Our CEO, Marcin Kleczynski, recently announced that Malwarebytes will get tougher on PUPs. PUPs, or potentially unwanted programs, are some of the hardest to classify since they lay in a realm between good and bad. Although most PUPs lean more towards the bad side and should be removed, there are some that aren’t that simple.
Speaking for us mobile researchers, we sometimes classify apps in order to warn users of its presence because of its potential harm, but leave it up to the users’ discretion to remove. This is the case when it comes to a subcategory of PUPs called monitors.
Monitoring apps are those that can be great tools if you lose your phone, but could also be easily used to spy on an unsuspecting target. To show exactly what we are talking about, let’s look at a monitor app found in the Google Play store named Android Lost.
Android Lost
Android Lost is an app that lets users remotely control a mobile device via their website, androidlost.com, or through SMS messages sent to the device. To send commands via their website, one must log in or register using a Google account. This same account must also be an active account on the device you like to control. Here is a list of just some of the features you can do remotely:
- Sound an alarm on the mobile device for up to two minutes
- Make the mobile device vibrate for up to twenty seconds
- Send a GPS location pinpointed on a map of the mobile device
- Option to send location when the power is low on the device
- Take and send a picture from either the front or rear camera
- Take a picture with front camera whenever a wrong pin is entered
- Send a popup message to the mobile device that has a “OK” confirmation button that if pressed will take a picture with the front camera
- Get up to the last 50 SMS messages that have been sent and received from the mobile device
- Option to get only unread messages
- Get a calling history list of up to last 50 items
- Get browser history of last 20 sites visited
- Using the mobile devices mic, record up to an hour of sound and send a saved sound file
- Put a message on the mobile device that overlays everything else on the screen
- Enable/Disable features on the phone such as sound, Bluetooth, GPS, and Wi-Fi
- Get information on the mobile device that contains personal information such as email accounts used, phone number, IP address being used, and a long list of other information
- Send a text to speech message that makes the mobile device talk (extra creepy)
- Send a command to lock the mobile device (requires admin rights)
- Send a command to unlock the mobile device (requires admin rights)
- Send a command to erase the SD card (amazingly, does NOT require admin rights)
- Send a command to wipe the mobile device (requires admin rights)
- Backup content from:
- SMS inbox
- Contacts
- Audio files
- Photos (to an FTP server)
All the data gathered from the mobile device is encrypted and stored on a remote server. The data can be viewed via the Android Lost website and is stored for seven days.
Once installed on a mobile device, it hides its presence by using a generic icon called “Personal Notes”. There is even an option via a command from the Android Lost website to not display an icon at all. The developers reasoning behind such elusive ways is to hide its presence from the thief that stole your device.

Within the Android Lost app, you can request administrator rights, see what security levels that have been set on the device (which one cannot change within the app itself), buy the premium version, and a couple other features.
Our stance on monitor apps
From time to time, our support team gets asked why we classify Android Lost and other monitor apps like it. We have addressed this in a blog we published two years ago entitled, Spyware installed on Android devices to stalk domestic abuse victims. Monitor apps share much of the same features as the more threatening category, spyware. Both have a potential to be used to spy on unsuspecting victims; therefore, our stance is that users need to know about their presence.
Whitelist monitor apps with ease
If you are someone who knowingly installed one of these monitoring apps on your mobile device for its capabilities in the event it is lost or stolen and are annoyed Malwarebytes for Android is detecting it, whitelisting is an easy solution.
If our mobile product is already installed on the mobile device, you will see a popup when the detected monitoring app is first installed. Select the “Add to Whitelist” option, and you won’t be bothered about this app again.
