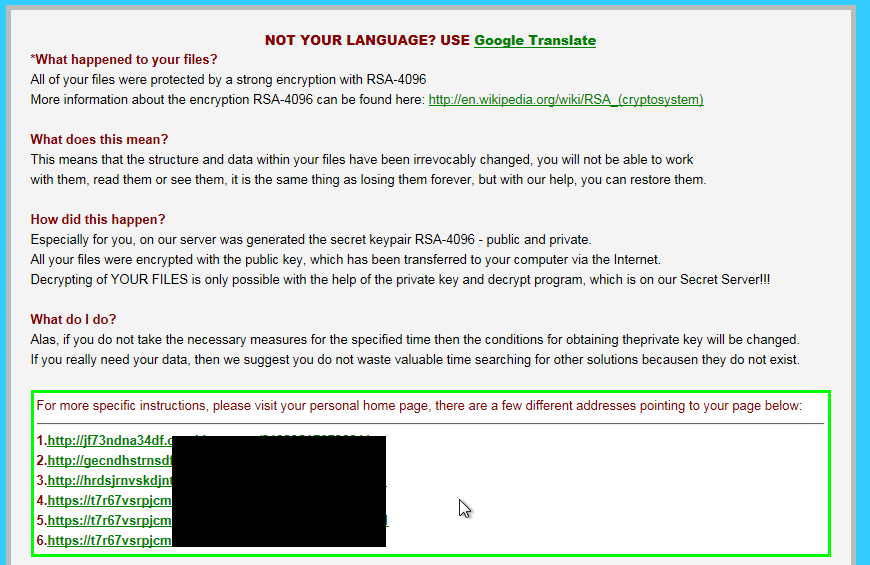
On December 18, security company Fortinet blogged about a possible new variant of the CryptoWall ransomware distributed via spam. Around the same time we discovered that the Angler exploit kit was also pushing this new ‘variant’. However it is not CryptoWall (thanks Yonathan Klijnsma for the tip) but rather TeslaCrypt.
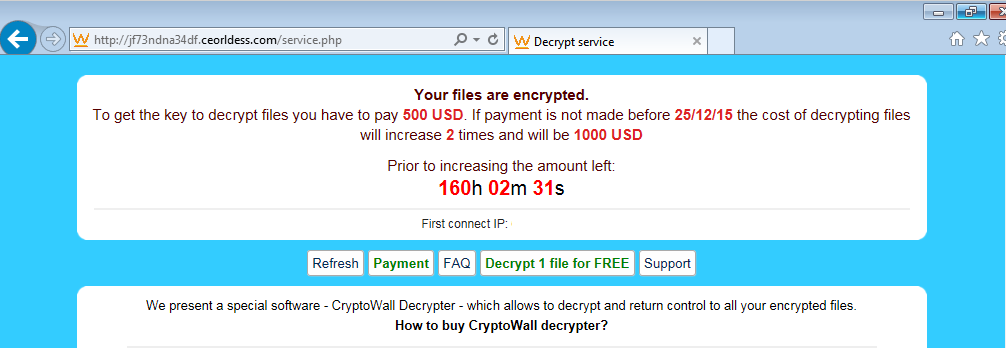
Files are encrypted and appended with a .vvv extension. In order to recover those files, victims must pay $500USD or face the risk of seeing this amount double within less than a week.
Your files are encrypted.To get the key to decrypt files you have to pay 500 USD. If payment is not made before 25/12/15 the cost of decrypting files will increase 2 times and will be 1000 USD
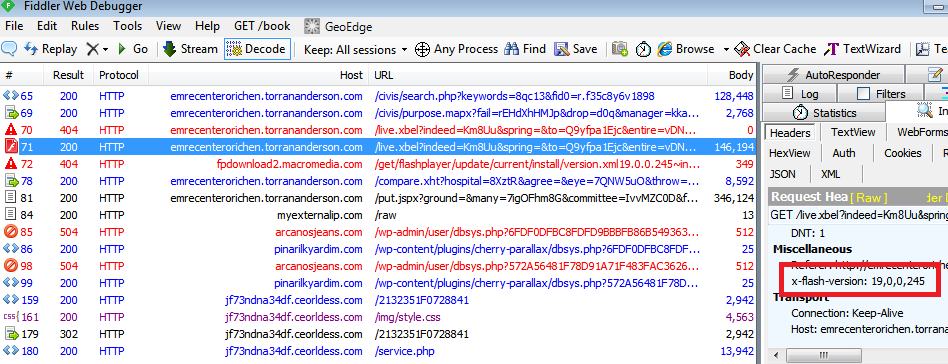
Angler EK uses a very recently patched flaw in Adobe Flash Player up to version 19.0.0.245 (CVE-2015-8446), making it the most lethal exploit kit at the moment.
Ransomware is one of the most prolific and devastating pieces of malware users have had to deal with in recent years.
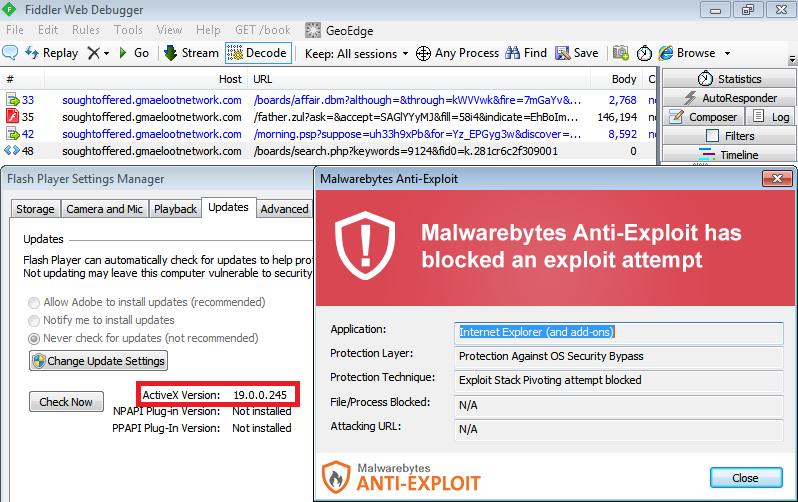
Malwarebytes Anti-Exploit blocks this particular attack via Angler while Malwarebytes Anti-Malware detects the malware binary (VT 2/55).