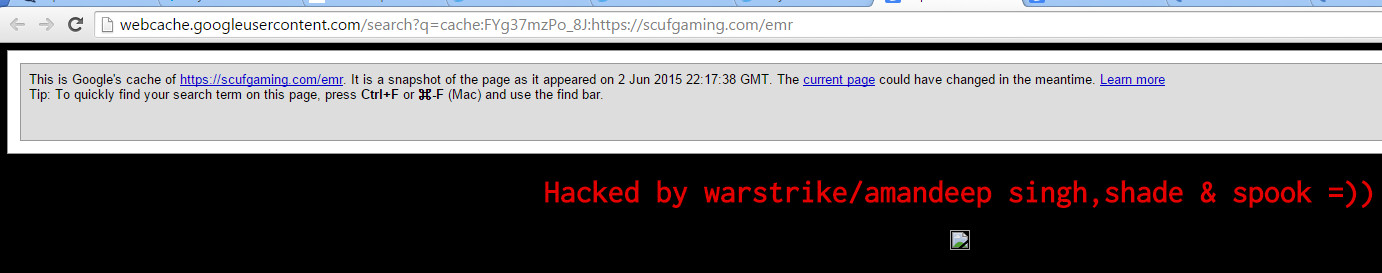
Popular makers of custom gaming controllers, Scuf Gaming, were recently notified by many service users that their website had been compromised like so:
It still lives on in Google Cache:
Hot on the heels of this, numerous Scuf customers report having been sent an email [1], [2], [3], [4], [5] which reads as follows:
Dear Scuf Gaming Customer,
There’s no word yet if they think the website hack and the data swipe are related – they could be entirely separate attacks,with multiple groups / individuals taking advantage of a way in to get up to mischief.
This is a fairly common pattern – a site running outdated software will be hacked, then another group will come along and replace the original defacement with one of their own.
At this point, your only way of knowing something might have happened is by having seen the email – I had a look at their Twitter feed and website, but there doesn’t appear to be any mention of the June 2nd “incident” or the website defacement.
One thing is for certain – if you have a Scuf account, you should definitely follow their advice and change your password, alongside making sure you’re not reusing the same login details elsewhere.
Password reuse is a major problem where keeping accounts safe is concerned, and there are even extensions available to assist in breaking this bad habit.
Many websites and services are compromised behind the scenes all the time, and you can bet that quite a few of them don’t bother sending anything out in terms of notification.
For as long as you don’t know a service has been popped, the people behind said popping have carte blanche to check for password reuse on your other accounts at their leisure. You can kill this threat to yourself off at the source by avoiding password reuse, and investing in a password management tool such as LastPass.
Go on – give yourself one less thing to worry about…
Christopher Boyd