It’s always interesting to identify the source of an infection, especially when it comes to exploit kits.
Beyond identifying the various parties involved, it also helps to better understand how cyber criminals are redirecting the traffic flow in ways that are harder to predict.
Malvertising is a prime example of multiple redirections away from the original site someone visited before being bounced around several networks that eventually lead to an exploit kit.
The case we are looking at today involves a couple of ad networks and malicious sites, one of which happens to be a copycat of a genuine gaming company.
This somewhat unexpected redirection chain lead to the Neutrino exploit kit which delivered the Bunitu Trojan.
Malvertising
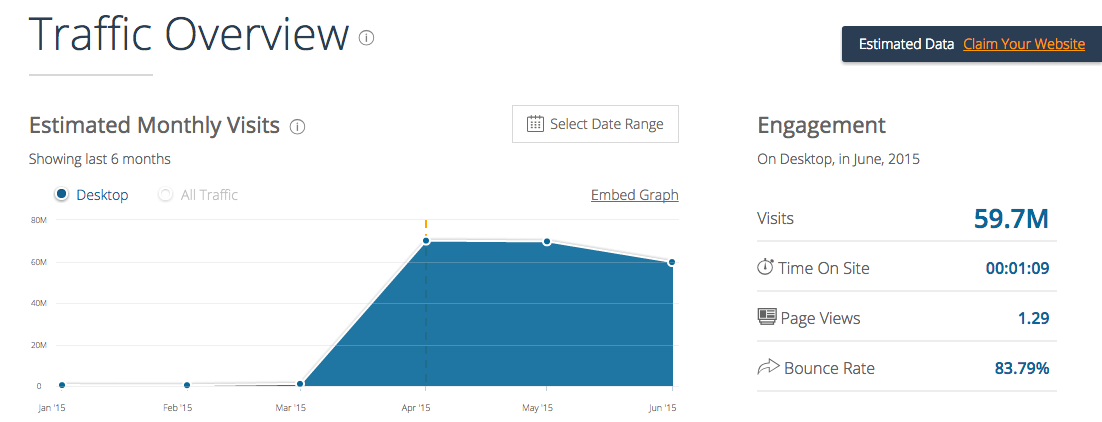
The first ad network caught in the malvertising attack is known as xmediaserve.com. While there is not a whole lot of public information about it, it serves a lot of content with close to 60 millions visits last month according to SimilarWeb.
Registrant Organization: WHOIS PRIVACY PROTECTION SERVICE, INC. 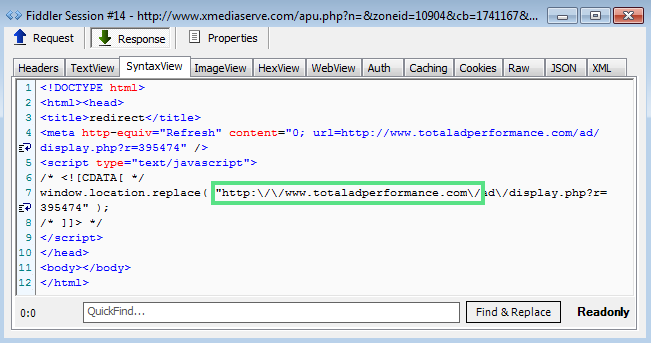
In this case, xmediaserve.com launches another ad platform called totaladperformance.com where once again very little information is available.
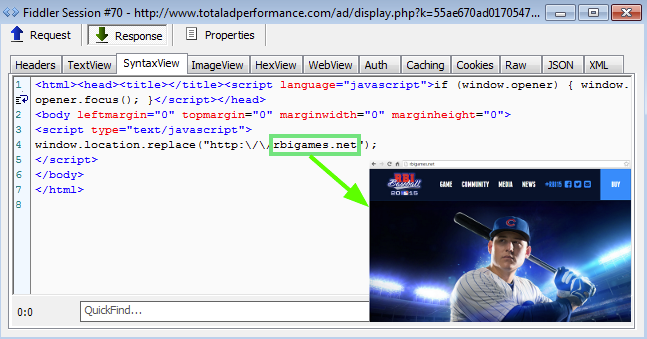
Registrant Organization: Domains By Proxy, LLC The latter advertisingserivce rotates ads ranging from fake Flash Player, to tech support scams. But if you keep spinning that wheel of (mis)fortune you may get something totally different, such as this gaming site, rbigames[dot]net.
At first glance, the site appears quite legitimate and promotes the latest iteration of a baseball video game (R.B.I. Baseball 15).
However something did not feel quite right with this. A quick search on the site’s registrant gave us a rather unexpected result:
Admin Email: dimitrlorion@gmail.com Registrant City: Moskva Registrant Country: RU
Why would the registrant be from Russia, when the site looks like it is related to MLB.com?
In fact, to further this theory, clicking on the Twitter link shows that the official site appears to be rbigame.com.
