The online advertising industry is a very lucrative business and so it comes as no big surprise that cyber-criminals have taken a keen interest on how to ‘milk’ it using different fraudulent techniques.
One particular technique known as malvertising, leverages the infrastructure provided by ad networks to distribute malicious content to end users while they browse the Internet.
Today we are looking at a prolific ad network (over 180M hits/month according to SimilarWeb) being used by online fraudsters to distribute malware and other nuisances. Popcash is a pop-under ad network that offers services for both publishers and advertisers.

Pop-under ads are similar to pop-up ads, but the ad window appears hidden behind the main browser window rather than superimposed in front of it. As pop-up ads became widespread and took up whole computer screens, many users learned to immediately close the popup ads that appeared over a site without looking at them. Pop-under ads do not immediately impede a user’s ability to view the site content. They usually remain unnoticed until the main browser window is closed or minimized, leaving the user’s attention free for the advertisement. Research has indicated that users therefore react better to pop-under advertising than to pop-up advertising because of this different, delayed “impression”. —Wikipedia
Malvertising analysis
First, let’s do a quick analysis of the malvertising case we have on our hands.
Loading the following ad URLs, is a little bit like spinning the wheel of a gun in that you take a chance with your computer’s security.
http://popcash.net/world/go/49931/92055/ http://popcash.net/world/sgo/49931/92055/367b01ac31fe6ea1/
In this case, we received a URL used as a gate to an exploit kit:
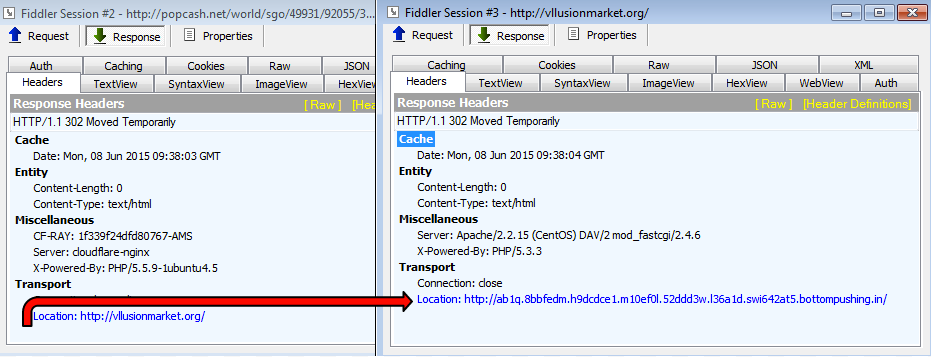
Magnitude exploit kit
The Magnitude EK starts with a simplified landing page that contains the code to launch a Flash exploit and an iframe to perform an Internet Explorer exploit:
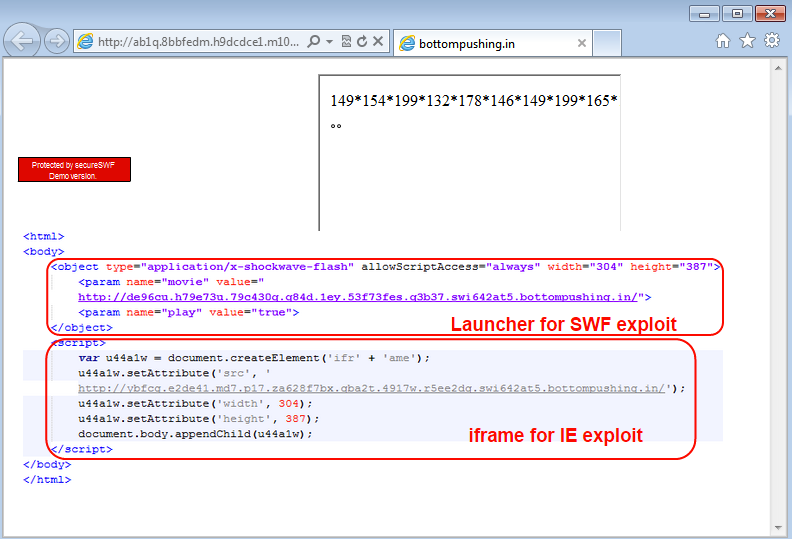
The Flash exploit (VT) is CVE-2015-3090 (thanks @TimoHirvonen).
