Phishing emails attempt to acquire your sensitive information – account information or passwords, for example – by masquerading as a legitimate source. For example, they might pretend to be a friend or a company you deal with – even a charity you support.
Here are a couple of examples I received last week – would you be alert enough to spot these?
The first example is from a charity I support, the YMCA. It actually contains, in the email signature, the executive director’s name, address and phone number. It looks legitimate!
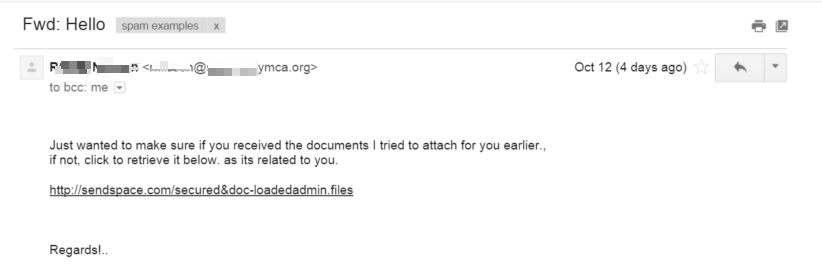
What are the clues that this email is not legitimate? There’s one big one. If you hover over the link to sendspace.com, you see a different URL entirely:
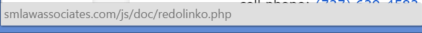
(Note: This assumes you have the status bar enabled in your browser, which is a good practice for security; search for “preview links in
Another option would be to view the text form of this HTML email. In Gmail, you press the down arrow to the right of the message, and click on “Show Original.” Sure enough, if we search down for the sendspace.com link, we get
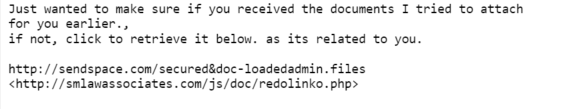
which shows you that the link is not legitimate.
Many security analysts such as our own Steven Burn recommend always viewing HTML email in plain text, and not HTML or RTF.
To learn about how to view HTML emails in plain text in your email client, you can search for “Read email messages in plain text in
But how was a bad guy able to send this email from the YMCA? A quick phone call to the owner of the email confirmed that their email account had indeed been hacked and used to send spam.
The second example was from a friend in trouble … or so I thought.
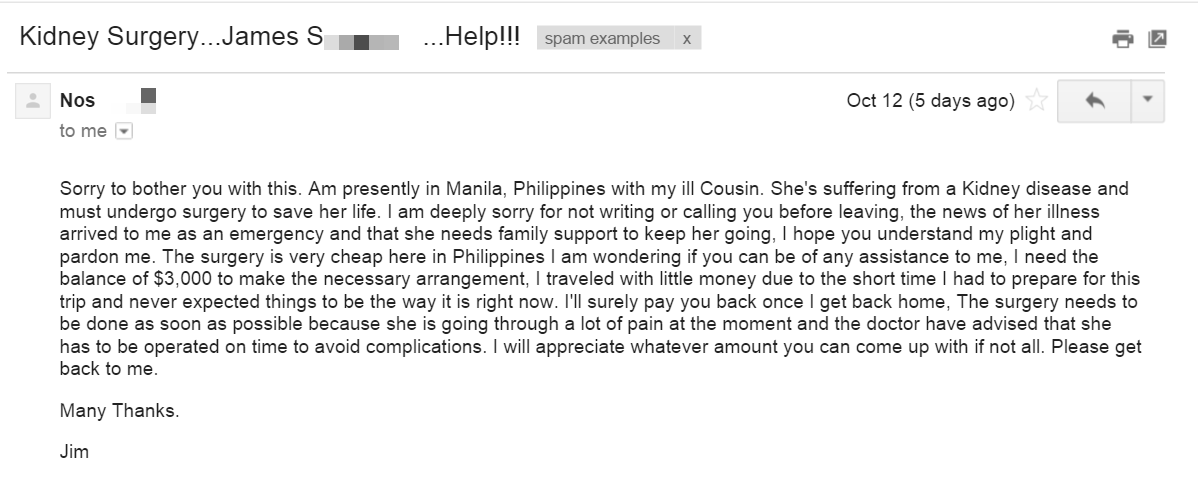
Now I laughed when I read this, since my friend Jim is a wealthy man who would have $3,000 in the pocket of the bespoke suit he wore while traveling, but let’s leave that aside.
This email has the standard pattern of a 419 scam, which we have written about extensively on this blog.
“419” refers to the section of the Nigerian criminal code which addresses this sort of activity, Nigeria being a common source of these kinds of frauds in recent years. The mark is asked for an advance payment to cover a crisis, and a promise is made for future repayment.
I did a reply and looked carefully at the email address shown in the “To:” section. Notice how it starts with “n0s” instead of ”
nos
Let’s conclude with summarizing what can we learn from these two examples.
- The most secure way to operate email is with HTML formatting off. Now for many people, this is a bridge too far, but a compromise is just to familiarize yourself with viewing plain text email in your client, and just doing that when you get something unusual.
- You should always hover over links and pay attention to the actual link target (shown at the bottom of your browser), which might differ from what is shown on the page. Indeed, if it does (i.e. the page says http://site1.com, and the hover text at the bottom of the browser says http://site2.com, that’s a clear indication of trouble.)
- Anytime you receive an email which exclaims that a crisis of some sort has arisen, take an extra moment to double check it. Look at the return address which is shown when you reply to it, for example.
Phishing attacks are a common occurrence in our modern era of connectivity, and cyber criminals know that the best way to get around technical protections is to exploit the user.
By keeping a vigilant eye on what you are clicking, receiving and downloading, you can help make the Internet a safer place, one e-mail at a time.