This time around the registrant details make more sense:
Registrant Organization: MLB Advanced Media, L.P. Registrant Street: 75 Ninth Avenue Registrant City: New York Registrant Country: US
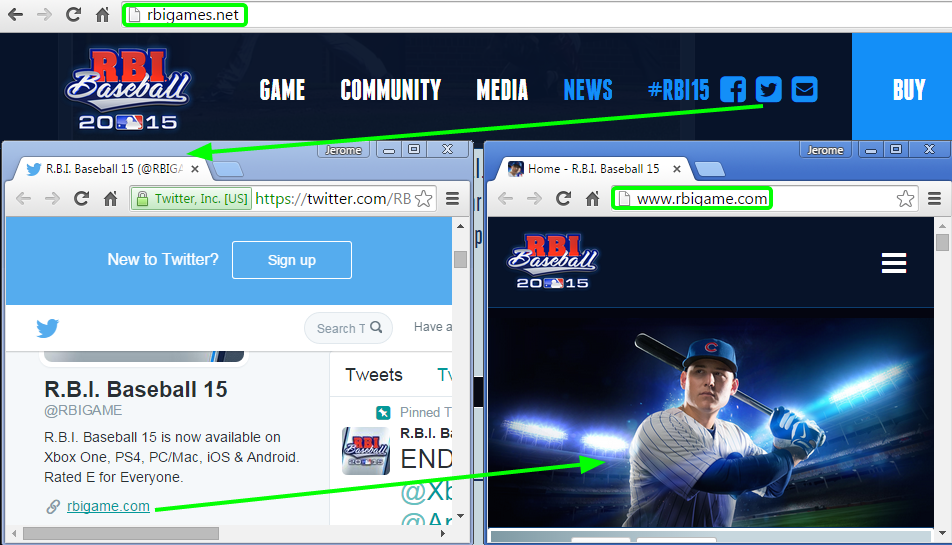
We confirmed with @RBIGAME that rbigames.net was not their site and that they were in the process of having it shutdown.
The copycat site is injected with a malicious iframe that loads a secondary iframe:
Neutrino exploit kit
This series of redirections takes us to the Neutrino exploit kit, which recently integrated new Flash Player zero-days:
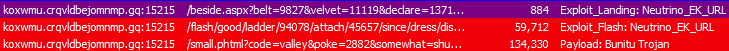
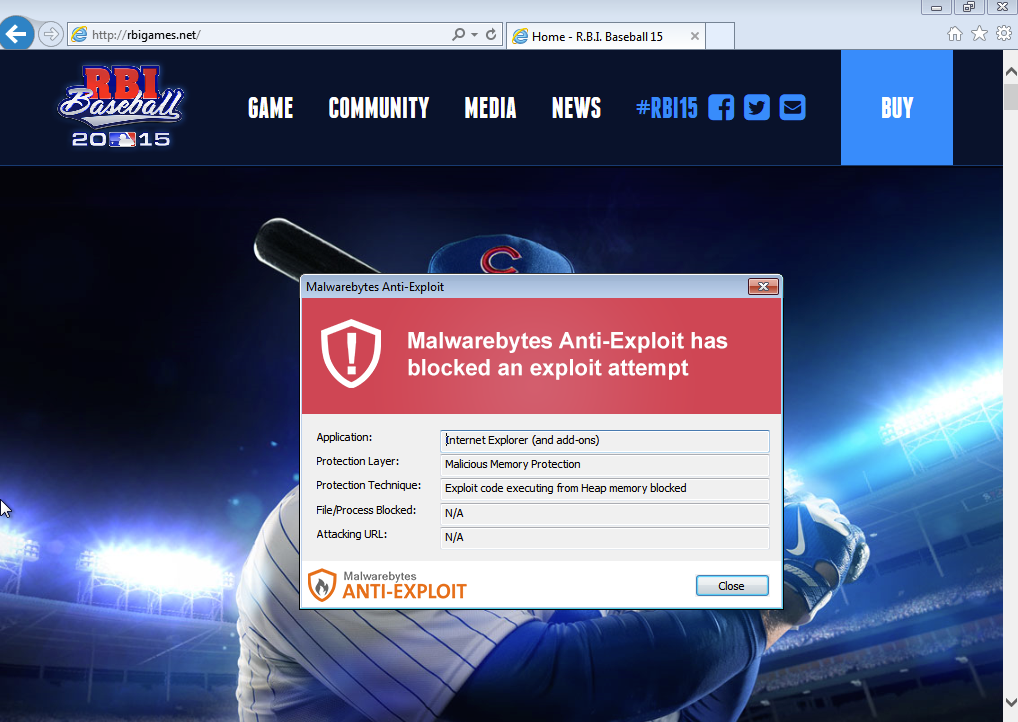
If exploitation is successful, a malware payload is dropped on disk via a script invoked by wscript.exe. The payload is no other than the Bunitu Trojan which we recently documented on this blog.
This malvertising chain was quite new to us and we don’t quite know for sure the purpose of the copycat site, unless perhaps it tries to make money from affiliate sales of the video game.
Malwarebytes Anti-Exploit users were already protected against this attack.