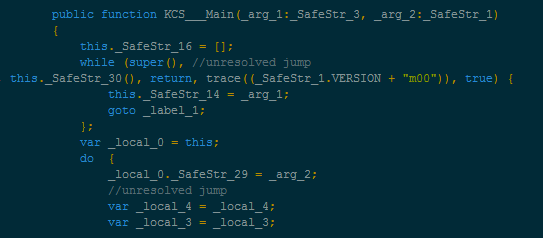
The Internet Explorer exploit is prepared via a heavily encoded piece of JavaScript:
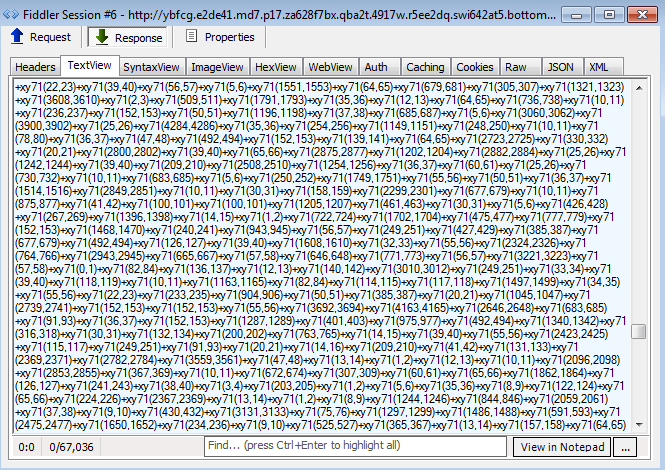
Shellcode is used to deliver the binary payload(s) via urlmon.dll:
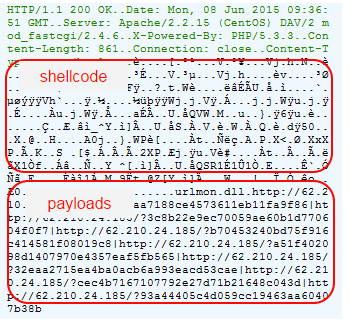
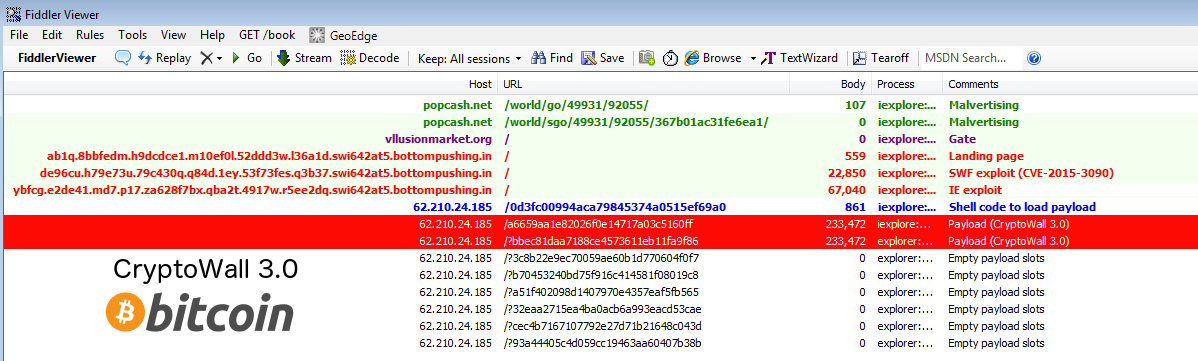
Several URLs are loaded but only a couple actually loaded the same binary (VT) detected by Malwarebytes Anti-Malware as Trojan.Dropper.Necurs, which eventually loads CryptoWall 3.0.
However, other slots are available and could be filled with different malware families by the exploit kit operator.
