A well known malvertising gang famous for its use of the fingerprinting technique and other evasion tricks to bypass security checks has been ramping up its activity against many different ad platforms to push malware via top websites.
The setup for these malvertising attacks relies on a combination of techniques that start with the fraudulent advertiser choosing a victim, typically a legitimate website in the retail, or legal business. The goal is to use someone else’s identity to appear legitimate when approaching ad networks.
The ad banners are designed professionally by the miscreants and then hosted along with the ad code on shadowed domains. The owners of said domains are completely unaware that a subdomain has been created on their hosting platform, let alone that it is serving malicious ads.
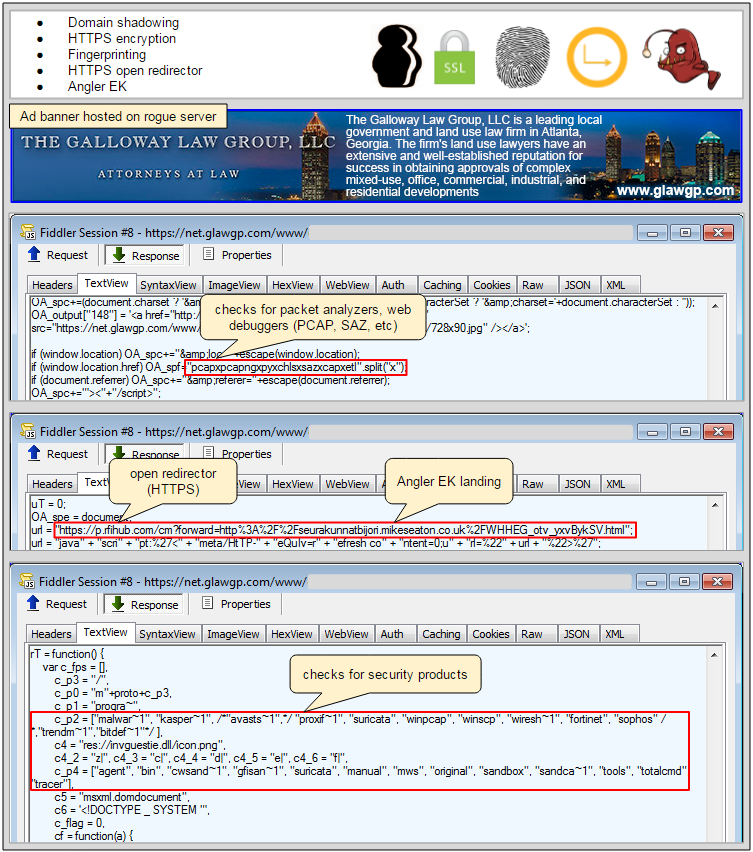
Here is the interesting part though. The ads are typically clean of any malware for anyone trying to manually verify them. The JavaScript code looks benign no matter how many times you refresh the page or rotate IP address. This is because the rogue version of the JavaScript is served conditionally, with the proper referer, user-agent, sometimes even your screen resolution, and several other parameters.
Once a genuine user is identified (a victim that happened to browse a particular publisher serving that ad), another series of checks – which we call fingerprinting – is performed to ensure that only those that are likely to get infected are indeed redirected to the Angler exploit kit.
Recently, researchers at Proofpoint identified a small but noteworthy change in the redirection mechanism to Angler. Rather than using the Google DoubleClick HTTPS open redirector, threat actors switched to programmatic marketing platform Rocket Fuel’s (rfihub.com). Perhaps this was decided as a result of increased scrutiny on the DoubleClick redirector, but regardless, it serves their goal of launching the exploit kit URL in an encrypted manner, making it more difficult for security companies to identify attacks.
Below are some popular websites that we identified in our telemetry, inadvertently serving the malicious ad banners via one of several ad platforms (Rocket Fuel, PLYmedia, Zedo, AppNexus, ShareThrough, Rubicon, DoubleClick) eventually leading to the Angler exploit kit.
- dailymotion.com
- kijiji.ca
- vodlocker.com
- answers.com
- cda.pl
- cbssports.com
- m.mlb.com
- legacy.com
- thechive.com
- cbs.com
* Ranked by monthly traffic according to SimilarWeb.com. Note that each site served a varying number of impressions of those malicious ad banners.
Angler EK converts visitors exposed to the malicious ads into ransomware victims via its own CryptXXX product. An aggravating factor in this case is the fact Angler is using a very recently patched Flash Player exploit (CVE-2016-4117). This entire sequence does not require any user interaction at all. As soon as soon as the advert gets displayed, the exploit redirection and infection automatically take place.
- pix.canadianhedgewatch.com
- front.business-mastery.ca
- net.glawgp.com
- pixels.respondez.co.uk
- ads.sicurauto.com
- probe.registermyserviceanimal.com
- dy.wwcpga.com
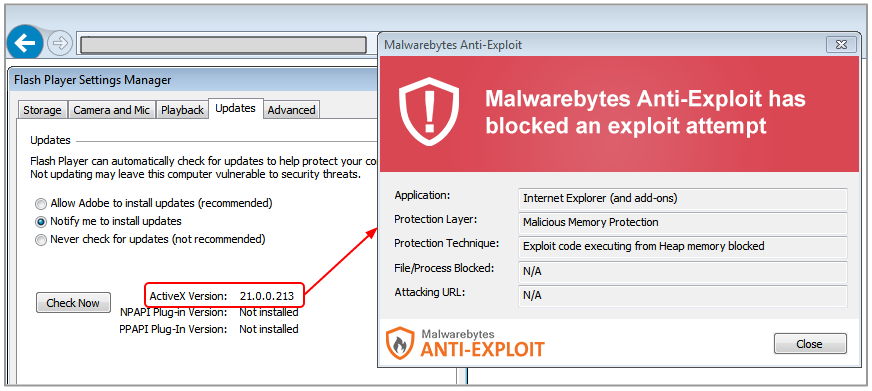
Malwarebytes Anti-Exploit detects the malicious banners and also blocks the latest Flash exploit (CVE-2016-4117):
We are pleased to say that we received quick acknowledgements from almost all the ad networks involved and that they have already taken measures to ban the fraudulent advertisers and their purveyors.










