When we talk to people that have been infected, they often ask how it happened. In a growing number of cases, they have been doing nothing more than reading a news website or browsing for some online shopping. They haven’t clicked a bad link, visited a risky website or installed anything strange. However, next thing they know their credit card details have been stolen, Facebook account hijacked or the pictures on their laptop are being held to ransom.
This kind of experience is increasing amongst everyday computer users because of the growing threat from Exploit Kits. This article digs into the dark world behind this problem, which contributes to a fast growing proportion of all new malware we are now seeing and tries to provide a bit of education.
What is an Exploit Kit?
These clusters of criminal code are secretly dotted around the Internet, hiding on invisible landing pages. When you encounter one, your computer is automatically catalogued. The Exploit Kit builds up a picture of what everyday software you have running, such as browsers, PDF readers, Flash Player, Java, and most importantly whether any of these have flaws, called vulnerabilities. It is basically looking at your computer for known holes to exploit.
After figuring out which of these weaknesses are present, it uses pre-built ‘exploit’ code to force this hole wide open. This essentially leaves your computer at the mercy of the attacker, allowing them to install whatever malicious software they want, bypassing many security software programs.
How do I encounter an Exploit Kit?
People most often get to Exploit Kits from booby-trapped high-traffic websites. These sites redirect you in the background, without opening any new browser windows or alerting you in any other way, so that each visitor can be scanned for their suitability for infection, and based upon this you are either compromised or discarded.
This doesn’t happen overtly and it typically works in one of two different ways. Either a piece of malicious code hidden in plain sight on the website, or an advert displayed on the page itself is infected. Both methods immediately redirect you to the Exploit Kit without showing any signs to the user. Once there, if you have vulnerabilities on your computer, it’s game over.
This means the news sites you read, the website you get your recipes from or the online store you buy your shoes from are all possible candidates.
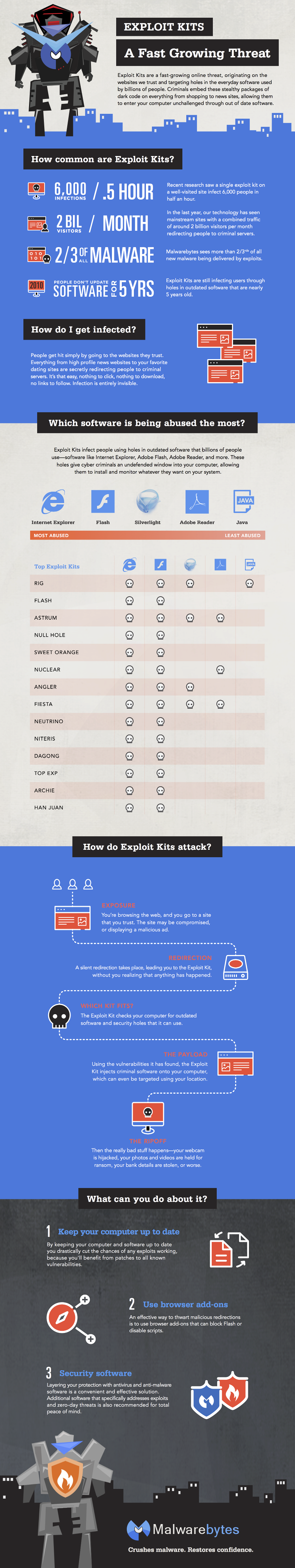
So what software is vulnerable?
In theory, given enough time, every piece of software is vulnerable. Specialist criminal teams spend lots of time pulling apart software so they can find vulnerabilities to use against people. However, they typically focus on the software applications with the highest user-base, as this presents the richest possible target. It’s a numbers game.

What about Zero-Days, what are they?
A Zero-Day is an exploit for a vulnerability that has not been patched yet. In essence, even the most up-to-date computer could get compromised. Zero-Days are rare in mainstream Exploit Kits but cannot be forgotten.
