Chinese PC manufacturer Lenovo made the news in a big way this week, but unfortunately these weren’t good news for anybody.
So what is all this fuss about and what is Superfish? This is the definition from Lenovo prior to the big debacle:
Superfish comes with Lenovo consumer products only and is a technology that helps users find and discover products visually. The technology instantly analyzes images on the web and presents identical and similar product offers that may have lower prices, helping users search for images without knowing exactly what an item is called or how to describe it in a typical text-based search engine.
This may sound like great new technology but users have to read between the lines:
Superfish is a piece of software that came pre-installed on some Lenovo PCs which is able to directly inject ads into your browser as well as intercept encrypted communications (HTTPS) by acting as man-in-the-middle (MitM).
The company providing MitM capabilities, Komodia, was boasting about this undefeatable technology they had developed:
Browser companies (Mozilla, Google, Microsoft) limit the usage of Toolbars and browser extension. Soon users will only be able install extensions approved by Google on Chrome. This has led to media companies to adapt with an almost certain loss of revenues, at an attempt to comply with new challenging regulations. Happily Komodia can help with these challenges via the ad injection SDK. Additionally supporting Safari and Opera, two browsers that are not monetize by current plugins solutions.
This seems like a clever way to bypass most security software and leave end users clueless about what is happening. There is no doubt that this kind of practice is within the realm of adware, perhaps even malware. Again, quoting the now offline Komodia website:
After the traffic is intercepted you can inspect it using the DLL or COM framework and decide per page if you want to inject JavaScript or any other HTML component.
This is totally unacceptable for a huge company like Lenovo to agree with, as the potential for abuse is really unlimited.
However, Lenovo initially downplayed the security risks:
Superfish technology is purely based on contextual/image and not behavioral. It does not profile nor monitor user behavior. It does not record user information. It does not know who the user is. Users are not tracked nor re-targeted. Every session is independent. When using Superfish for the first time, the user is presented the Terms of User and Privacy Policy, and has option not to accept these terms, i.e., Superfish is then disabled.
This backfired on them and the backlash became so intense that Lenovo changed position and is now calling it the “Superfish vulnerability“
Lenovo Security Advisory: LEN-2015-010
Potential Impact: Man-in-the-Middle Attack
Severity: High
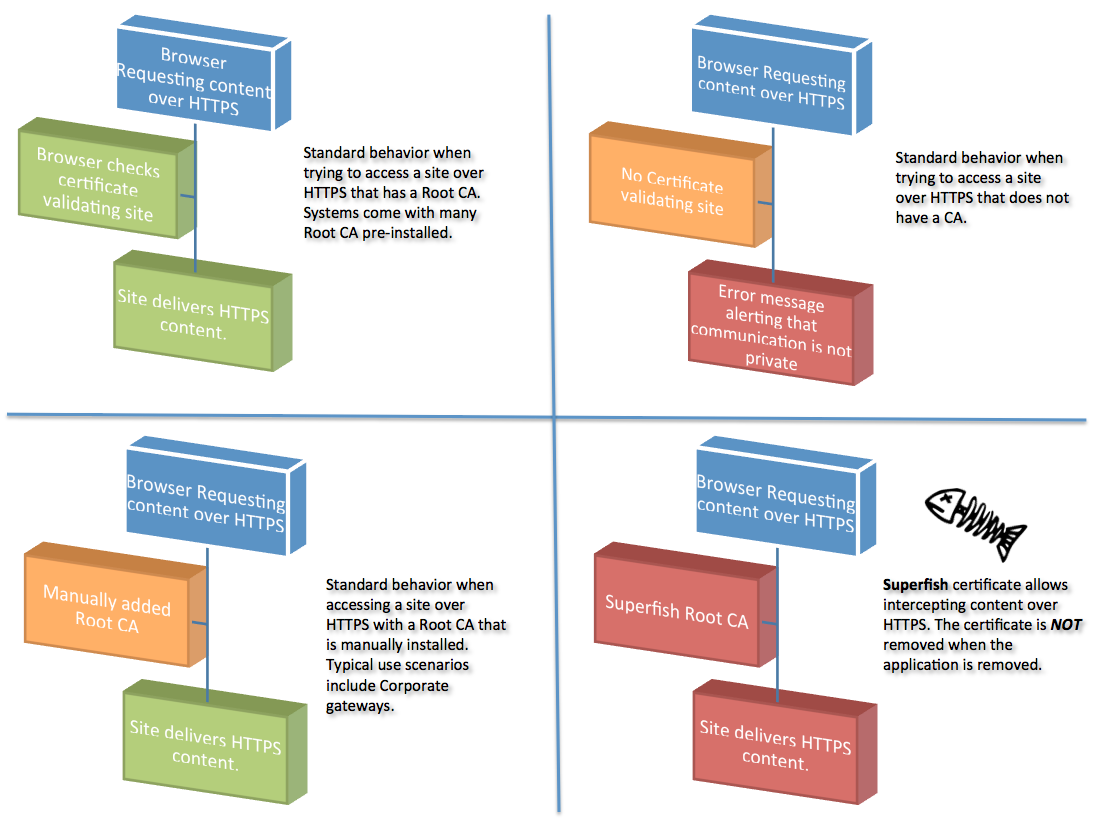
On top of undesirable ads being literally forced into your browser, Superfish also introduces major vulnerabilities because it uses a valid encryption certificate which has already been compromised.
Attackers on the same network (i.e. your local coffee shop) can now read all your encrypted communications as well as spoof legitimate websites with phishing pages.
To find out if you are affected, you can visit this site.
Additionally, we have a full removal guide for Superfish and the dodgy certificate.
The online community will not stand for such intrusions in privacy and poor security implementations whether it comes from governments, Adware companies or PC manufacturers.
The best we can hope from this fiasco is that the message has been sent loud and clear to any other companies even thinking of going down that path.
Thanks to Pieter Arntz and JP Taggart for additional research assistance.