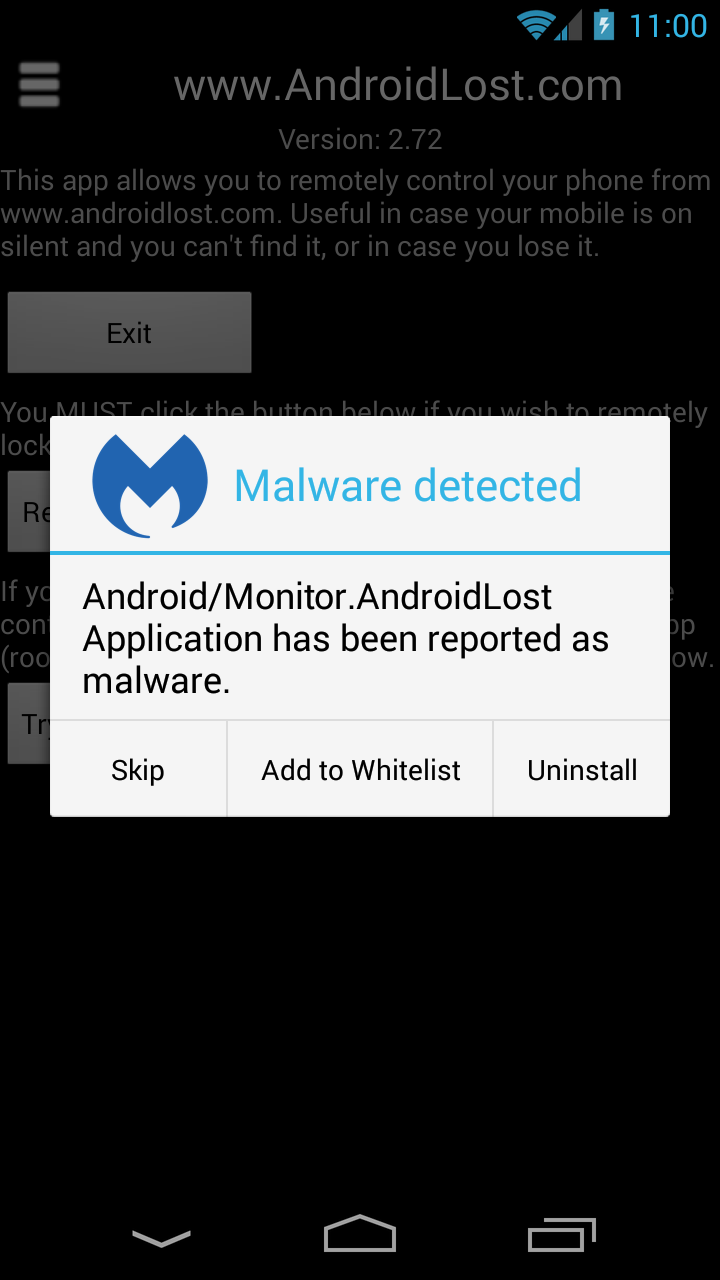
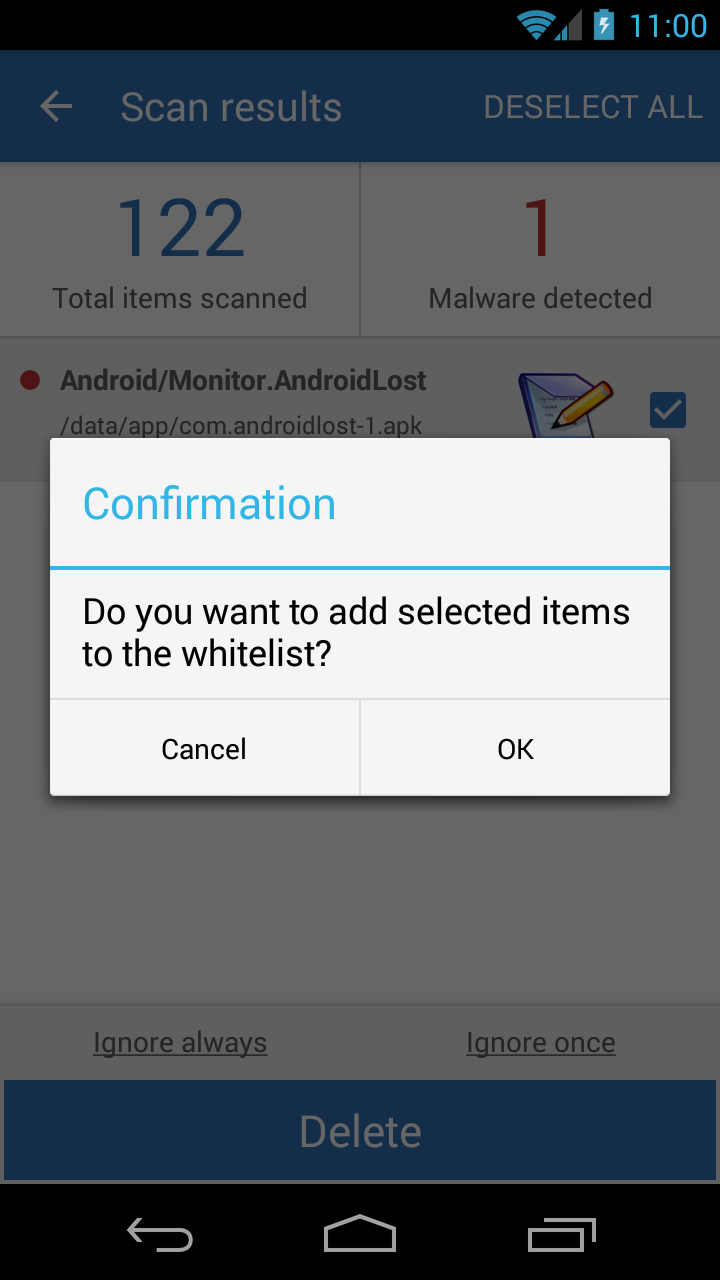
If you have a monitor app already installed on your mobile device before installing Malwarebytes Anti-Malware Mobile, and it was found during a scan, that’s easy, too. Just click “Ignore always”, and confirm you want to add it to the whitelist.
View and remove whitelisted items
