Gumtree is a free classified advertising site and subsidiary of eBay particular popular in the UK, Australia, and South Africa. Gumtree is the number one local classifieds in Australia with 47.8M monthly visits* and was recently affected by a malvertising attack.
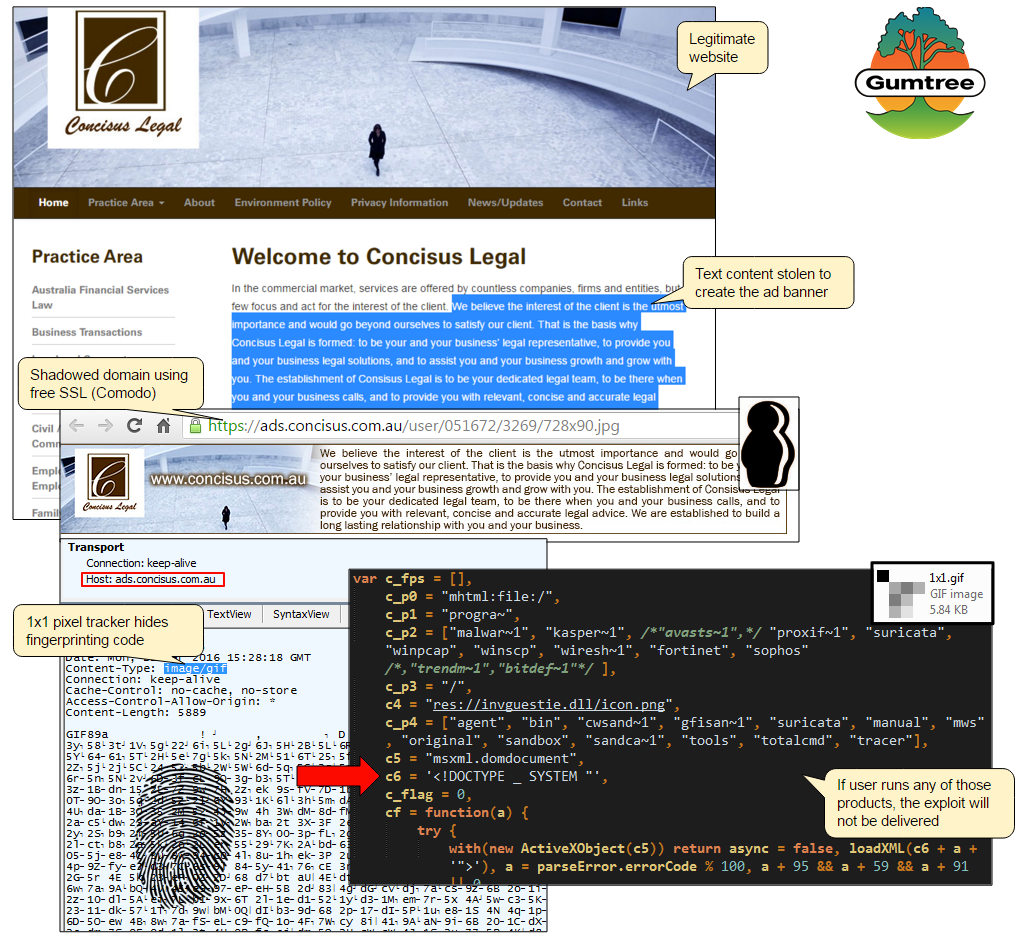
Threat actors hacked the account of an Australian legal firm called Concisus Legal to create a legitimate looking but fraudulent subdomain off their main server.
Legitimate domain:
Hostname: concisus.com.au IP address: 203.170.87.121Rogue advertiser
:
Hostname: ads.concisus.com.au IP address: 46.165.218.138
In addition to using a different server infrastructure, the fraudulent advert is served via HTTPS, while the legal firm’s site is only using plain HTTP. This is a technique we have observed several times before.
The rogue advertisers simply lifted the company logo and some text from their website to create what looks like a typical ad banner. They then approached ad networks and pretended to want to advertise under the disguise of the victims they abused.
By alternating between clean and malicious versions of the same ad banner, these crooks can dupe the ad industry and carry out their attacks in stealthy ways. Like previously, we see the same fingerprinting approach that tries to detect and avoid machines running certain security tools or network packet captures.
The malvertising sequence went like this:
- Publisher: gumtree.com.au
- Ad network: sin1.g.adnxs.com
- Advertiser (rogue): ads.concisus.com.au
- Exploit Kit: Angler EK
Those who were exposed to this malvertising attack would be facing the Angler exploit kit which can drop a range of different payloads such as ransomware or banking trojans.
We immediately reported this incident to AppNexus which responded within a few minutes and deactivated the rogue account. We also alerted the abused Australian law firm about this breach.
* Number from SimilarWeb.com