Update (04/29): Maisto[.]com is now in maintenance mode to fix the issue. We appreciate the prompt reaction and doing the right thing to protect the site’s visitors.
The website of popular American brand Maisto, known for miniature and radio-controlled toy vehicles, was caught pushing the Angler exploit kit eventually leading to ransomware infections.
According to website security company Sucuri, maisto[.]com is running on a Microsoft IIS server and showing an outdated version of the Joomla Content Management System, therefore exposing itself to automated hacks.
Malicious code was injected directly into the homepage and bears the same pattern as the pseudo-darkleech campaign, also discovered by Sucuri. Brad Duncan wrote a nice piece titled “Campaign Evolution: Darkleech to Pseudo-Darkleech and Beyond“, which shows how the attack that once only affected Apache servers also targets Microsoft IIS.
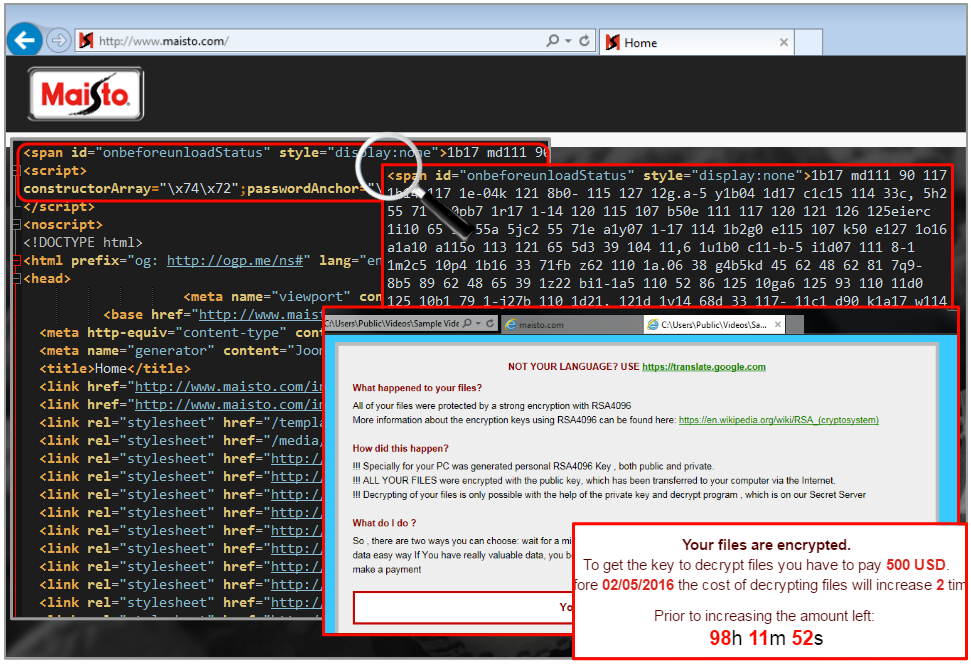
We replayed the attack in our lab and were served the Bedep version of the Angler exploit kit. The fileless loader proceeded to install the CryptXXX ransomware, first identified by Proofpoint researchers.
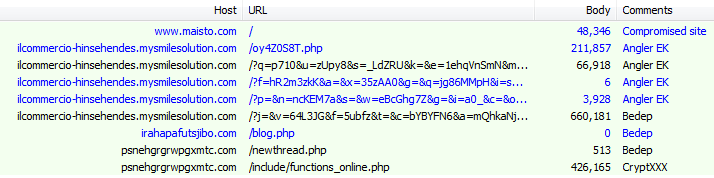
Traffic overview:
Despite the authors’ claim “So , there are two ways you can choose: wait for a miracle and get your price doubled, or start obtaining BITCOIN NOW! , and restore your data easy way. If You have really valuable data, you better not waste your time, because there is no other way to get your files, except make a payment“, there is a tool you can use to decrypt your files.
We contacted Maisto but have yet to hear back from them. In the meantime, users should ensure that their computers are fully up-to-date and remove unnecessary or risky plugins such as Flash or Silverlight. We also recommend an additional protection layer against exploits.
IOCs:
- Maisto’s homepage (also includes spam content at the bottom): pastebin.com/raw/fXLEPiAj
- CryptXXX: 0c6a15e0f78774a49d94653db0fbd1135b000c48527df5f1f820668065d9fff1










