The same adserving technology platform – AdSpirit.de – which was recently abused in malicious advertising attacks against a slew of top media sites was leveraged again on MSN.com. This is the work of the same threat actors that were behind the Yahoo! malvertising.
The incident occurred when people who where simply browsing MSN’s news, lifestyle or other portals were served with a malicious advertisement that silently loaded the Angler exploit kit and attempted to infect their computers.
The ad request came from AppNexus, which loaded the booby-trapped advert from AdSpirit and the subsequent malvertising chain.
Infection chain:
- msn.com/en-us/news/politics/dozens-of-clinton-emails-were-classified-from-the-start-us-rules-suggest/ar-BBlXPkl?ocid=iehp (publisher)
- lax1.ib.adnxs.com/{redacted} (AppNexus Ad network)
- pub.adspirit.de/adframe.php?pid=7&ord=[timestamp]prdclick_0 (AdSpirit Ad network)
- trkp-a1009.rhcloud.com/?tr28-0a22 (OpenShift redhat Redirection)
- fox23tv.com/?cn67CuYcDcbvV (Same ad but with redirection to malicious URL)
- abbezcqerrd.irica.wieshrealclimate.com (iframe to exploit kit)
- hapme.viwahcvonline.com (Angler EK landing page)
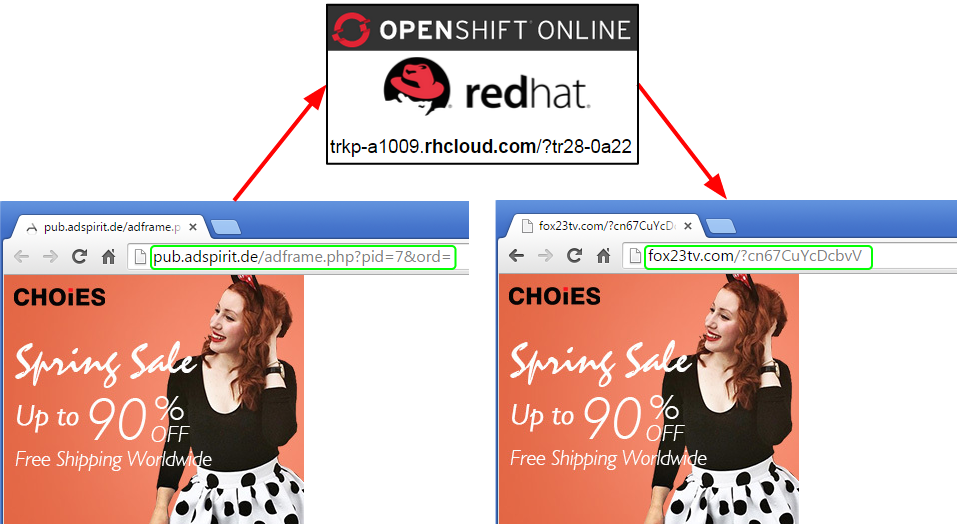
This time, rogue actors are leveraging RedHat’s cloud platform, rhcloud.com to perform multiple redirections to the Angler exploit kit (in the previous attack they were using Microsoft’s Azure).
While we did not collect the malware payload associated with this campaign, we believe it is either Ad fraud or ransomware, Angler’s trademark.
Angler has been acting up strange lately, for instance last week it fell out of favour briefly for the Neutrino EK when compromised sites decided to redirect to the latter.
Following our report, AppNexus deactivated the creative in question and said they were investigating this issue in greater depth.
Malwarebytes Anti-Exploit users are already protected against this attack.