If you suspect a monitoring app has been installed on your mobile device unknowingly, but Malwarebytes Anti-Malware Mobile isn’t detecting it, then it’s a good idea to check the whitelist.
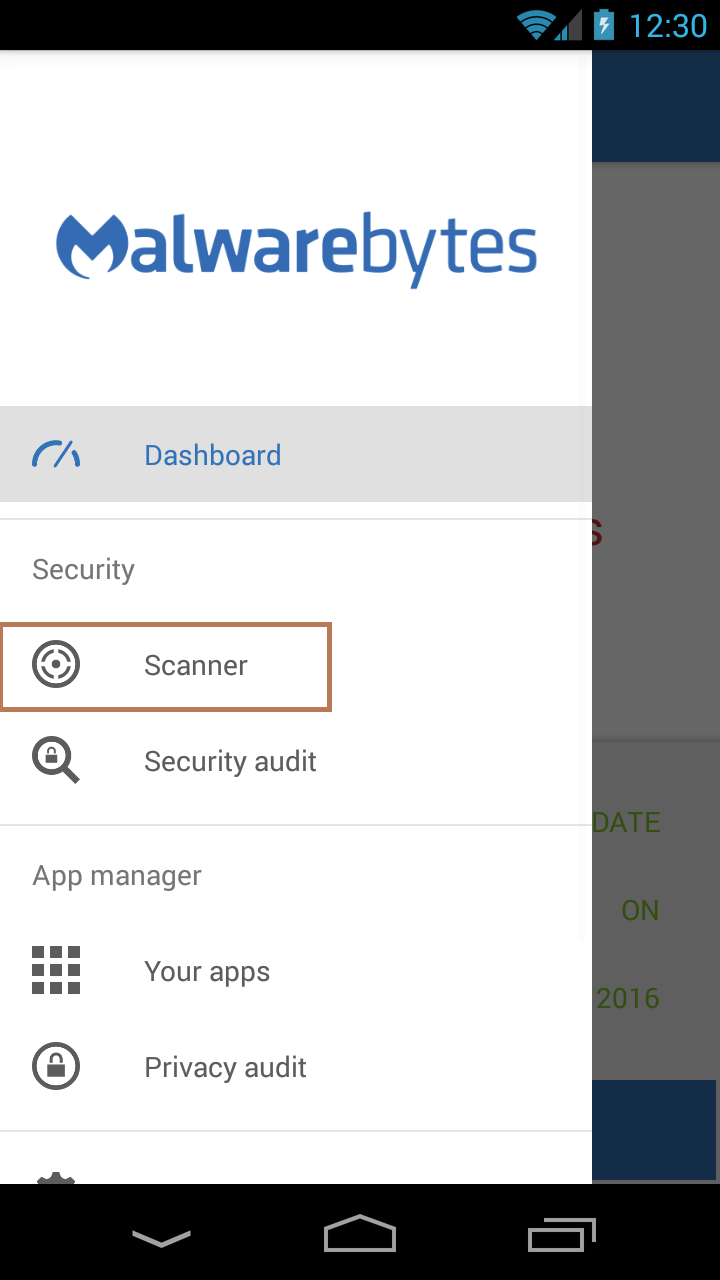
Simply open our app and from the menu drop-down, select “Scanner”. From there, you will see a list icon in the top-right corner of the screen; click it to open the whitelist.
