Browsefox aka Sambreel aka Yontoo is a family of browser hijackers. When advertised they promise to “customize and enhance your interaction with the websites you visit”, but in reality they are almost never a users choice install. They come bundled with other software at many major download sites and at best you will see this screen when the installation starts.
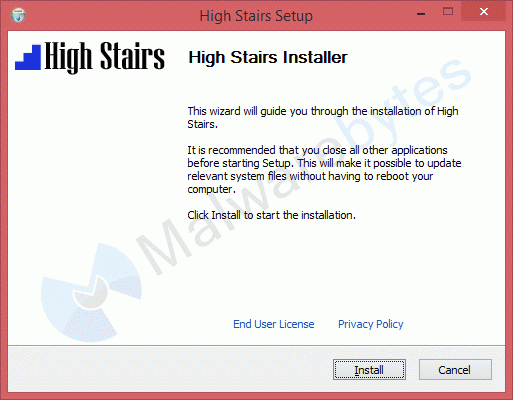
High Stairs is one of the latest additions to this family.It is being offered as a browser extension without making clear what it does for the user.
If you want to have a look at the EULA and Privacy Policy you will have to visit their website.

The software is free to use, but is supported by advertising (including banner, browsing-related, transitional, text link, interstitial and full page advertisements).
Part of their site is blocked if you have Malwarebytes Anti-Malware Premium installed and Malicious Website Protection enabled.
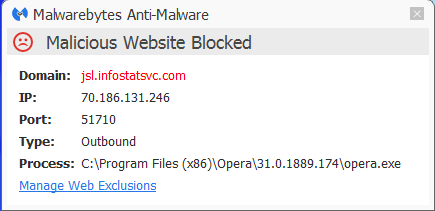
The EULA clearly states that it allows the “Software” to use any means imaginable to deliver advertisements and that it will collect your data. The Privacy Policy lets you know that they will use, share and sell those data to any and all parent, subsidiary or affiliate companies. Bottom line, as long as it brings in cash.
Browser hijackers of this family are VM aware, meaning they will not do a full install if they detect they are run on a Virtual Machine. Sometimes the files are downloaded and put in place, but the extensions are not installed and enabled.
The hijackers from this family do provide browser extensions for IE, Firefox, Chrome and Opera (and probably more).
Having a closer look at “High Stairs” in particular we found a string inside the Browser Helper Object (IE extension) that deserved a closer look.
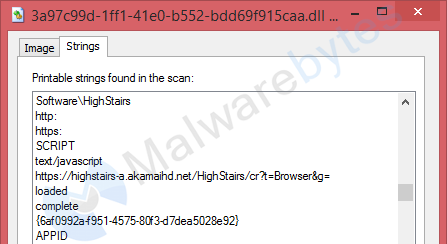
Following the URL visible in the screenshot, I downloaded cr.js which is a file containing JavaScript code. Looking at some of the code inside indicates that it creates a 1 pixel iframe.

These invisible iframes can be used to deliver anything and everything to your computer, ranging from advertisements (which is very likely in this case) to (in theory) exploit kits. In theory in this case means, that we haven’t seen any exploit kits being delivered through the advertisements these PUPs deliver, but if the PUP has a vulnerability or their network is compromised a third party could use this in the same manner as has been done with malvertisements on legitimate sites.
This browser hijacker is relatively easy to remove. Other variants have been known to install services as well, making them a bit harder to tackle. Unfortunately “High Stairs” is not alone. We see a new Sanbreel variant at least a few times every week.
The installer and the installed files are all detected as
PUP.Optional.HighStairs.A
Logs, more screenshots and removal instructions for “High Stairs” can be found on our forums.











