While investigating a recent malvertising incident we were stumped trying to identify the exact infection chain. We talked to the publisher which was positive they never used a particular ad provider which made it more difficult to figure out what was taking place.
A closer look at a network capture revealed something odd which ultimately lead to uncovering the whole thing. Additional code was injected into certain browser sessions from a program called Wajam, marketed as a “social search” browser add-on.
One of the things Wajam does is that it injects ad banners into existing web pages, in addition to the regular adverts. Below you can see Wajam inserting a deceptive advert saying “Please Fix Your Windows Errors” on popular kids portal pbskids.org (at least they used the word please).
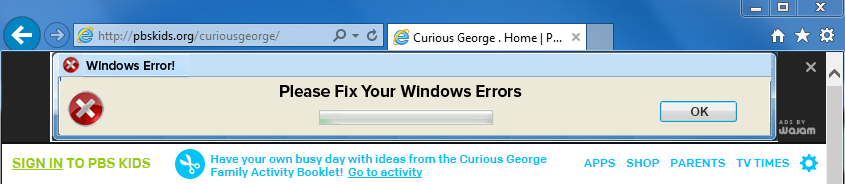
The problem with this business model (especially with low quality ads), is that sooner or later something bad is bound to happen. Case in point, the following malvertising attack infected users because they had the Wajam browser add-on that loaded an advert via the Adk2x (Plymedia) ad network:
- Publisher (scripts are injected)
- trudeautechnology.com/jsonp/searchengine/contentSiteSetup.json?se=content_site&unique_id=FA321934ED6F5E58A3F1B6D0DAC99550&{redacted}
- adstract.adk2x.com/imp?p=70540033&size=728×90&ap=1300&ct=html&u=http%3A%2F%2Fwww.{redacted}.com%2F%3Futm_campaign%3D{redacted}&r=http%3A%2F%2Fwww.{redacted}.com
- {redacted} .com/writing/opportunity/western/butter.html?click=%2F%2Fadstract.adk2x.com%2Fclick%2FS5U30_4RngIpwoqgKRBYSkfxsy-Doy0V_LxTAyow–T0MF4CNigy4QehvhEH9abrGaQmhN-4bVZa1VTworujUYWYGguyDJxbL
- Angler EK

We reported this and other incidents to PLYmedia which are related to the same recent wave of malvertising attacks we have been observing.
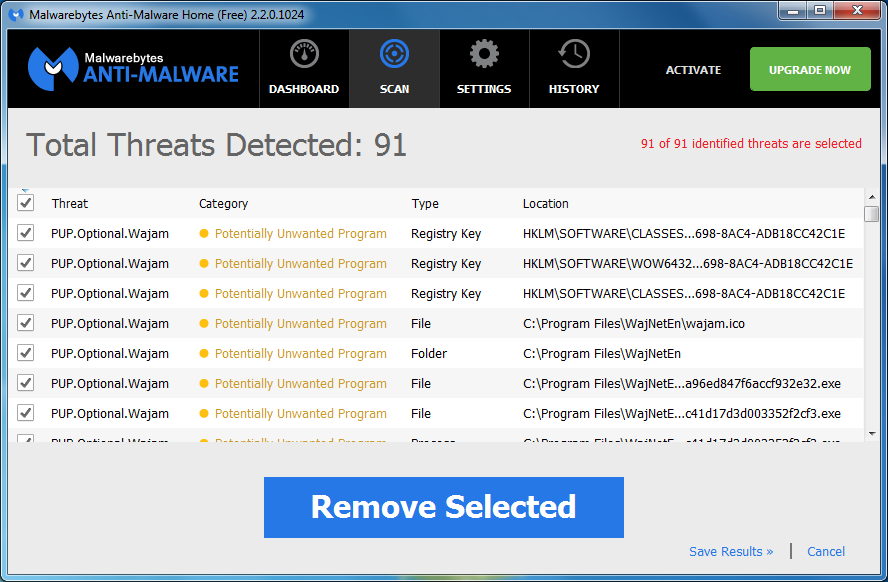
Malwarebytes Anti-Malware detects Wajam as a Potentially Unwanted Program (PUP.Optional.Wajam) while Malwarebytes Anti-Exploit blocks the drive-by download attack.










