As we’ve seen in other recent examples [1], [2],[3] Tech Support Scammers are using every trick in the malware authors book to get new “customers”. Here is one that takes over the victims’ Windows system after a reboot by using the Winlogon-Shell registry value.
Shell registry value
Under default circumstances the registry value looks like this:
[HKEY_LOCAL_MACHINESOFTWAREWow6432NodeMicrosoftWindows NTCurrentVersionWinlogon] (64 bits OS) or [HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionWinlogon] (32 bits OS) “Shell”=”explorer.exe”
This makes sure that the user gets access to his Taskbar and Desktop (among other things). It can be changed by so-called skins or replacement shells with the users’ consent, but in this case it was done without consent.
The value was changed to:
“Shell”=”C:Program Files (x86)ProductkeyupdateProductkeyupdate.exe”
As a backup the same was done under the HKEY_CURRENT_USER branch of the registry. So if you manage to change the value under HKEY_LOCAL_MACHINE the user that ran the installer will still be affected. This resulted in this screen after the user logged on:
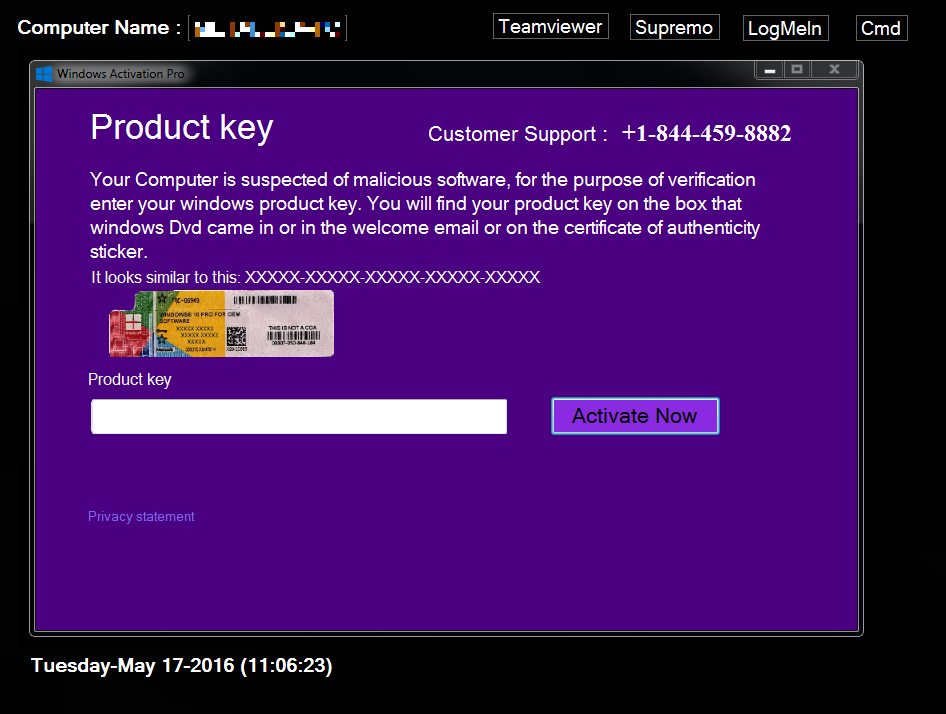
Due to the lack of the Windows Taskbar the average user will feel quite helpless, but the Tech Support Scammers left an opening, most likely for their own use and designed to make the users feel they actually got some money’s worth. More about that later.