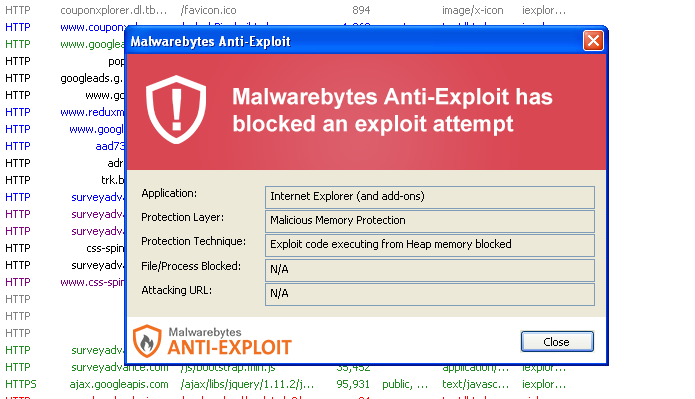
Malwarebytes Anti-Exploit users were protected from this attack:
Fiddler summary:
CryptoWall 3.0
Magnitude EK, just like many other exploit kits recently, is pushing crypto ransomware, possibly one of the worst strains of malware because it uses genuine encryption to lock down a user’s personal files.
Soon after the ransomware takes over the PC, it will prompt a message warning of what just happened and giving details on how to proceed.
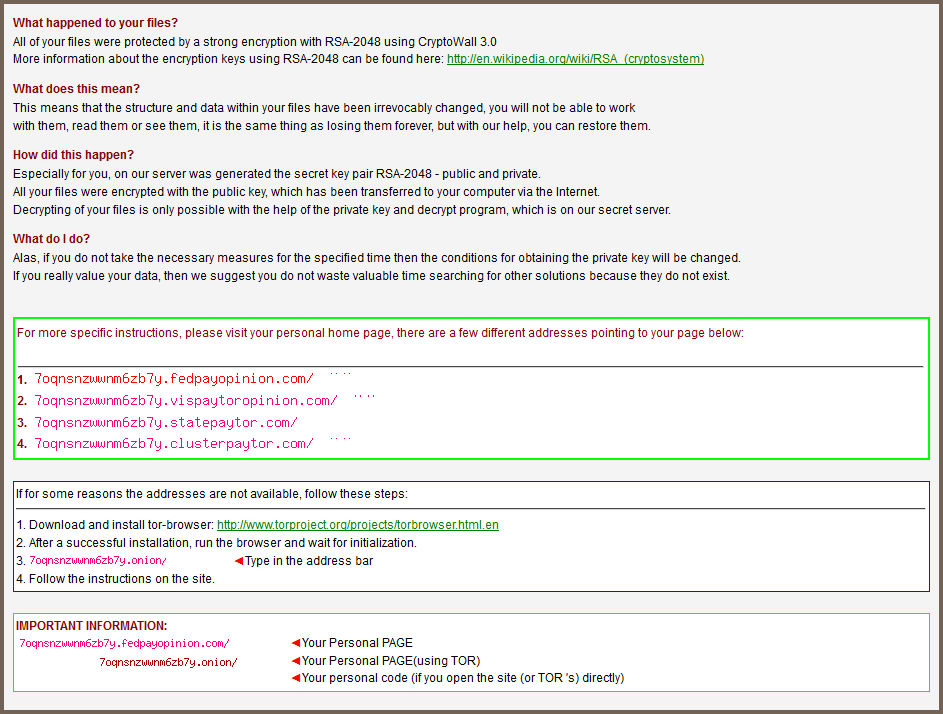
In this case, one needs to pay $500 to get their files back within the deadline, otherwise that amounts doubles:
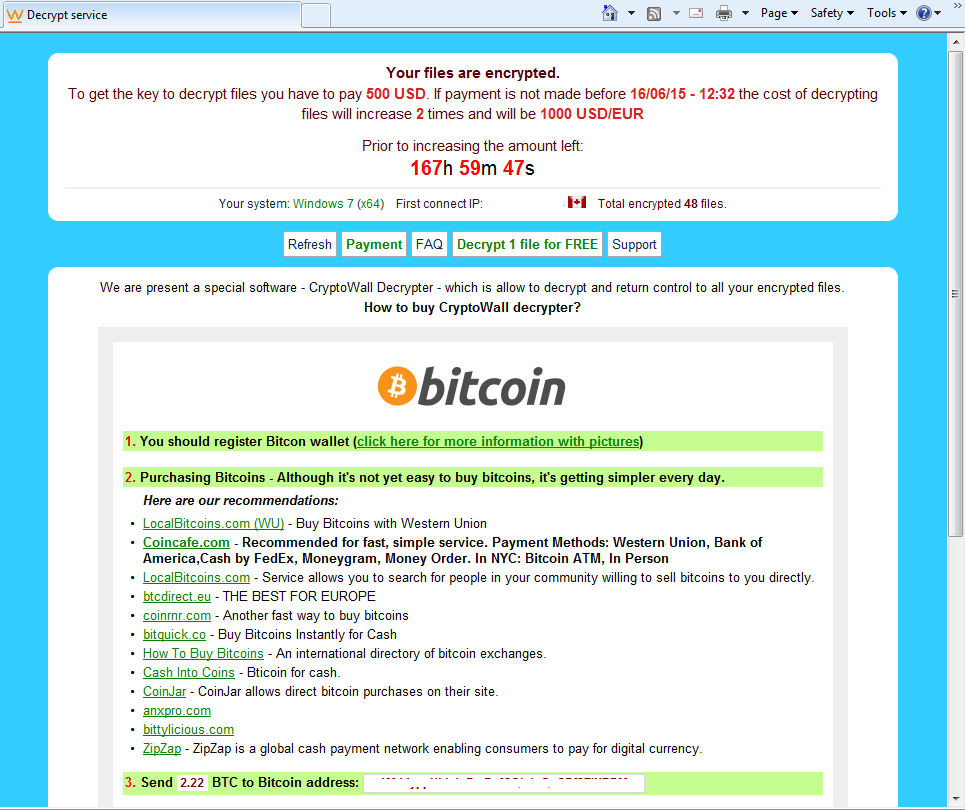
Paying the ransom as a desperate measure to get those important files can be understood but it also keeps this underground economy flourishing.
Conclusions
Because malvertising involves multiple players in order to work (publishers, ad networks, visitors) each has its own role to play in combatting this problem.
