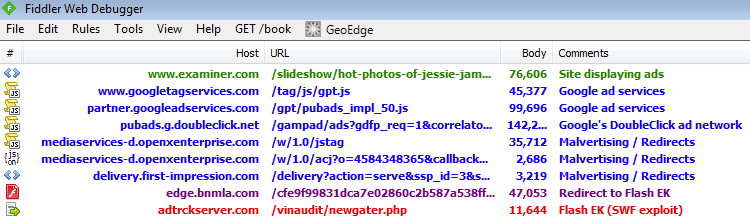
Traffic capture:
Redirection flow:
Flash-based redirection:

This ad looks legit but hides a silent redirection to an exploit page. Once again, no user interaction is required to trigger the redirection and anyone running an outdated Flash plugin is at risk of getting exploited.
I used Sulo to decrypt the malicious redirection that is hiding deep inside the Flash advert:
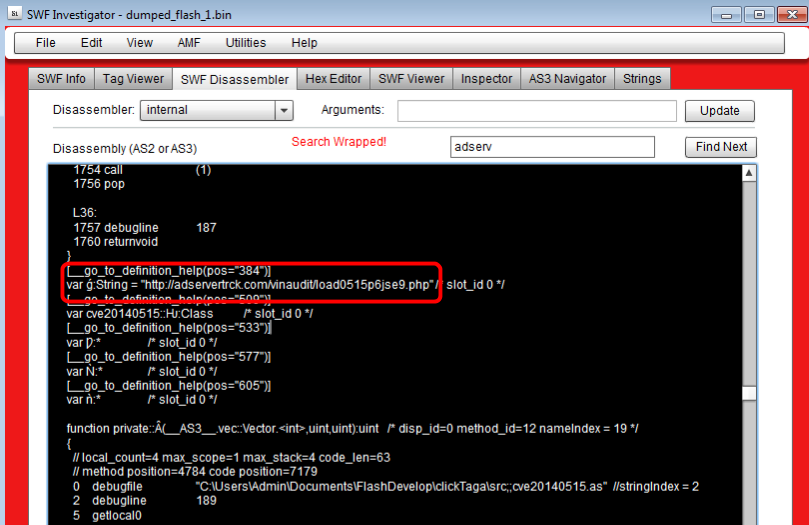
Flash Exploit Kit:
We discussed this landing-less exploit kit a week ago (‘Flash EK’ skips landing page, goes Flash all the way) and this one follows the same pattern. The first SWF file is used for redirection while the second one attempts the exploit (CVE-2014-0515).
Malwarebytes Anti-Exploit blocks this attack:
Payload:
The payload comes from hxxp://adservertrck.com/vinaudit/load0515p6jse9.php
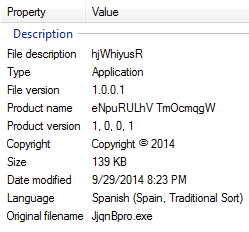
It is the infamous CryptoWall (hat tip @kafeine) ransomware that encrypts your files and demands a ransom.
Closing notes:
Last week I attended the Virus Bulletin conference in Seattle and one of the talks was about leveraging ad networks to distribute exploits. In the paper titled “Optimized mal-ops. Hack the ad network like a boss“, the authors declared “Although we haven’t yet seen malicious banners that incorporate a fully functional exploit kit, it is a possibility, especially considering the targeted character of web ads.“
This latest example shows how the lines between malvertising and exploit kits are getting blurry. The bad guys might already be there.