The installer
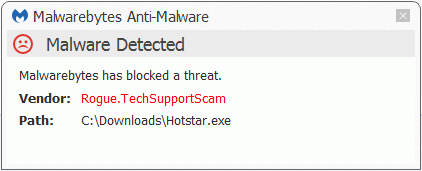
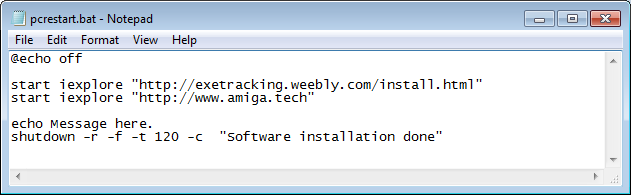
The installer is a file called Hotstar.exe and was submitted to us by a fellow researcher. We suspect the file was hosted on the site amiga[dot]tech, because of two reasons. The installer opens two browser windows and one of those queries that site. The other one opens up exetracking.weebly.com, a site that can be used to keep track of the number of installs, but the account of this author was suspended a few weeks ago. The other reason is that amiga[dot]tech still hosts a file called Hotstar.exe, but this one installs a fake registry cleaner. (The type that finds 896 infections in 0.2 seconds on a clean Virtual Machine.)
After opening the two browser windows the installer tells you it’s done-
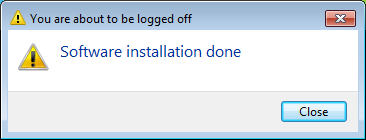
– and it triggers a reboot of the system, no doubt to force the user to find the Tech Support Scammers screen after they log on.
The escape
Looking at the Tech Support Scammers screen you will notice a few options.
- One is to enter your product key and Enter, which is not recommended since it could be sold to who knows who. (We tried a false one, but nothing happened.)
- The Teamviewer button takes you to the Teamviewer website. Teamviewer is a legitimate software that enables remote control of systems. This is often used by Tech Support Scammers and real Techsupport people to look at remote systems and remedy problems (or steal information and make things worse).
- The same is true for Supremo and LogMeIn. Both are software packages used for remote control.
- The button labeled Cmd is the one that makes us happy, since it opens a Command Prompt.
That makes us happy since it offers us a way to get back control over the system. In theory we can undo all the changes the installer made and clean the machine manually. But it is a lot easier to remove the file that replaced explorer as the shell, then reboot and let Malwarebytes Anti-Malware handle the rest.
Note that Windows will restore the default registry HKEY_LOCAL_MACHINE value when you remove the file that acted as a shell replacement.
There are obviously several ways of getting around this using the command prompt, but my preferred one would be:
- Open the command prompt using the Cmd button in the Tech Suppport Scammers screen
- In the command prompt use the command taskmgr to start the TaskManager and kill the process called Productkeyupdate.exe
- In the command prompt use the command explorer to open a file browser window and delete the file Productkeyupdate.exe
- In the command prompt use the command shutdown –r to reboot the computer back into its normal state.
- Download and run Malwarebytes Anti-Malware to clean out the leftovers.
If you already have Malwarebytes Anti-Malware installed it’s even easier:
- Open the command prompt using the Cmd button in the Tech Suppport Scammers screen
- In the command prompt use the command explore to open a file browser window and navigate to the folder %ProgramFiles%Malwarebytes Anti-MalwareChameleonWindows and double-click the file iexplore.exe to start Chameleon.
- Then follow the instructions on the screen and the infection will be fully removed
File details
Md5 of the installer: a9e5af63d548847d26b07e1f4983389d
Md5 of the Productkeyupdate.exe c52203064f03caecb3f54567667b15b9
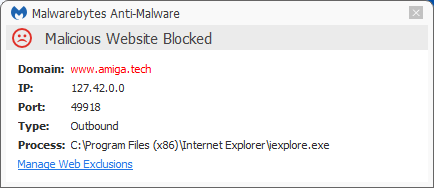
The Malicious Website Protection component of Malwarebytes Anti-Malware Premium blocks the site amiga[dot]tech.
And the Malware Protection component blocks the execution of the installer.
An elaborate and illustrated removal guide (with or without Malwarebytes Ant-Malware installed) for this infection can be found on our forums.
Summary
We looked at another Tech Support Scam using scare tactics to lure victims into calling their phone number. The method is a bit different, but the end-goal is the same. Take the money and run. So save yourself the hassle and get protected.
Pieter Arntz