Update (11/19/15): The hosting provider, AdvancedHosters, replied to our complaint. They have servers in the US and also around the world but are based in The Netherlands.
“According to our investigation, the customer has not been involved in hacking/running malicious scripts/malware distribution activity. If you require further information, or have any questions, please do not hesitate to contact us. Regards,” AdvancedHosters Customer Support
No comments, the evidence speaks for itself.
This case is very strange to say the least and it is possible that there is an ulterior hidden motive behind it which we are still investigating.
– –
The year is 2015 and a threat actor is using the defunct Blackhole exploit kit in active drive-by download campaigns via compromised websites.
We noticed Java and PDF exploits collected by our honeypot which we haven’t seen in ages. Looking closer at the structure of this attack, we were surprised when we realized this was the infamous Blackhole.
Blackhole’s author, Paunch, was arrested in October 2013 and while criminals kept using the kit for the next few months, the exploits slowly deprecated and lost value because of lack of development.
The new drive-by download attacks we caught over the weekend rely on the same structure as the original Blackhole, even reusing the old PDF and Java exploits. The only difference is the malware payload being dropped, which is current and had very low detection on VirusTotal.
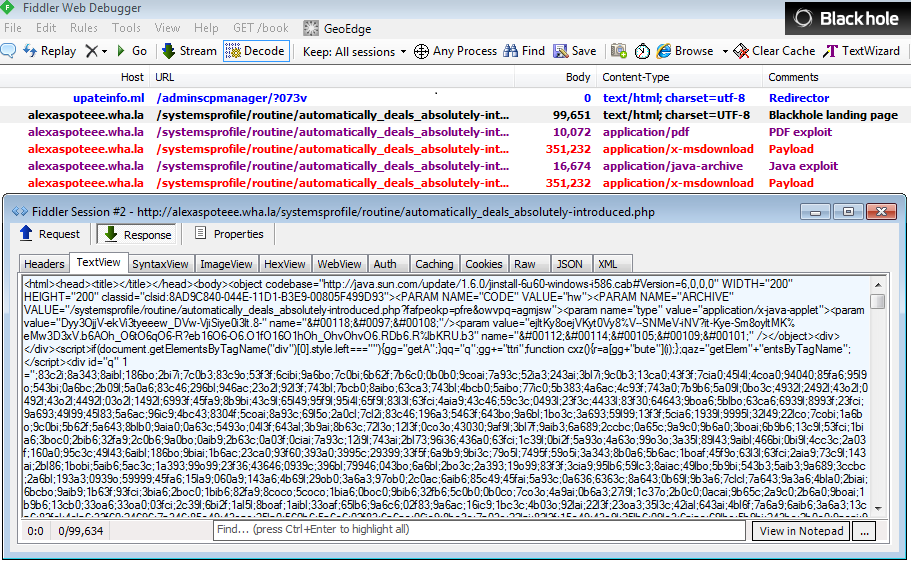
The server used to host the exploit infrastructure happens to be fully browsable (thanks @MeJz024 for the tip). The folder structure shows with no doubt this is taken straight from the Blackhole source code that had been leaked.
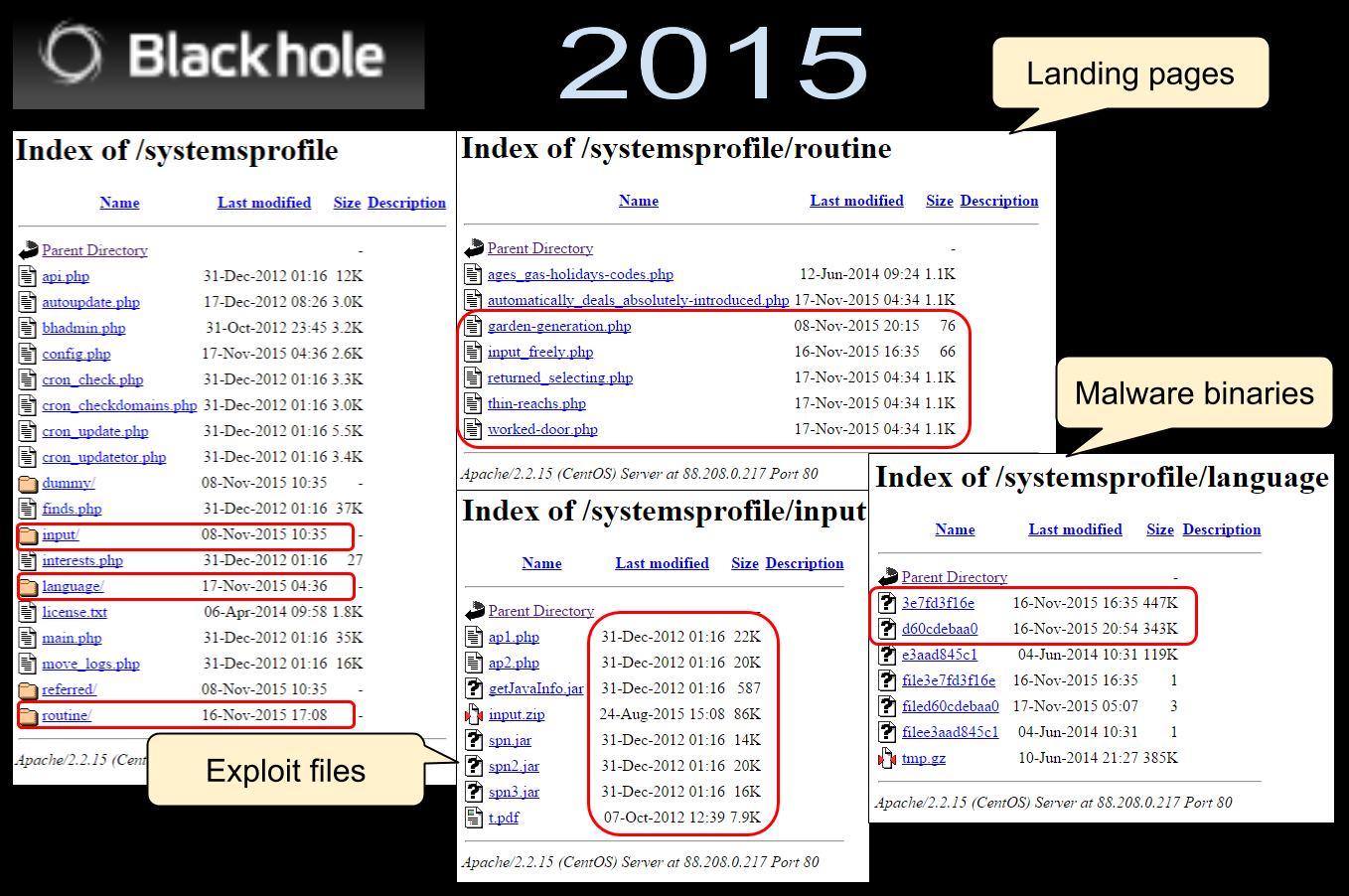
Although the exploits are old, there are probably still vulnerable computers out there who could get compromised. We also noticed that the author behind this Blackhole edition was working on new landing pages, so it is possible there might be additional changes in the future.
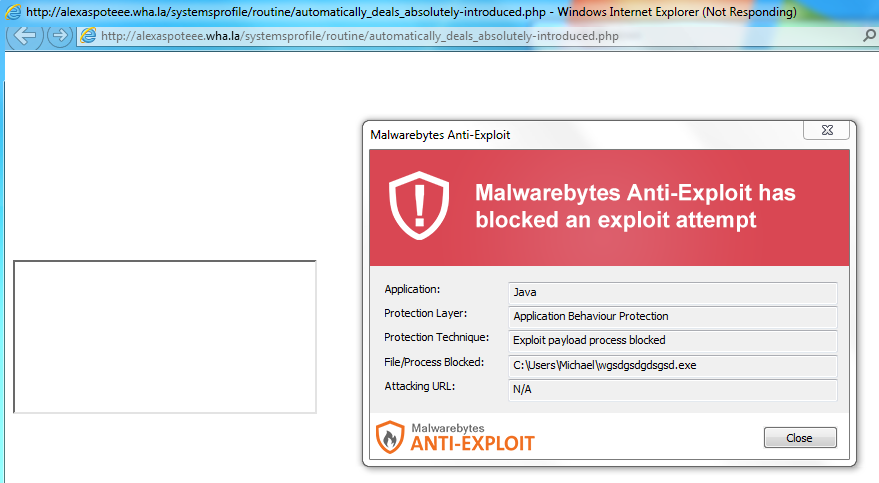
Malwarebytes Anti-Exploit protects users against this attack, despite the exploits being very dated.
We are not quite sure why this old exploit kit is being used in live attacks considering the infection rate would be quite low due to the aging exploits.
One hypothesis could be that the source code being public, it is a free platform that can be built upon and updated.
Indicators of compromise
Server IP: 88.208.0.217
Domains:
- updatewindowsplayer.ga
- updatewindowsplayer.gq
- 1qw2.wha.la
- qwe2345.wha.la
- alexaspoteee.wha.la
- alexaspoteee.epac.to
- s-mx.com
- www.s-mx.com
:
- e2866f9d234f67e2e8349416d923cc5e
- b556f7449178a06257ad6c97b8f52cb1
- 1afb93d482fd46b44a64c9e987c02a27
- fdf894411559d1c30c39ee92faed6efe










