We have found members of the Elex family to create an extra Firefox profile and wrote about it on our blog in a post called GsearchFinder hijackers add extra Firefox profile. Now they took on the task of doing the same for Chrome (and succeeded). They copy some settings from your current profile to create the new profile and give it a natural “feel”.
Background
Youndoo is named after the searchpage it tries to get its’ victims to use.
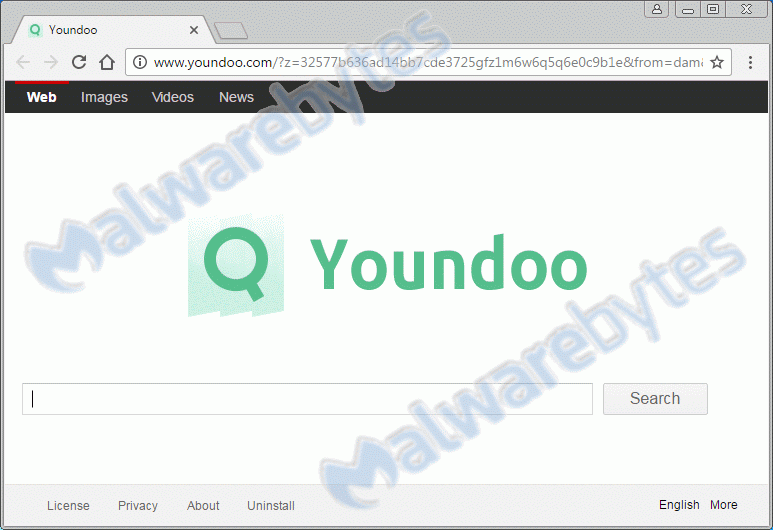
If there is one thing we must admit that this is a resourceful lot. They have come up with some very inventive methods to get us to use their search engine(s). Maybe if they had put all that creative power into improving said search engine they might have taken over the market lead by now. (hint, hint)
To name a few examples of their making:
- Qone8 – hijacking browser shortcuts
- HohoSearch – an extra Firefox profile
- The first Youndoo – using ShellExecuteHooks
- YesSearches – altered browser shortcuts, services, and Scheduled Tasks
The extra Chrome profile
This hijacker uses some other methods, but we will focus on the new Google Chrome profile here. If you are used to logging in to Chrome with your Google account you will see something like this under Settings:
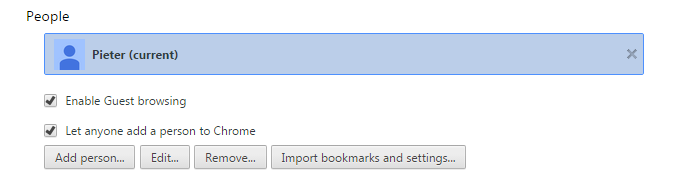
Under “People” you will see the currently active account. If you are not logged in, the displayed account name will be “Person1” and the icon will be gray and not blue.
But, if you have been affected by this hijacker, you will see this instead:
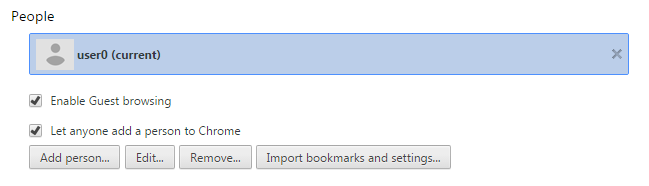
A gray icon with the profile name “user0” is displayed as the current user. Your extensions and history were copied to this account, but your start-page has been changed to
www.youndoo.com.
You will also find that your “Home Button” brings you to the same page and that Youndoo is now your default search engine in Chrome. But even changing all these settings manually will not prevent the Youndoo search site from opening when you start Chrome. Even removing the new profile will not undo that. But after editing the settings and a reboot, that part is cleared up. This is not a total removal though, we urgently revise to do a full Threat Scan with Malwarebytes Anti-Malware if you are dealing with this infection, since there are usually also a Scheduled Task and a service active on affected systems.
A full removal guide can be found on our forums, where you will notice most of the detections are done as PUP.Optional.FakeCHRProfile to get rid of the fake Chrome profile.
File properties
SHA1 dam_ay.exe a54ca8156ad9de6ae81231ba934284dffeb8d730
Malwarebytes Anti-Malware detected this installer as PUP.Optional.YesSearches even before it was released.
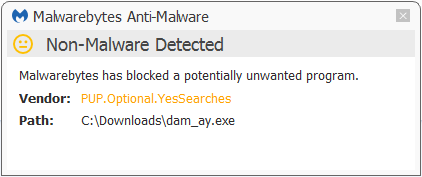
As often this file was offered as an installer for a VLC player.
Stay safe and get yourself protected.
Pieter