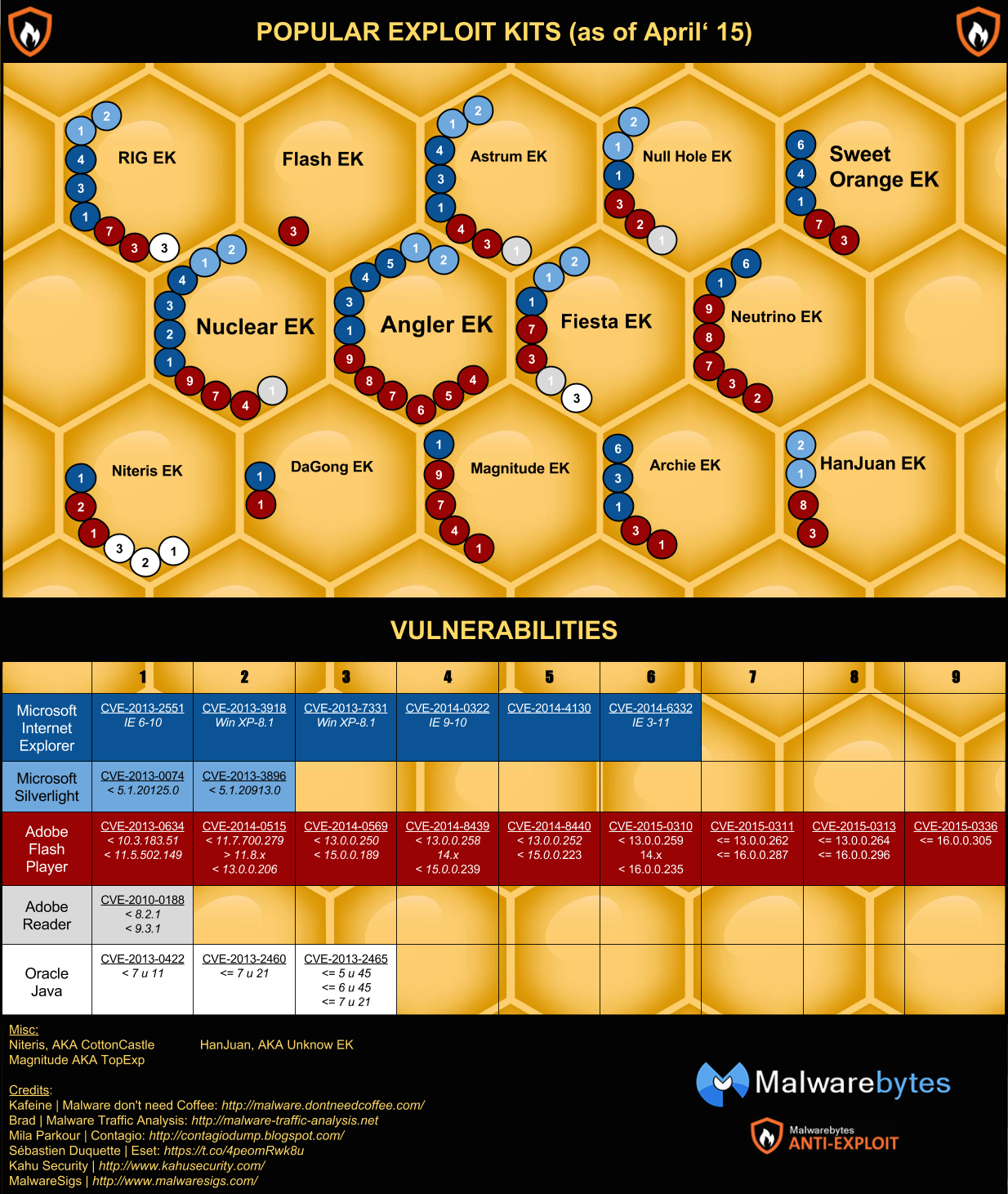
We recently did a bit of research into the top Exploit Kits being used at the moment and found that:
- Two thirds of new malware are delivered by Exploit Kits
- An estimated 2 billion visitors are exposed to Exploit Kits during a monthly malicious campaign
- Internet Explorer Is the most commonly abused browser by today’s most well used Exploit Kits
- Usage of Adobe Flash Player exploits is growing in popularity
- Exploits of up to 5 years old are still being commonly used in popular Exploit Kits, meaning people are still not patching effectively
- Criminals are turning away from Java in favor of Flash and Internet Explorer exploits
Who makes Exploit Kits?
Cyber criminals usually specialize in a specific area. For example, there are people whose job is to focus on hacking websites and placing malicious redirection code on them. The Exploit Kit authors focus on building the most effective cyber weapons they can based on the current vulnerabilities available.
They are software developers, coders who could effectively be working in the software industry but chose a different path. It’s important to note that they are not the same criminals who make malware (i.e. ransomware, keyloggers, etc.). To use a metaphor, they build a weapon which other people use to cause harm.
What makes Exploit Kits so effective?
Exploit Kits are made of different parts that can be updated as time goes on. That is one critical part as most software programs evolve and new vulnerabilities are discovered. Since there is a high demand to have the most effective exploitation tools, there is a lot of money that goes into making the Exploit Kits better.
Why aren’t my favourite sites doing anything about it?
To some extent major websites are victim of external factors such as malicious advertising, also known as malvertising. A site owner may have the most secure site there is but if third party content is displayed on his pages (as a source of revenues) it can bring the overall safety down.
What can I do about it?
To fend off attacks from Exploit Kits there are some simple but yet effective measures anyone can take. By keeping your computer up-to-date you drastically cut the chances for any exploits to work because all known vulnerabilities have been patched.
For the security conscious, using browser add-ons that block Flash or disable scripts is also an effective way of thwarting most malicious redirections although it makes the browsing experience less enjoyable.
For a convenient and yet effective solution, using a layered defence makes a lot of sense. A fully patched computer with antivirus and anti-malware is a solid protection. For peace of mind, an additional layer that specifically addresses exploits and Zero-Days is also recommended.