Publishers can be wise in choosing their third-party advertisers by choosing reputable ones (although it is not a 100% guarantee (nothing is) that incidents will not happen).
Ad networks can and should also ensure that the traffic they serve is clean. We contacted Popca$h on two separate occasions through their official “report malware” page, but never received a response.
The campaign is still ongoing and not only serving exploits but also tech support scams customized for your browser, ISP, city, etc:
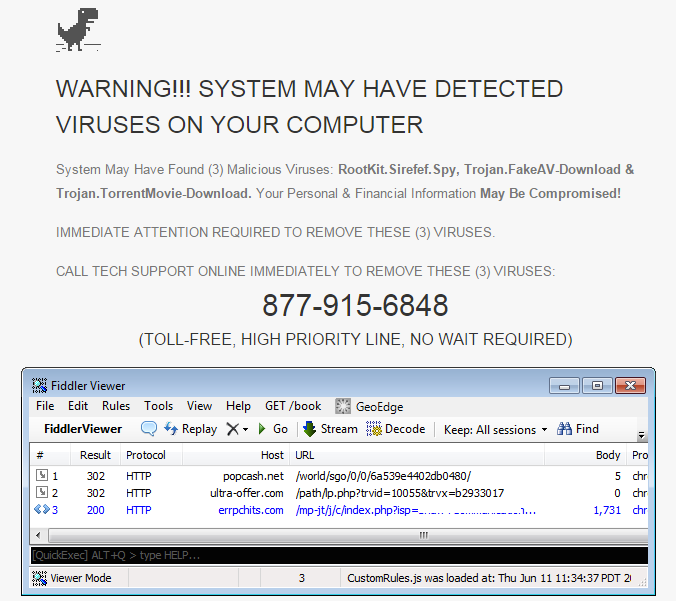
Visitors can dramatically reduce the risks by keeping their computers up to date and ensuring that they have anti-exploit and anti-malware installed. As we have seen recently, this can even act as a deterrent.
Update: 06/15: Popcash sent us an email acknowledging the problem and saying the malvertisement has been blocked.










