As reported by F-Secure, a recent malvertising campaign has been hitting several top publishers to push the Angler exploit kit and install the TeslaCrypt ransomware, according to the Finnish company. Some of these infections happened via Skype, which displays ad banners within its product.
We looked into the redirection mechanism and identified that these attacks came from a rogue advertiser abusing the AppNexus platform, and which was performing conditional forwarding to rotating Angler EK domains.
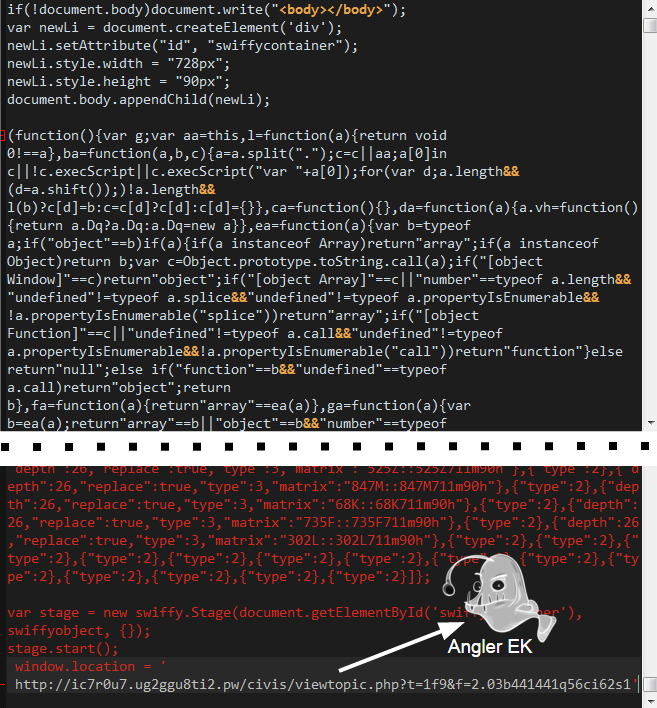
Rogue domain: hueyscatering.com/cTRVRZgacCqj6V0XrysHCkZPZC1QPx -> Angler EK landing page: ic7r0u7.ug2ggu8ti2.pw/civis/viewtopic.php?t=1f9&f=2.03b441441q56ci62s1
The advertiser used a domain that at one point belonged to a catering company, before it expired and was reutilized in these attacks.
The redirection to Angler is done server-side with threat actors having full control of who will or won’t be served the exploit kit.
The malicious code resides in an unusually long JavaScript file perhaps intended to confuse security scanners.
This attack was reported and blocked by Malwarebytes Anti-Exploit.