“>
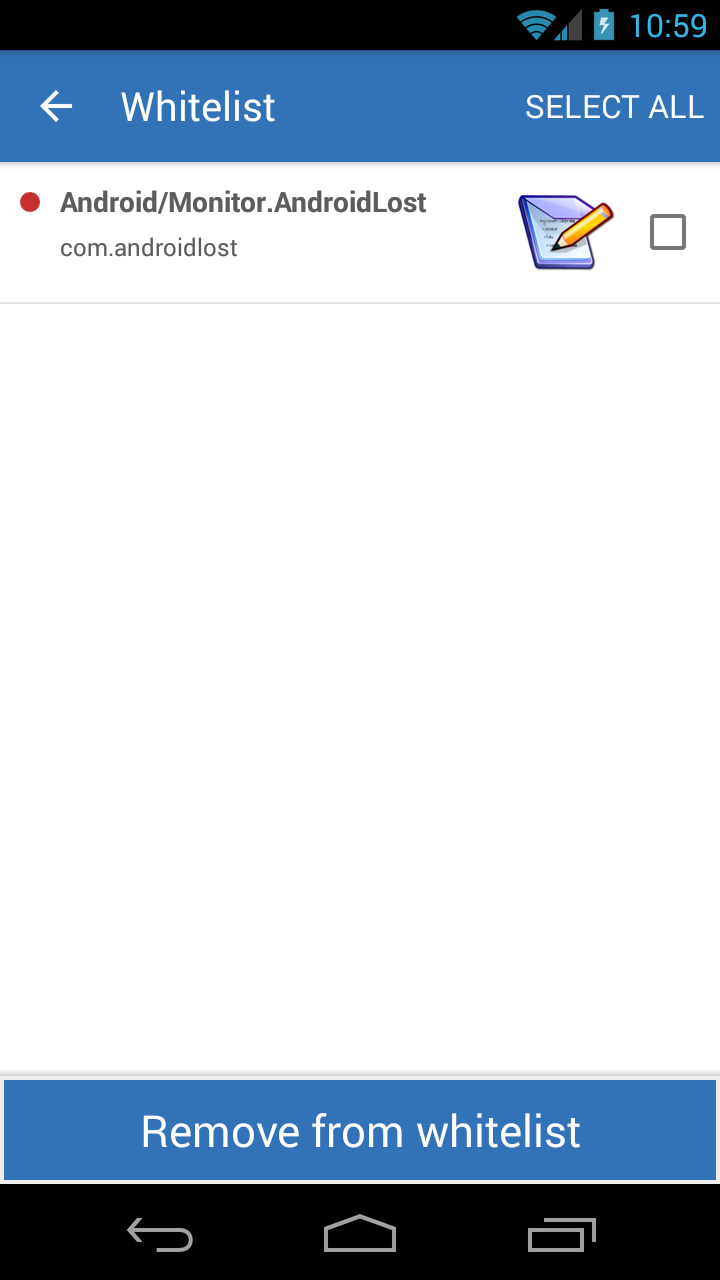
From here, you can see what apps are in the whitelist and select any you would like to remove. All removed whitelisted items shows up in the next scan.
An uneasy feeling
Although developers of monitor apps hide behind claims of protecting users against device theft, you can’t ignore their high potential for acts of spying/stalking. Although spyware is considered more aggressive, the ease of which monitor apps can be installed from Google Play leaves me with an uneasy feeling. At least with spyware, you must take extra steps to install it from the developers website, which could leave users thinking twice about what they are installing.
As with many things in life, it is not my place to say what things users should or should not use based solely on the their potential for harm. Therefore, my dear readers, I will leave the decision up to you. If you do decide to use such apps, I hope it is for their intended purposes in cases of lost/stolen mobile devices and not for purposes of spying/stalking on unsuspecting victims.










