When it comes to online threats, these days website ads could be considered a grey area. For the majority of site owners providing free services or content, they’re good to have because they generate revenue from visits and clicks. For normal site visitors, they (we) have learned to gloss over the ads at best. Regardless of where you stand on ads, they’re everywhere, and they may be here to stay for a long time.
What most internet users may not realize is that ads can be used as doors leading to user systems, thanks to how online criminals have exploited them for their malicious purposes. Ads can be easily ignored, no matter how enticingly they flash on your screens. A well-placed ad, however, may spell greater risk for users.
Such is the case of a certain online streaming service catering to sports fans that we found recently. There was one ad directly in the middle of the video and one just above the disappearing progress bar, both completely visible in the middle of the screen. Not only are these annoying, but they make users believe that these ads, which were deliberately made to look like believable prompts, are real.
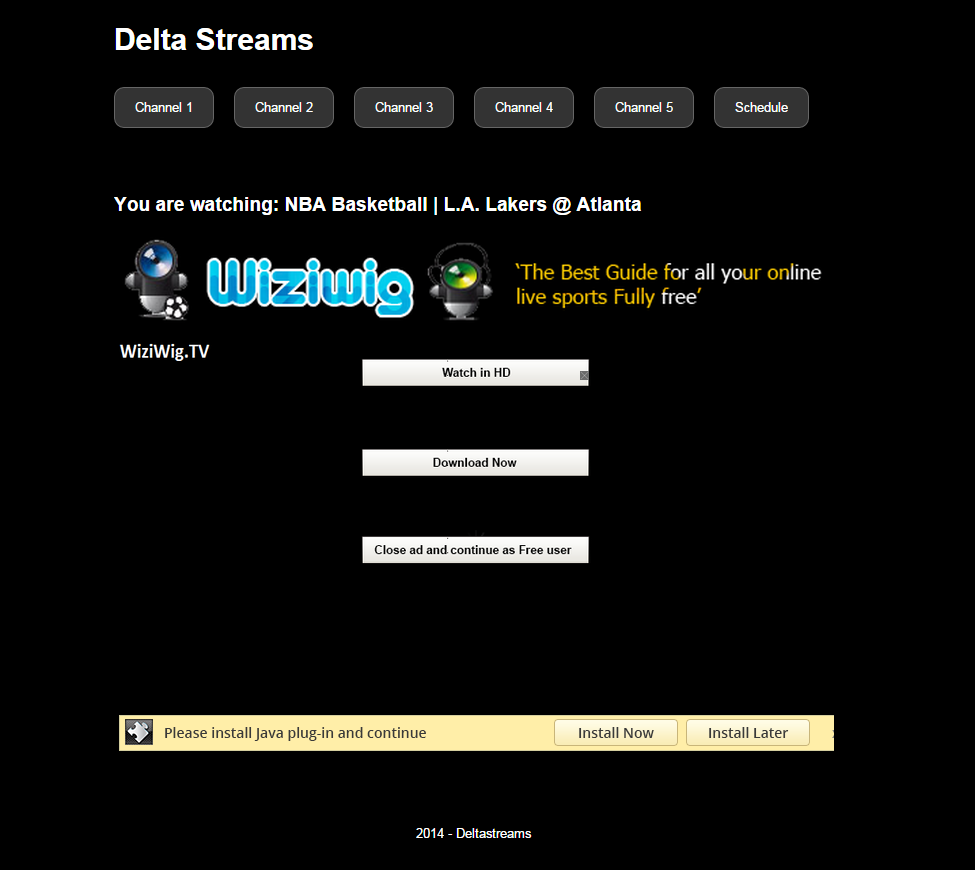
Please install Java plug-in and continue
Clicking the second ad loads the following site, which also accesses secure(dot)11-pn-installer(dot)com to download a file called setup.exe, a download manager:
Once executed, the following actions take place on the affected system:
Malwarebytes Anti-Malware detects setup.exe as PUP.Optional.iBryte (20/53). We have determined that its downloaded file, updatejv.exe, is the same as the Auto Java Updated program served on this SourceForge page. Based on user reviews, this application removes installed Java (regardless of the version) from systems before attempting to install the version it thinks is the latest, which is version 1.7.0_71. This is probably why some say it’s broken. The date it was last updated? 2012.
updatejv.exe is also said to damage the Android SDK, which could be bad if the user is a software developer.
Virus Total also has a record of the executable’s source domain, informing us that most URL scanners find it malicious.
If we look at the fake Java download page above, you will notice that it resembles the Java page in a file analysis done by our friends at StopMalvertising from a malicious ad campaign back in June.
Dear Reader, let’s take extra care when visiting sites that we know have ads on them. Refrain from clicking them (or the surrounding areas of the page you’re on as this may also trigger an accessing of an unknown if not unfamiliar site) if you can. If you want to avoid ads completely, it’s best to install ad blockers on your browser, such as AdBlock Plus (ABP), NoScript, or Ghostery.
Jovi Umawing










