There has been a lot of buzz about the powerful Angler Exploit Kit in recent days. One thing is for sure, the gangs using it are extremely resourceful and won’t let attempts at slowing them down get in the way.
We detected an attack that happened via a sophisticated malvertising campaign we had previously documented on this blog: the SSL malvertising attack via Microsoft Azure.
Malvertising works by inserting a malicous advert within a publisher’s website. When the page loads, the ad is displayed and performs its nefarious action without the user having to click on it.
This time it struck on popular British newspaper the Daily Mail which accounts for 156 million monthly visits according to SimilarWeb. The malicious ad would have been displayed to a fraction of its users during the timeframe of the attack which we first caught Friday and was addressed by Monday morning.
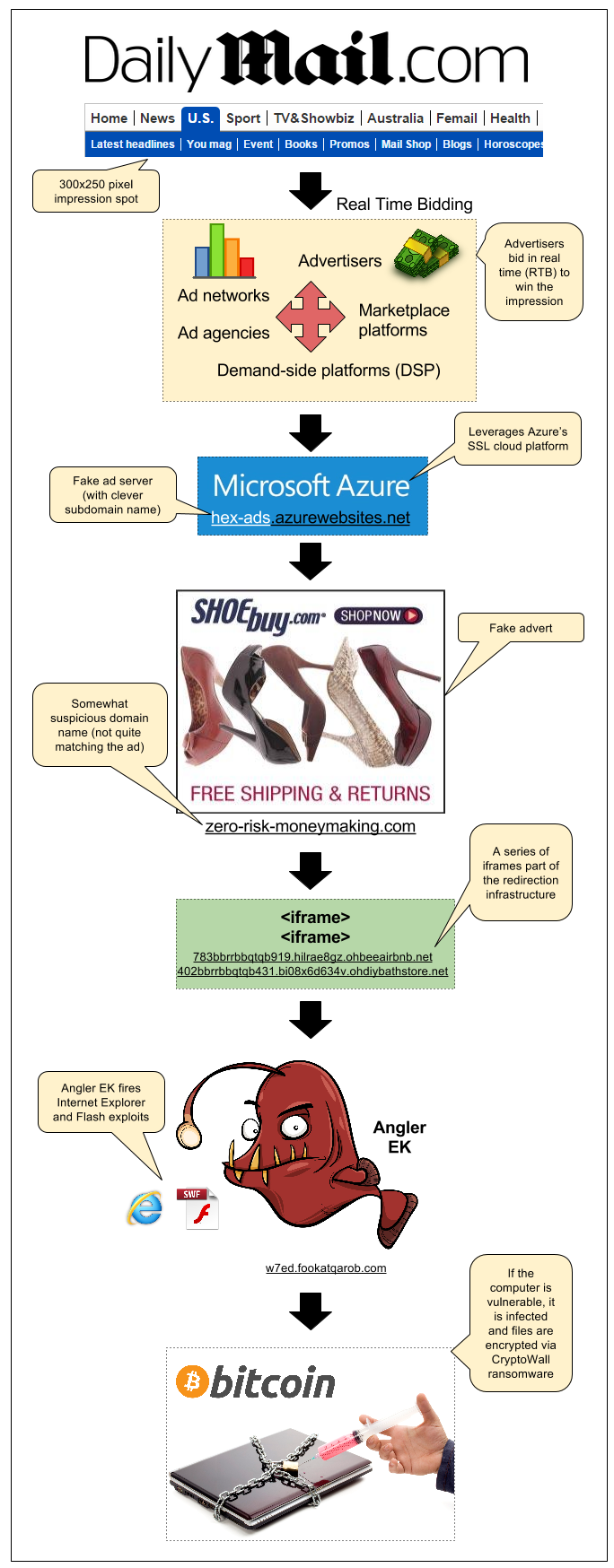
Infection flow:
- Publisher: dailymail.co.uk/ushome/index.html
- Ad call: www5.smartadserver.com/ac?out=js&nwid=1546&siteid=81193&pgname=sf300s&fmtid=35210&tgt=[sas_target]&visit=m&tmstp=[timestamp]&clcturl=http://pixel.mathtag.com/click/img?mt_aid=5829942979381995373&mt_id=1859987&mt_adid=148298&mt_sid=956001&mt_exid=9&mt_inapp=0&mt_uuid=90555615-e26a-4d00-8f31-09247eb00069&mt_3pck=http%3A//beacon-us-iad2.rubiconproject.com/beacon/t/ef1e4098-f217-4beb-8644-01803c6d7545/&mt_lp=http%3A//www.shoebuy.com/new-womens-shoes.htm%3F5DCjbVsxF67hxMc&redirect=
- Fake SSL ad server (malvertising): hex-ads.azurewebsites.net/?=awefyg677873jk2o
- Fake advert for shoebuy.com (malvertising): zero-risk-moneymaking.com/?vC237XnBcMvp
- iframe(1): 783bbrrbbqtqb919.hilrae8gz.ohbeeairbnb.net/287e1e7f185ac57172a0a7b70483e
- iframe(2): 402bbrrbbqtqb431.bi08x6d634v.ohdiybathstore.net/ced1d59c80127f0fb50e6e083d3
- Angler Exploit Kit: w7ed.fookatqarob.com/boards/viewforum.php?f=61ls0&sid=826888i5.161802rr6070
Malvertising has been one of the main infection vectors and continues to affect large publishers and ad networks through very distinct campaigns, very much like a whack-a-mole game.
In addition to spreading via compromised websites, Angler EK leverages malvertising thanks to several different threat actors who use clever ways to go undetected as long as possible or are able to quickly adapt and get back on their feet if one of their schemes gets too much attention and is disrupted.
During the past months we have been working very closely with ad networks, publishers, cloud providers and other companies that have been abused by these attacks.
In addition, we hope that well documented cases such as this one help consumers to realize that malvertising is a very dangerous and yet often misunderstood threat. There is no such thing as a safe website anymore and it is everyone’s responsibility to ensure their devices are fully patched and well protected.
We contacted the affected publisher (DailyMail) and related ad networks right when we found out about this incident. On 10/12, we were informed by MediaMath that the malicious creative had been disabled.
Malwarebytes Anti-Exploit users were already protected against this attack, thanks to its proactive exploit mitigation capabilities.