Malvertising isn’t only used to infect users via drive-by downloads or to deceitfully push fake software updates. A campaign currently going on via the TrafficHolder adult ad platform leverages the promise of raunchy videos to lure people into ad fraud.
The trick is simple and yet effective. While browsing, users are automatically redirected to what appears to be YouTube for adult content. The page looks completely normal, except for the fact that it is a giant image slapped across an actual ‘normal’ WordPress website.
To the naked eye the large JPEG or GIF looks legit, and curious visitors may me tempted to push the Play button to watch the saucy movie. Rather than playing any content, this click is used to launch a real and paid advert via Google’s DoubleClick. This technique referred to as ‘clickjacking’ is very popular and can take different forms while the end goal remains to generate legitimate-looking clicks on adverts.
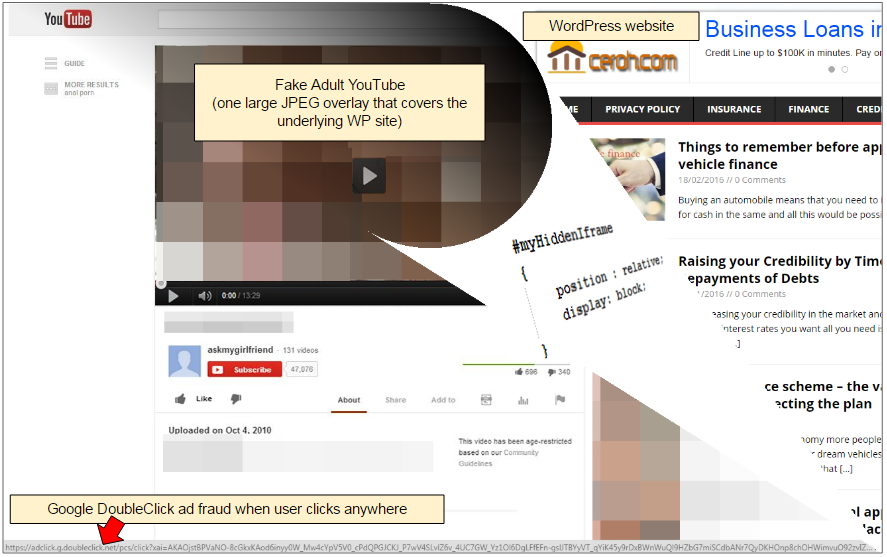
The crooks are using hundreds of what appear to be bogus (insurance, loans and other scams) WordPress sites to carry out this fraudulent scheme. A simple layer is added on top of the page to give this optical illusion. JavaScript code is able to track mouse movements and knows if the user has actually clicked on the advert.
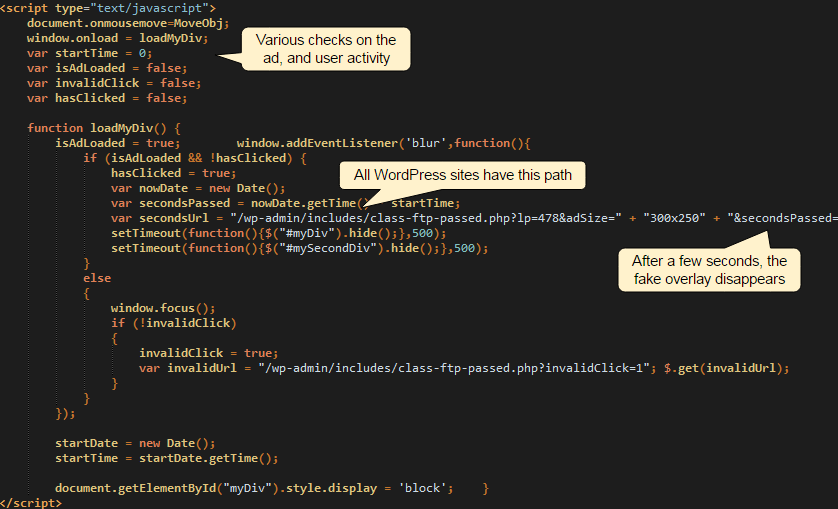
The fake adult image (which covers the whole page) is dynamically generated on the fly and a new one is retrieved randomly from a remote server (5.39.99.215):
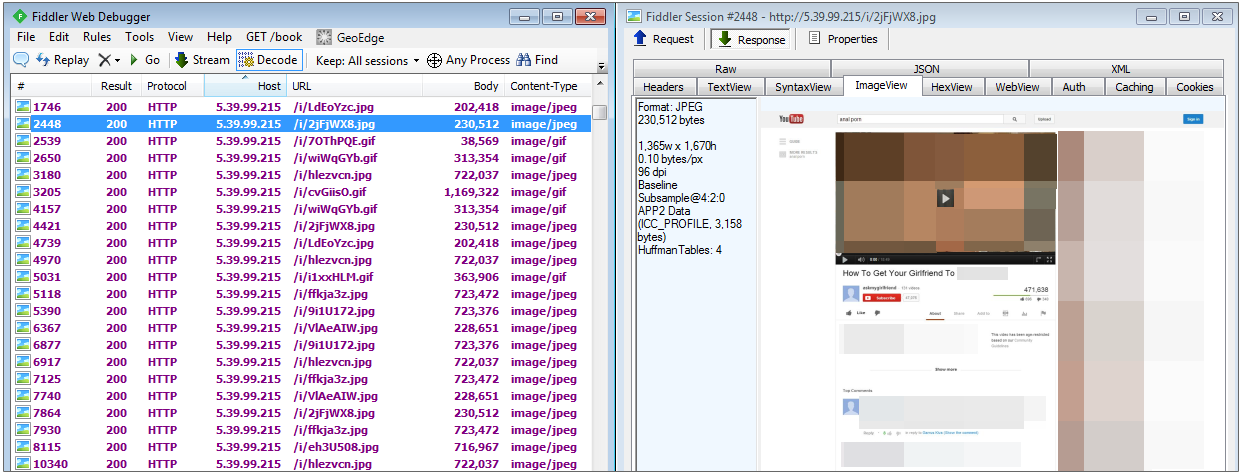
Interestingly, that image will disappear after a few seconds of inactivity to reveal the actual underlying WordPress site. The majority of the sites we found were highly suspicious and most likely used for hosting various other spammy content.
When users click to play the bogus video, their action triggers the ad fraud component of this scam by abusing Google’s DoubleClick, as seen in the traffic capture below:
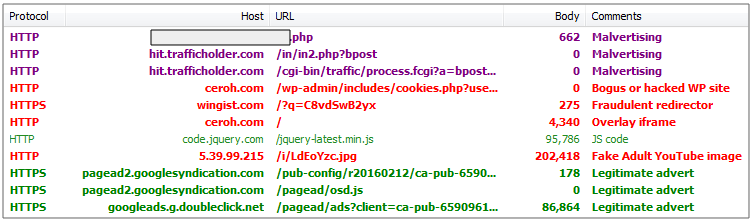
In this particular malvertising instance, users are not put at risk with malicious code, they are simply being duped so that the crooks behind this can generate ad money for each click. However, we have also observed redirections to exploit kits via the same ad platform (TrafficHolder) so you should be extra vigilant and use a proactive line of defence such as exploit protection to avoid getting infected.
We have reported this ad fraud to Google and will keep monitoring the situation as one can expect those rogue actors to come up with a different plan to monetize low quality traffic.










